What separates a good guy (white hat) from a bad guy (black hat)?
The bad guy will either hack you for profit or hold your information for ransom in exchange for monetary gain or brand damage. The good guy will tell you what is insecure about your company, and most importantly, how to fix it.
A penetration testing report is the ultimate product that is delivered by a penetration tester or ethical hacker.
A penetration test report can come in many shapes and sizes as well as vary in the amount of detail provided to the client. Some penetration testing firms may simply provide scan results while others may provide highly detailed reports that can be over one hundred pages long. The length and depth of the report is in the eye of the beholder.
This blog post explains what TCM Security provides to our penetration testing clients at the end of an engagement. If you want to follow along with this article, understand what a penetration test report looks like, or want a template to start from when writing your own reports, download our sample penetration test report.
What is Included in a Penetration Test Report from TCM Security?
At TCM Security, we pride ourselves on providing penetration test reports that are easily digestible for our clients. We try to strike a balance between the amount of detail in the report and the clarity of the communication. Keep in mind that when a report is given to a client, it is usually handed to multiple parties in the client’s organization. In addition to the top leaders in the security organization, system administrators and developers of the systems being tested are likely to read the report as well. For that reason, a penetration test report should be detailed enough to demonstrate the issues and how to fix them, but also high-level enough that an executive is not overwhelmed in the decision-making process. We also provide supporting documents as shown in the Supplemental Documents section.
There’s no one correct way to write a penetration test report. However, at TCM Security, our penetration test reports consist of the following major parts:
- Cover Page
- Table of Contents
- Confidentiality Statement/Disclaimer
- Contact Information
- Assessment Overview, Types of Assessments Performed and Methodology
- Findings Severity Ratings
- Project Scope and Exclusions
- Allowances
- Executive Summary
- The Findings! 😊
- Supplemental Documentation/Appendixes
Penetration Test Report Walkthrough
Let’s take a walk through every aspect of our pentest reports and why they are important.
Cover Page
Here is a sample title page of our reports at TCM Security. Many testers choose to highly customize the cover page of their reports using flashy art styles that align with their branding. It’s not all aesthetics however. The title page contains important information like the name of the client company, as well as the dates the testing was performed. You may also choose to use version control on the cover if the pentest report goes through multiple editing iterations.

Table of Contents
The next section of the report is the Table of Contents. This easily allows any reader of the report to jump to the sections they are most interested in. Do not overlook the table of contents! As mentioned, many different types of people will be reading the report. Make it as easy as possible for them to navigate. For example, an executive may want to read only the executive summary of the report and trust their team to handle the remediation. Likewise, a developer or system administrator may jump right into the meat and potatoes of each individual finding to begin their remediation efforts. I highly recommend using Microsoft Word’s built-in heading styles to easily build a table of contents as you write the report.

Confidentiality Statement and Contact Information
Although this section of the report may seem mundane, the confidentiality statement defines the legal obligations between the penetration testing firm and their clients. This section of the document spells out what information can be shared between the client and other organizations as well as what TCM Security is allowed to share about the client. Furthermore, the Disclaimer section of the report protects the penetration tester from legal liability if a security vulnerability is introduced after the testing period. Finally, the contact information section of this page serves as a historical record of who performed the assessment as well as who the primary point of contact of the client is at the time of testing. This information is valuable to both parties and helps keep an accurate record of contacts at both organizations.

Assessment Overview
The assessment overview section of our reports outlines when the assessment was performed and the basic methodology utilized by the tester. This section of the report can sometimes be highly customized based on the specific type of test that was performed. For example, as a penetration tester you may be assessing the security of an individual device according to a specific standard such as a STIG or NIST standard. These methodologies and standards should be highlighted in this section of the report when applicable. This section also outlines the basic phases of a penetration test such as planning, discovery, exploitation, and most importantly, reporting.

In addition to the “Assessment Overview” we also include an “Assessment Components” page which explains each type of test that was performed. This specific example shows the outline of our external penetration test but if the client requested more tests (like a test of their wireless network, physical security, etc.) the report would contain additional paragraphs. This report section helps to give the client and executive leadership a summary of what differentiates the types of tests that were performed. Summaries like this help the reader understand what aspects of their environment were tested.

Finding Severity Ratings
The next section of the report is the finding severity rating chart. This is one of the most widely varying aspects of penetration tests between penetration testing firms. Every firm creates their own scale and naming convention. Some firms may choose Critical, High, Medium and Low for their severity categories, while others may choose entirely different naming conventions.The naming conventions and risk names are truly in the eye of the beholder! The image below shows the table and the severity ratings used by TCM Security:
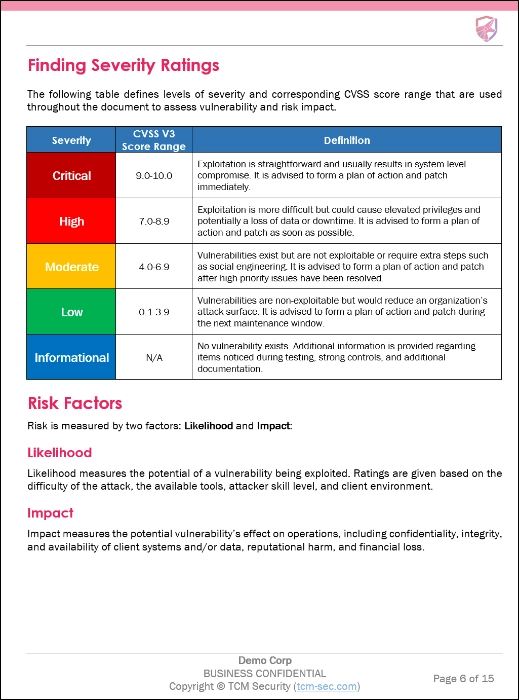
One of the most important aspects of TCM Security’s reporting is the freedom to include “Informational” findings in the report. Informational findings are important to us because it is an opportunity to give the client some credit for things they have done well. Here is an example of what we call a “positive finding” from a recent report:
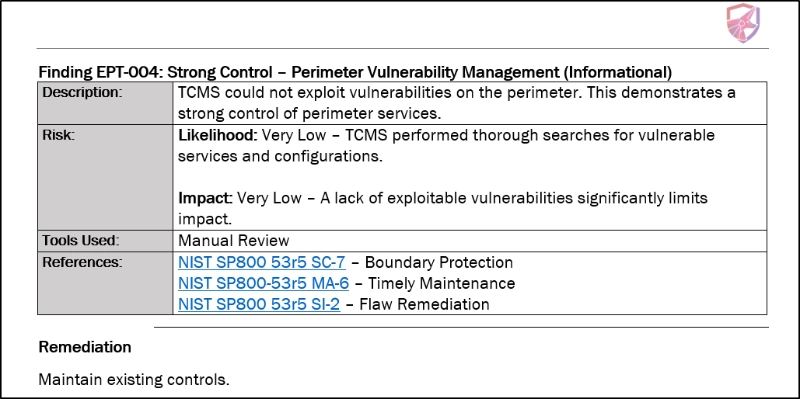
The client had an extremely small external attack surface, and all their software and exposed services were patched to the highest possible level. This client did an excellent job reducing the number of vulnerabilities in their environment, so this was an opportunity to call them out for a job well done.
We also use the informational findings to address issues that have a negligible impact on security, but may be a bug or other issue we discovered during the engagement. For example, if the user interface (UI) of a web application broke during testing we can make the client aware of the issue without negatively affecting their report. It’s important to inform the client of issues that we believe may have a negative impact on customers even if it’s not a security issue. This helps to build trust and show that we genuinely care about the client’s ability to do business!
Project Scope and Exclusions
The next page of the report is an extremely important piece of documentation. This section of the report shows the IP addresses or hostnames that were part of the project scope. As penetration testers it is important that we do not attack targets that are not in scope. The scope of the engagement should be agreed upon and signed in a separate document called a “Rules of Engagement” or ROE document. This is a legally binding contract that outlines what the tester is allowed to test, and the scope of the ROE is further reflected in this section of the final report. The Scope exclusion section highlights the types of tests that should not be performed during the engagement. The most common scope exclusion is Denial of Service since we should not cause business disruptions during testing.

Allowances
This page also summarizes the client allowances. An allowance is anything that the client gave you as information or access that a normal attacker would not have. Allowances include information like credentials, accounts with varying roles, firewall rules changes, network diagrams or anything that benefitted you during the engagement. This should always be documented in your penetration test reports to show any access or information that was granted by the client.
Executive Summary
The executive summary is the first section of the report where we provide an overview of the issues identified during testing. This page is a quick summary of the entire engagement within one or two pages. The executive summary includes the dates the engagement took place as well as a brief summary of the scope and testing performed. The executive summary gives a sentence-by-sentence summary of each finding discovered during the engagement. The summary also links to the findings so a technical individual can easily hop to that section.
The most important aspect of this section of the report is the Key Strengths and Weaknesses section. At TCM Security, every executive summary includes a bulleted list of strengths and weaknesses we discovered. It’s easy to focus on the negative findings, but we like to always give the client an overview of how their security program is succeeding.

The Findings
Finally, we have come to the part of the report that you are probably the most excited for! The findings!
At TCM Security, we provide a quick color-coded scorecard summary of the findings from the report as well as a one sentence remediation recommendation that clients can quickly read to understand how to fix the issue. This scorecard also gives executives a quick overview of the number of findings in each criticality that were discovered.

Here is an example finding from this report:
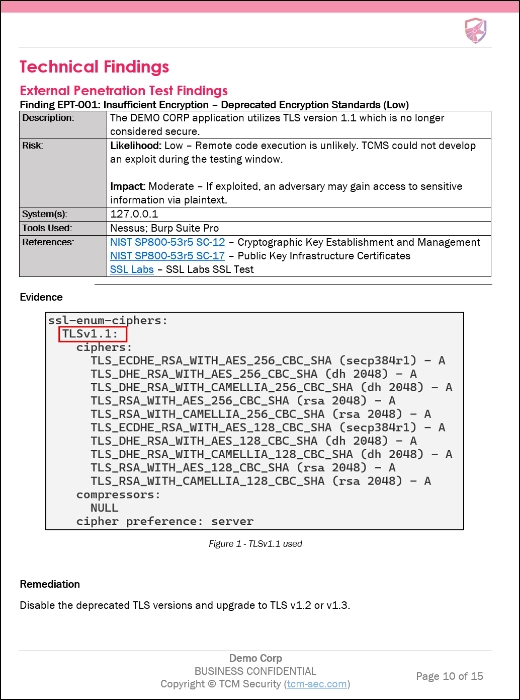
This finding has a few parts that are important. No matter which penetration testing firm you utilize most findings are likely to include the following:
- Title
- Criticality: in this case: Low.
- Description: A brief or long form description of the vulnerability and what it affects.
- Risk: A summary of why the tester assigned the given criticality to the finding.
- Affected System(s): The IP address, host, or asset where the finding was discovered.
- Tools Used: The tool or method that found the vulnerability.
- References: Any documentation or resources that will either help the client to fix the issue, identify further instances of the issue, or to give any background context to the issue.
- Evidence: Evidence can be in the form of screenshots as shown in this finding, or sometimes evidence will be in the form of an attack narrative with several pictures and a few supporting paragraphs of text.
- Remediation Recommendations: As penetration testers, we need to tell clients how to fix the issue, otherwise we are just identifying problems without a resolution.
Some penetration testers may also choose to include additional information for each finding. A few common examples are:
- Steps to Reproduce: The step-by-step documentation to discover the issue.
- CVSS Score: A strict calculation of the vulnerability’s risk created by NIAC.
- Regulatory Compliance Details: If the client is required to meet regulatory requirements, it may be relevant to tie the finding back to a specific violation or missed requirement.
Supplemental Documentation
At TCM Security, we provide supplemental documents alongside our penetration test reports. These documents are:
- Letter of Attestation: A formal letter that outlines the services that were performed, when they were performed, and the number of findings discovered. Many clients use this document to attest to regulatory requirements which state third-party penetration testing must be performed once per year.
- Executive Summary: A one-page document that explains the assessments performed as well as the number of findings in each assessment type.
- Findings List: A summary of the findings in CSV or Excel format
Finally, we pride ourselves on providing our clients with the outputs of tools as well as allowing clients to shadow engagements alongside us. We believe in sharing as much information with clients as possible to help them become better defenders. Because of this, we also provide tool recommendations and the outputs from our tools such as:
- Nessus Reports
- PingCastle and Bloodhound Reports
- Social Engineering Call Logs
- Breached Passwords
- Password Audit Results
- Burp Suite Results
Providing this level of granularity and detail allows clients to dive deeply into their environment and fix root issues, and most importantly, learn to evaluate their environment for themselves. We want to empower clients to defend and improve and put the power into their hands to identify issues before the bad guys do.
Sample Penetration Testing Reports
You can find a sample report on our website at: TCM Security Sample Report or on Heath Adams’ github page.
Like we mentioned, there are many different ways to write a pentest report. One of my favorite resources is pentestreports.com. You can also find many bug bounty write ups at Pentesterland.
Conclusion
If you’d like to know more about TCM Security’s penetration testing services, please reach out to us using the form below.

About the Author: Aaron Wilson
Aaron is a passionate security professional with experience in the Fortune 50. He is the Red Team Lead at TCM Security, responsible for leading the penetration testing and consulting teams. He is also an avid Capture the Flag Creator and has published multiple rooms on TryHackMe. Aaron is also CEO and Founder of the Wilson Security Group and publishes videos on YouTube on security topics and cybersecurity certification reviews.
Aaron holds certifications such as the eMAPT, CISSP, eCPPTv2, eWAPTv2, CEH, and eJPT certifications among others. He holds a bachelor’s degree in Security and Risk Analysis from Penn State University as well as a Master’s in Information Assurance and Cybersecurity from Western Governor’s University (WGU).
Follow Aaron on Social Media:
LinkedIn – https://www.linkedin.com/in/wilson-security
YouTube – https://www.youtube.com/c/WilsonSecurityGroup
TryHackMe Hacker Methodology – https://tryhackme.com/r/room/hackermethodology
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

