Introduction
Many people considering a cybersecurity career often gravitate towards red team operations and penetration testing because the media portrays them in an exciting and flattering light. However, it’s important to recognize that businesses often place even greater importance on the defensive side of security operations. Organizations historically relied on, and will continue to require, skilled analysts and engineers to monitor the infrastructure, build out detection capabilities, and ultimately respond to the inevitable—incidents.
Additionally, while not always the case, individuals are more likely to break into the industry through a blue-team or defensive role due to their higher demand and prevalence of entry-level positions.
Consequently, it’s important to understand the various roles and responsibilities that exist within defensive operations, with the SOC Analyst standing out as one of the most prominent. But what exactly does a SOC Analyst do? And what does the day-to-day work and career progression path look like for someone working in a SOC? Interestingly, the answer is not as straightforward as one might think.
Understanding the Security Operations Center (SOC)
To properly understand the role of a SOC Analyst, we must first familiarize ourselves with the concept of the SOC itself. A SOC, or a Security Operations Center, is a centralized unit within an organization dedicated to managing security issues, incidents, and events. This definition purposely covers a broad spectrum, because the responsibilities and priorities of a SOC can vary significantly among different organizations based on factors including their specific industry, leadership, or budget.
However, a SOC typically strives to build out several proactive and reactive capabilities. These include continuous monitoring, threat detection, incident response, and security management. These functions are crucial for maintaining the confidentiality, integrity, and availability of the organization’s assets and data.
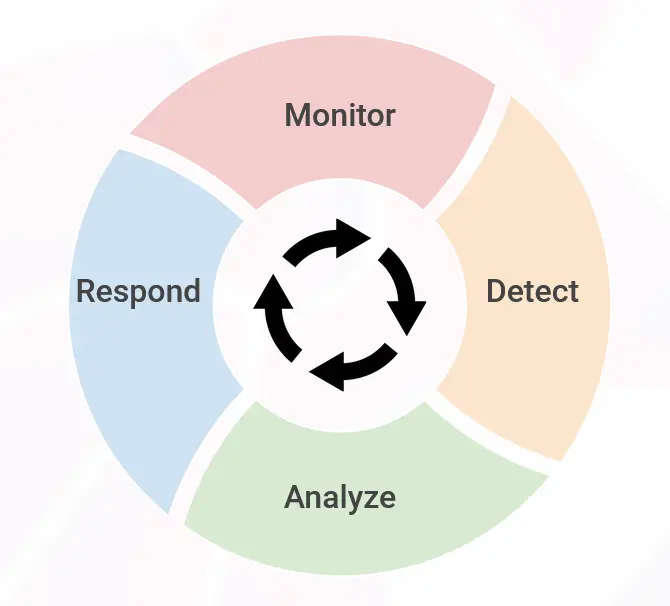
The main functions of a Security Operations Center can be generally categorized into four pillars:
1) Security Monitoring
When people think about a Security Operations Center (SOC), monitoring is often the first function that comes to mind, as it forms the core of the SOC’s effective operation.
As a quick aside, common depictions of a SOC typically include rows of analysts sitting shoulder to shoulder, with hundreds of monitors and screens displaying flashing graphs and alerts. However, with the recent rise of remote work and the interconnected nature of IT operations, more SOCs are becoming virtualized and geographically distributed. The advancement of cloud solutions, virtual private networks (VPNs), and team collaboration platforms enables many SOC teams to operate from anywhere in the world, without the need for a centralized physical location.
SOC teams deploy and use various data aggregation tools like Security Information and Event Management (SIEM) systems to ingest data from servers, endpoints, and other assets to maintain real-time visibility into the organization’s IT infrastructure. In order to monitor effectively, a SOC typically deploys endpoint agents, sets up passive detection or inline prevention systems, configures logging forwards or uses protocol-specific logging mechanisms like syslog to ensue all of this telemetry is collected, aggregated, and stored in a central location for analysis.
For example, to track file access, processes, registry changes, or network activity on endpoints, a SOC can deploy an EDR (Endpoint Detection and Response) agent. This agent collects and aggregates telemetry data, providing detailed visibility into endpoint activities for security analysis and incident response purposes.
2) Incident Detection
Once monitoring solutions are in place, events are forwarded to a centralized logging system and fine-tuned to identify anomalies, policy violations, and indicators of compromise (IOCs) within the data. The goal of detection is to ensure that the SOC is able to effectively identify potential incidents amidst the large volume of collected events. Achieving this involves establishing an effective baseline, leveraging various detection methods, and continuously fine-tuning the detection mechanisms to mitigate false positives.
Continuing the example, suppose a behavior-based detection alert is triggered and forwarded from the EDR solution. The alert indicates that an employee is attempting to access a sensitive file outside of their normal working hours and from an abnormal geographic location.
3) Incident Analysis
When alerts are created, it becomes a SOC Analyst’s job to conduct an investigation and understand the nature, scope, and potential impact of the event. An analyst performs an initial triage to determine the alert’s validity and prioritize the response effort.
The process may involve correlating data from various sources within the SIEM to build a comprehensive view of the incident, examining logs, network traffic, or endpoint data of the affected host, and ultimately trace a potential attacker’s tactics, techniques, and procedures (TTPs).
In the case of the EDR alert example, an analyst would first need to triage and investigate the generated alert to gather more information. This involves reviewing the employee’s access history, IP addresses of recent logins, other activities that occurred on the workstation prior to the alert. The analyst leverages various data points within the environment to determine if the access attempt is malicious or benign.
4) Incident Response
Based on the findings of the analysis, the SOC needs to take decisive actions to contain, mitigate, and remediate the incident by executing an incident response plan. Often, this includes isolating affected systems, temporarily restricting access privileges, resetting credentials, deploying patches, and coordinating with internal or external stakeholders.
For example, after a thorough analysis, a SOC Analyst finds that the employee’s access attempt was malicious. Consequently, an incident response plan would need to be initiated to reset the employee’s credentials, audit the accessed data, notify affected parties, and implement measures to prevent similar incidents in the future. Additionally, a deeper investigation into the root cause would need to be performed to understand how the endpoint was compromised.
Who is a SOC Analyst?
The challenge in defining the role of a SOC Analyst stems from the variety of roles and responsibilities for these positions within the field. This diversity leads to confusion about the daily tasks of analysts. However, SOC Analysts can generally be categorized into different levels or tiers, each with distinct priorities, responsibilities, and expertise.
It’s important to note that not all organizations used the tiered model described below. Some may choose to forgo the tiered model entirely, and instead, facilitate a more collaborative and cross-functional approach. Valid arguments support either approach, and the choice depends entirely on the organization.
Tier 1 SOC Analyst
Tier 1 SOC Analysts are the front-line analysts involved in the continuous monitoring of the organization’s assets, and are sometimes referred to as “triage” analysts. Fundamentally, a Tier 1 analyst is tasked with analyzing the events and alerts generated by security tools such as a SIEM, an EDR, or various detection and prevention systems.
As someone entering the industry, you may see the word “triage” frequently without fully understanding its meaning. In a SOC environment, triage refers to the process of quickly assessing and prioritizing security alerts or incidents to determine the appropriate course of action.
“Triage” is often used in a medical context. For example, in hospital emergency rooms, medical staff assess and triage patients to prioritize treatment based on the severity of their condition. Within a SOC, analysts evaluate security alerts to prioritize response efforts or escalate them to more experienced analysts or incident responders.
Due to the nature of the field, a SOC must balance competing priorities and time constraints. A good SOC Analyst will learn when to invest their time, which is why effective triage is key.
Tier 2 SOC Analyst
In a typical tiered model, a Tier 2 SOC Analyst is more senior and often fulfills the “incident responder” or “investigator” analyst function. This is a more specialized role in the SOC, as these analysts are more experienced with the SOC’s tooling and are responsible for handling more complex incidents that have been escalated by Tier 1. Often, these types of incidents will require more in-depth investigation or involve a much larger scope within the organization.
Additionally, Tier 2 Analysts will contribute to the incident response function of the organization. They may write standard operating procedures (SOPs) in the form of playbooks and create response workflows to facilitate a coordinated and agile response to security incidents.
Tier 3 SOC Analyst
Lastly, a Tier 3 SOC Analyst is typically the highest level in a SOC before management and specialized roles. In many organizations, it is a more proactive role. Additionally, some SOCs may refer to Tier 3 Analysts as “Threat Hunters.” Again, it’s important to note that not all organizations have the budget and resources to build out a fully functional team using this model.
Tier 3 SOC Analysts are the most senior level analysts that are able to assist Tier 2 with intricate and involved incident response activities. However, unlike the lower tiers, Tier 3 Analysts often have a primary focus on proactively searching for suspicious behavior, ingesting threat intelligence, and performing threat hunting assessments to detect sophisticated threats or vulnerabilities that evade standard detection.
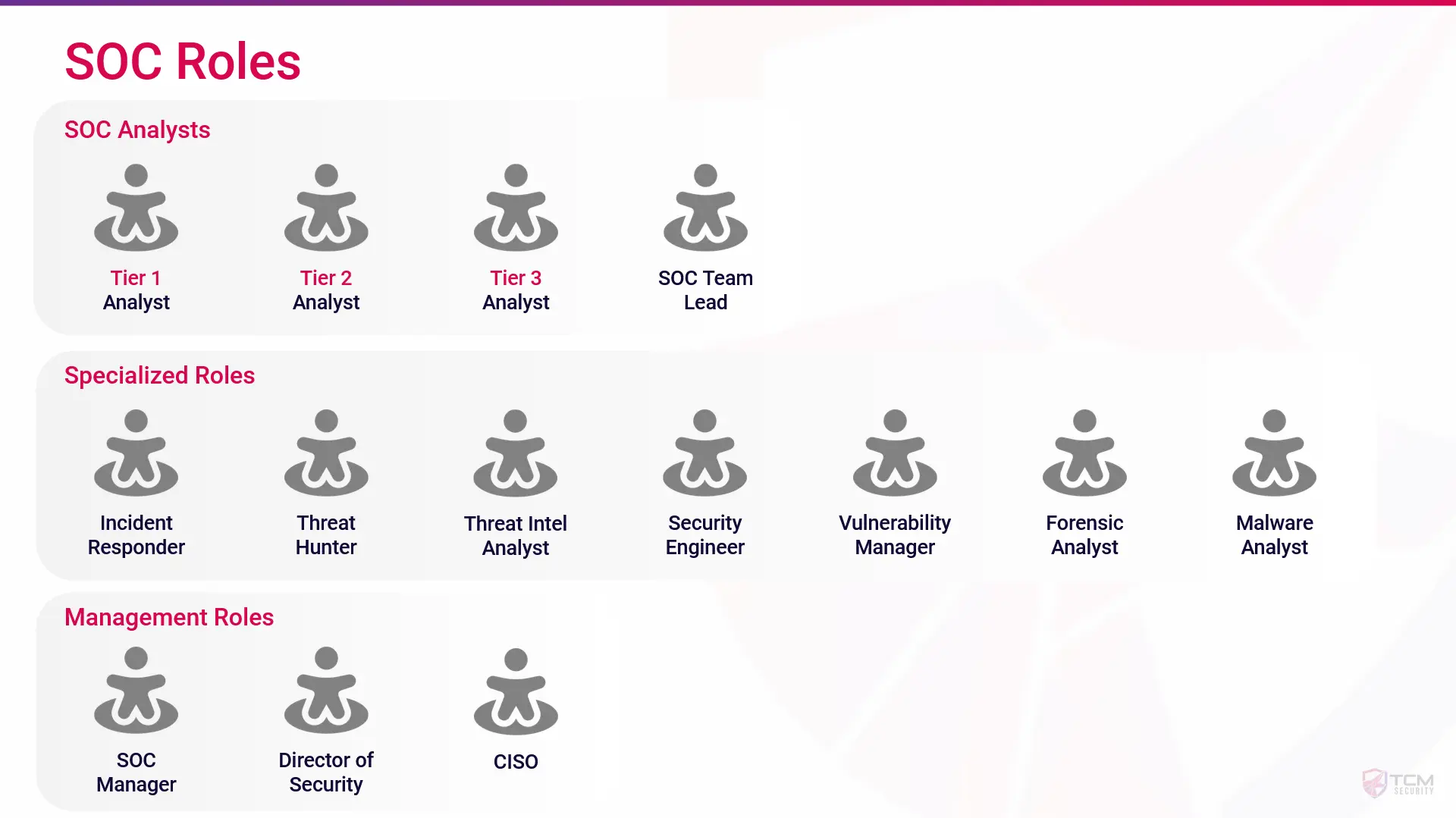
Specialized Roles
Beyond the standard analyst roles, a large SOC may carve out specialized roles and management positions within the team to focus expertise on niche areas and lead the team effectively.
On the management side, a SOC might have a Team Lead responsible for overseeing the day-to-day operations of the analysts, managing workload, and providing guidance for junior analysts. However, sometimes this responsibility is served by a Tier 2 or 3 Analyst. Typically, a SOC will also have a SOC Manager to serve this purpose and to implement strategies, policies, and procedures that align the team’s objectives with organizational goals.
If a SOC is large enough and well-resourced, it might include specialized roles such as an Incident Responder or Threat Hunter to fill reactive and proactive expertise, respectively.
Additional roles in the field can include a Threat Intelligence Analyst to ingest and disseminate actionable intelligence to enhance the team’s detection capabilities. Security Engineers will collaborate to architect, deploy, configure, and actively tune security infrastructure and tooling used within the SOC. Vulnerability Managers, while often falling into the governance, risk management, and compliance (GRC) side of cybersecurity, will collaborate with the SOC and IT teams to detect and remediate security weaknesses and implement patching strategies.
Conclusion
Ultimately, like with many areas of cybersecurity, the roles and responsibilities found within a SOC vary widely between organizations, and no two SOC Analysts will have identical experiences. A typical SOC Analyst will be exposed to and collaborate with many different areas and functions of the team’s defensive operations, making it a dynamic and cross-functional position.
However, as the primary focus of a SOC is built upon the pillars of monitoring, detecting, analyzing, and responding, a SOC Analyst plays a big role in the monitoring and triaging of organizational events and incidents. As SOC Analysts progress their careers, they will encounter numerous opportunities to transition into more advanced roles that integrate incident response or proactive threat hunting functions.
Additionally, working in a SOC will open the door to many additional specialized areas within cybersecurity, making SOC analysis an excellent foundational role for newcomers to the field and individuals looking to gain invaluable experience in blue team operations. If you want to learn more about life as a SOC Analyst, check out my new course, Security Operations (SOC) 101 in TCM Security Academy.
Looking for More SOC Analyst Training?
Join our SOC Level 1 Live Training from January 21-24, 2025! The training features four full days of back-to-back live training and new labs and challenges that cover the foundational skills needed for success in defensive security operations. Plus, the small cohort encourages interactivity and allows you to ask questions and connect with your fellow classmates.

About the Author: Andrew Prince
Andrew is a seasoned and passionate security professional who brings a wealth of experience in areas such as security operations, incident response, threat hunting, vulnerability management, and cloud infrastructure security. With a professional background in development and system administration, Andrew offers a well-rounded perspective on his security strategy. Andrew also navigates both offensive and defensive operations to provide a holistic approach to keeping people, processes, and technology secure. He is also active in developing various Capture the Flag challenges, creating security training, and sharing knowledge through content creation. Andrew created the Security Operations (SOC) 101 course in TCM Security Academy and the Practical SOC Analyst Associate certification.
Social Media Links:
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.