Overview
TCM is thrilled to continue the, “Practical Cybersecurity Awareness” blogs this week during Cybersecurity Awareness Month. The four topics discussed throughout the month of October will be compiled into a free course at TCM Academy available on October 31, 2023. Today we continue our four-part series with learning the essential practices to safely browsing the internet!
The internet has become an integral part of our daily lives. We shop online, bank online, and social media is becoming increasingly dominant in our lives. But just as we take precautions in the physical world, the online realm requires us to be equally vigilant. Safe browsing is not just a good habit—it’s a necessity.
HTTPS: The First Line of Defense
You might have noticed websites starting with ‘HTTP’ or ‘HTTPS’. The latter is the more secure version. HTTPS stands for HyperText Transfer Protocol Secure. But what does this actually do for us?
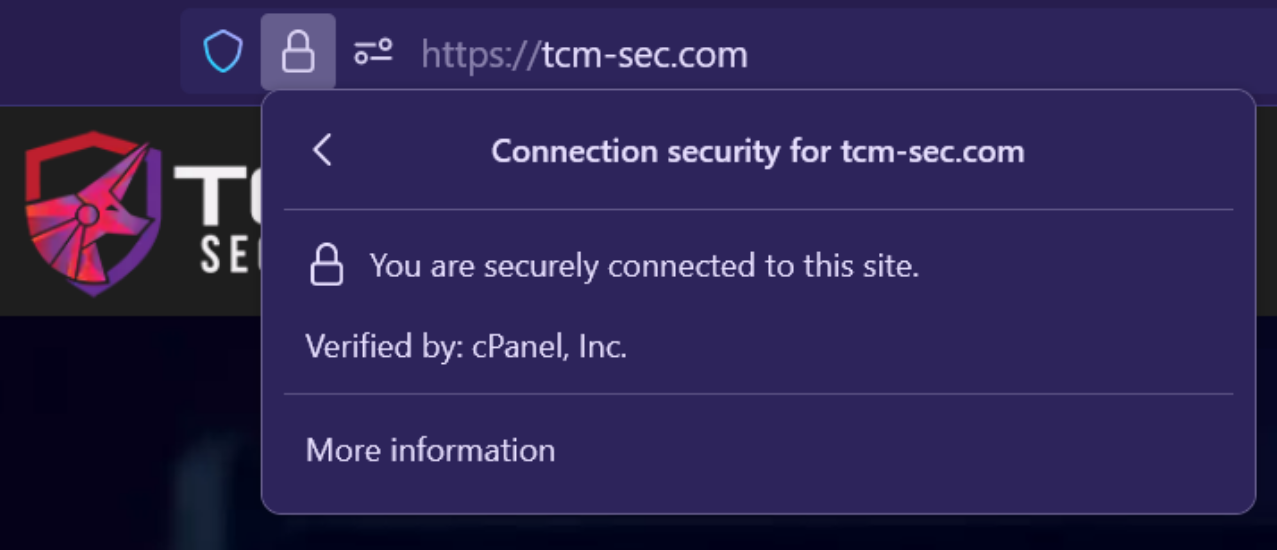
When you see HTTPS in the URL, it indicates that the website is using a secured connection, encrypting data transferred between your browser and the website. This encryption ensures that your data, such as passwords or credit card numbers, remains confidential during transit.
Good habit: Always ensure that websites you input sensitive information into have ‘https://’ before the URL. Be extra cautious if a site that previously had HTTPS suddenly reverts to HTTP.
In all popular browsers you will see a lock icon, this indicates that the site has a valid certificate and that the HTTPS being used is secure.
Domains and Trick Subdomains: Not All URLs Are What They Seem
One of the oldest tricks in the book is to use URLs that look legitimate at first glance. For instance, `https://legitimate.com.fakesite.com` seems like it belongs to ‘legitimate.com’ at first, but in reality, the main domain here is ‘fakesite.com’.
Tricky subdomains and slight misspellings (like ‘tcm–sec.com’ with an extra ‘-‘) aim to mislead users into thinking they are on the legitimate site. Furthermore, domains with similar names such as ‘tcm-sec.co.uk’ can appear to be legitimate.
Good habit: Always double-check the URL in the address bar, especially before entering any personal information. Bookmark essential websites (like your bank or favorite online stores) or navigate to them manually rather than following links.
Downloads from Trustworthy Sources: Don’t Invite the Thief
We often download apps, software, and files from the internet. However, not all sources are trustworthy. Malicious software (malware) can harm your device, steal your data, or even encrypt your files and ask for a ransom.
Good habit: Only download software or apps from well-known, reputable sources. If you’re on a PC, that might mean sticking to software providers you recognize or downloading directly from the developer’s website. On mobile devices, try to restrict your downloads to the official app stores.
Safeguarding Sensitive Transactions: Double the Security
Online banking and shopping require the utmost caution. Here are some best practices:
Good habit: Enable 2FA whenever possible. This security measure requires you to provide two types of identification before accessing your account, such as a password and a one-time code sent to your phone.
Good habit: Avoid conducting sensitive transactions over public Wi-Fi networks or from shared computers.
If you have kids or use a shared family PC, they can often be at risk as many free games, download and fun icon sets that contain malware are targeted towards kids. If you don’t have a private PC that you can use, stick to your smartphone for things such as online banking wherever possible.
Keeping Up to Date: Your Shield Against the Unknown
Cyber threats are continually evolving. What was safe yesterday might be vulnerable today. Thankfully, software developers and internet security professionals work tirelessly to patch known vulnerabilities and many modern browsers now have ‘silent’ updates where they will update in the background without needing anything from you or causing you to wait.
Good habit: Update your operating system, web browsers, and security software when asked. Automated updates are your best friends in this regard. However, you should be cautious about ‘update’ notifications from unknown sources such as website popups, as these can be scams.
Conclusion
The internet, in all its vastness, is akin to the wild west. There’s opportunity, convenience, and innovation, but there’s also risk. Safe browsing habits act as your compass and shield, guiding you away from potential pitfalls and ensuring you reap only the benefits of this digital age. Stay informed, stay cautious, and browse safely!

About the Author: Alex Olsen
Alex is a Web Application Security specialist with experience working across multiple sectors, from single-developer applications all the way up to enterprise web apps with tens of millions of users. He enjoys building applications almost as much as breaking them and has spent many years supporting the shift-left movement by teaching developers, infrastructure engineers, architects, and anyone who would listen about cybersecurity. He created many of the web hacking courses in TCM Security Academy, as well as the PJWT and PWPT certifications.
Alex holds a Master’s Degree in Computing, as well as the PNPT, CEH, and OSCP certifications.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

