TCM Security regularly conducts web application penetration testing for clients of all shapes and sizes, and these applications are the online face of our enterprises. Being accessible across the Internet as a whole makes websites of any size a potential target, and the necessity of maintaining sound security practices is paramount. Today we will show you the top five most common findings we see when testing client web applications.
No Multi-Factor Authentication
Hands down the most common, critical finding we see when testing web applications is a lack of multi-factor authentication. We generally list this as critical because of the implications of not enforcing MFA, and there being little reason not to implement the functionality in today’s security landscape.
Our users are typically the weakest link in cybersecurity. As security practitioners we need to assume that no matter the password requirements, common passwords such as “Summer2021!” will be used. Utilizing MFA requires the user to provide something they know (password), with something they have (authenticator).
Remediation – Implement MFA functionality in the web app.
Improper Session Management
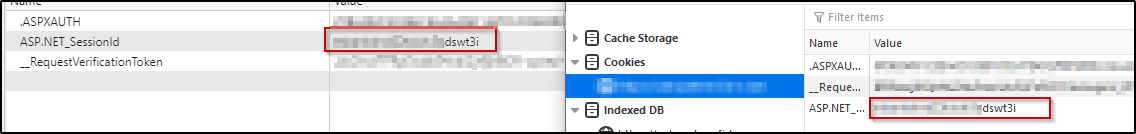
This finding is present in most of our web app assessments, and is somewhat a catch all for a few different issues. The first of these issues is when an application does not invalidate session tokens on authentication events such as logging out. When a user logs in to most web apps a session token is issued upon the user providing valid credentials. This token may be valid for a certain amount of time before being invalidated, or will invalidate upon logout.
We have seen on many applications where servers do not invalidate a token in storage, and a user can pass this session token after logout. We also see on occasion where simply pressing the back button will re-grant access to the application due to tokens not being properly disposed.
Remediation – Invalidate all session tokens on an authentication event.
The second finding is an attack called “pass the cookie.” This is an issue that arises when an attacker can steal a session cookie from another user or admin account, and replace their own session token with the stolen one. This can provide full access to the stolen session, allowing lateral movement or escalation of privileges in the application. As many users simply close their browser rather than use logout functions, access to the session generally exists until an authentication event (login/logout) event occurs elsewhere.
Remediation – Implement application timeout functionality in applications. Educate users on the importance of logging out through easy to find logout links.
Insecure Password Change Features
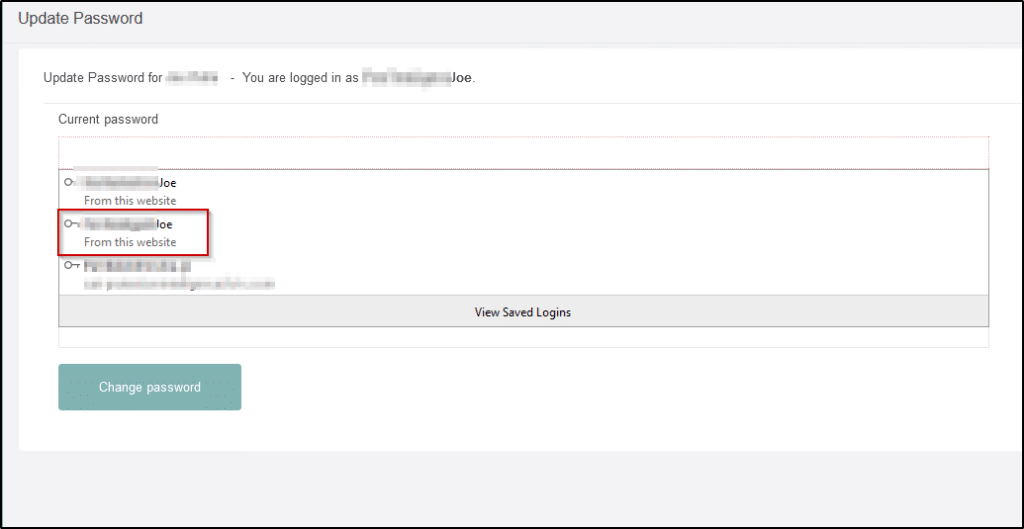
Password change features allow users to modify their password when needed. We often see applications that will require a current password to be provided, along with the new password, in order to change. Browser password managers make this requirement dangerous as applications can no longer disable autocomplete in order to prevent password disclosure. When a user has stored their password in the browser’s manager, it is possible to retrieve it and use it as part of the change confirmation process.
Remediation – Include MFA when changing a user’s password.
Poor Password Policies
We occasionally find web applications that do not implement password length or complexity requirements. As a way of testing this, we use test accounts provided by clients to check the requirements by purposely changing to poor passwords. Some password policies we have discovered include:
- No password requirements at all, despite passwords being a part of authentication
- Single character passwords being permitted
- Passwords with no complexity requirements (no uppercase, number, special character needed)
This creates obvious user access vulnerabilities as simple passwords are more easily bruteforced.
Remediation – Implement password length and complexity requirements according to industry and organizational best practices.
Improper Patch Management
Good patching shows an organization’s dedication to maintaining security of client and employee data and the user experience. Oftentimes we find vulnerable web servers, CMS platforms, and plugin libraries in use in applications. These vulnerabilities may be something low hanging, such as information disclosure about the underlying host. Other vulnerabilities are more severe, and may lead to cross-site scripting, SQL injection, or remote command execution. Implications can be massive depending on the vulnerable feature, and these are often a first stop for attackers.
Remediation – Implement organizational patch management policies that require regular checks for vulnerable solutions and update as needed
Our testers check for these types of vulnerabilities and more on every web application penetration test, and will provide feedback on how to remediate if found. For more information Contact Us
References
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers. Pentest Services: https://tcmdev.tcmsecurity.com/our-services/ Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | InstagramContact Us: sales@tcm-sec.com