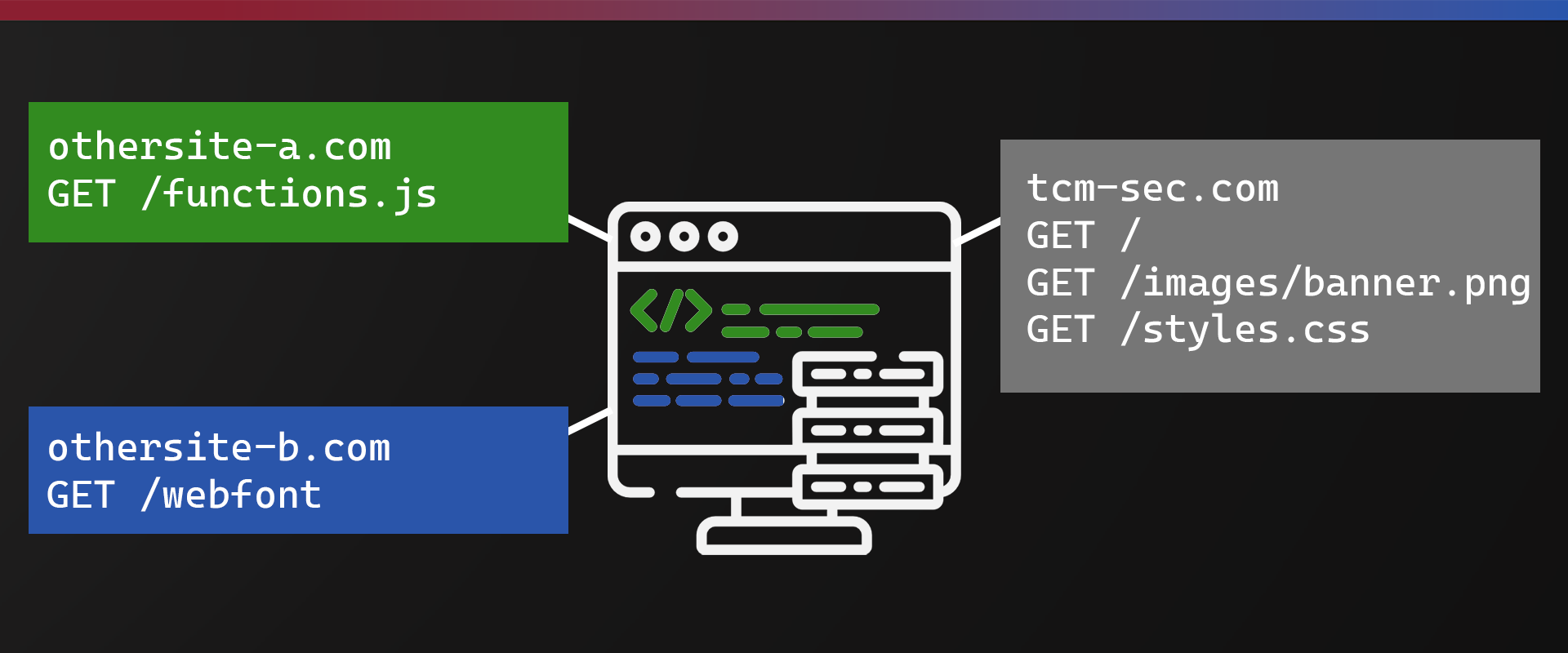
Most modern web applications load resources such as fonts and JavaScript from other domains or a CDN. CORS is a security feature that prevents unauthorized access to web resources. However, depending on how it’s implemented CORS can still be attacked. Let’s first take a quick look at CORS and then how CORS attacks work.
What is CORS?
Cross-Origin Resource Sharing (CORS) is an HTTP-header based mechanism that allows a server to indicate any origins (domain, scheme, or port) other than its own from which a browser should permit loading resources. CORS also relies on a mechanism by which browsers make a “preflight” request to the server hosting the cross-origin resource, in order to check that the server will permit the actual request. In that preflight, the browser sends headers that indicate the HTTP method and headers that will be used in the actual request.
Cross-Origin Resource Sharing (CORS)
CORS headers:
- Access-Control-Allow-Origin
- Access-Control-Allow-Credentials
CORS Misconfigurations and Vulnerabilities
If an application has misconfigurations or is too lenient with CORS, it can lead to vulnerabilities.
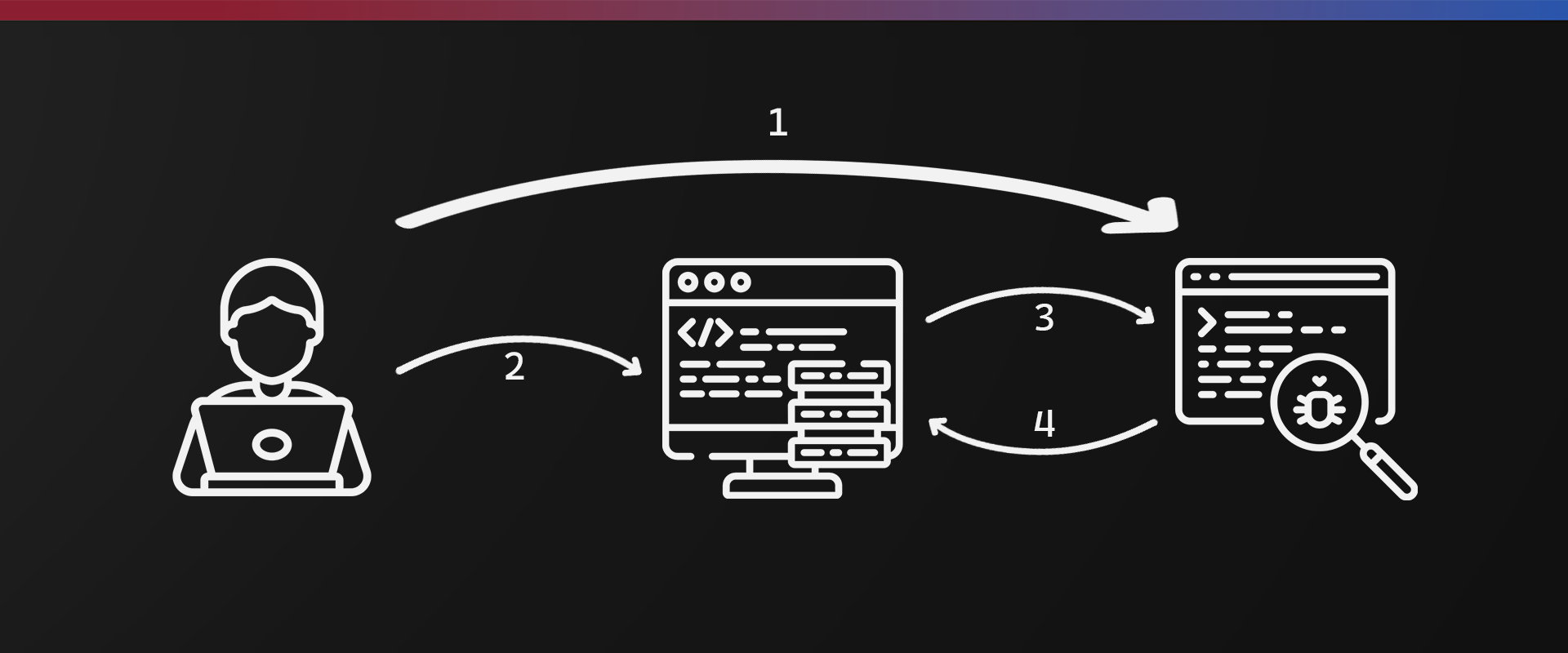
For example, in the scenario below:
- A user accesses a web application and logs in
- After a while, they access a malicious site
- This malicious site sends requests to the original application that the user accessed
- The original site has misconfigured CORS. It accepts the request and since it has Access-Control-Allow-Credentials set to True so the request includes the user’s cookies, and then responds
In this case, sensitive data is leaked.
Cross-Origin Resource Sharing (CORS)
Most modern web applications require resources from many domains and since Access-Control-Allow-Origin only takes three options, without the ability to pass a list or multiple domains, generating the header value dynamically can lead to issues.
Access-Control-Allow-Origin: * Access-Control-Allow-Origin: <origin> Access-Control-Allow-Origin: null
Setting Access-Control-Allow-Origin Header from Origin Header
One mistake is using the Origin header to populate the Access-Control-Allow-Origin header.
If we take the Origin: https://tcmdev.tcmsecurity.com header value from a request and simply reflect it in the response header so it reads Access-Control-Allow-Origin: https://tcmdev.tcmsecurity.com we are allowing any origin to access the resource.
Origin Header Allow-List Mistakes
If we try to maintain an allow-list to ensure that only approved origins are reflected into the Access-Control-Allow-Origin header, mistakes can be made when list items are not properly defined.
For example, the allow-list may contain the entry tcm-sec.com. This simple entry may be abused by passing:
usingaprefixdomaintcm-sec.com tcm-sec.com.usinganevilsubdomain.com
There are other issues that can arise, and as with many misconfigurations, there is a seemingly endless pit of mistakes to make.
Preventing CORS
Of course, any resource that returns sensitive information should be properly configured and protected. All of the vulnerabilities described above are misconfigurations. Therefore, ensuring that a proper allow-list without exploitable wildcard entries as well as validation of the Origin header is vital. We should also avoid using null when passing the header Access-Control-Allow-Origin.

About the Author: Alex Olsen
Alex is a Web Application Security specialist with experience working across multiple sectors, from single-developer applications all the way up to enterprise web apps with tens of millions of users. He enjoys building applications almost as much as breaking them and has spent many years supporting the shift-left movement by teaching developers, infrastructure engineers, architects, and anyone who would listen about cybersecurity. He created many of the web hacking courses in TCM Security Academy, as well as the PJWT and PWPT certifications.
Alex holds a Master’s Degree in Computing, as well as the PNPT, CEH, and OSCP certifications.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

