Many of our clients perform vulnerability scanning on a regular basis but find that they still don’t perform as well as they’d like on penetration tests. Well today we’re going to discuss a finding that’s frequently found on networks, that many vulnerability scanners consider a Medium Risk, and that usually ends in objective achievement. We’re talking about the not requiring SMB Signing.

What is SMB Signing?
SMB signing aids in preventing man in the middle attacks by allowing the recipient of SMB communications to confirm the authenticity of packets received. Unfortunately, Nessus considers this only a medium risk finding as shown here, which cause organizations to gloss over it. One could argue that by itself, “SMB Signing not required” is a medium risk to an organization but we find it’s often chained with other misconfigurations to create a perfect opportunity for an attacker to take over an environment.
Typical Attack Scenario
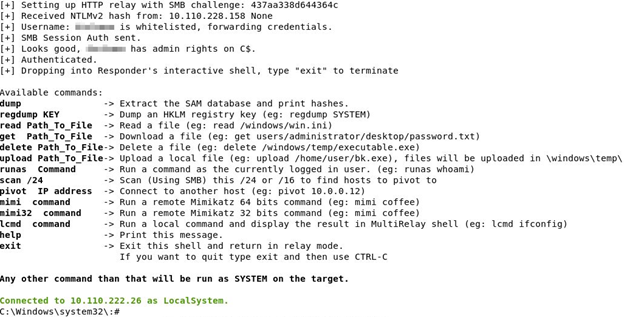
After basic enumeration, one of the first tools attackers will often start is Responder which is a poisoner tool that responds to various network requests such as LLMNR requests. Easy configuration changes allow a malicious actor to chain this with machines that don’t require SMB signing to simply relay SMB authentications by using tools like MultiRelay.py or ntlmrelayx.py. This allows an attacker to land on a machine without ever knowing the password or bothering to crack password hashes. Once on a system, attackers often dump hashes from the machine and attempt to spray those credentials across the network to obtain additional access and with the hopes of landing on a machine with a Domain Administrator hash stored on it. An interesting alterative is to run “mimi” which is a form of Mimikatz that can dump cleartext credentials from a machine.
Remediation
SMB Signing has 3 configuration options: Disabled, Enabled, and Required. Required is the most secure option and the one we most often recommend our clients use. Microsoft has additional information on how to configure this setting here along with basic signing information for SMB1 and SMB2 here. In general, it’s done through group policy changes by setting “Digitally Sign Communications” to “Always”. To further protect from this style of attack it’s recommended to disable LLMNR and NBNS/NetBIOS.

About the Author: Heath Adams
Heath Adams, also known as “The Cyber Mentor,” is the CEO of TCM Security. While Heath is an ethical hacker by trade, he also loves to teach! Heath has taught courses to over 1,000,000 students on multiple platforms, including TCM Academy, Udemy, YouTube, Twitch, and INE.
Heath has held many certifications, including CISSP, PNPT, QSA, GSNA, OSCP, ECPTX, and eWPT. He also holds an MBA degree.
Finally, Heath is also a husband, animal dad, tinkerer, and military veteran.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com

