Insecure Service
SMB Service Availability to Internet or Other Unauthorized Users
TCM-KB-EXT-001
Last Updated: 6/26/2023
Microsoft Windows Server
The recommended remediation steps and configurations described in this response would primarily affect systems running Microsoft Windows Server.
SMB
SMB refers to Server Message Block.
A small message block refers to a compact unit of data transmission used in communication protocols. It typically contains a limited amount of information, such as a command, status update, or a small portion of a larger message, allowing for efficient and rapid exchange of data between devices or systems.
Contributor

Joe Helle
Chief Hacking Officer
Recent Blogs

The Role of Phishing Simulations in Security Awareness Training
Organizations can integrate phishing simulations into their security awareness training to help employees recognize potential phishing attempts.
Teaching Kids Cyber Security Concepts with Bluey
We will take a look at two episodes of the show, Bluey, and how they can be used to explain cybersecurity concepts in a way that kids will understand.

Persevering in a Challenging Cybersecurity Job Market
What is Perseverance? Perseverance: persistence in doing something despite difficulty or delay in achieving success. Ironically, I started writing this blog a couple months ago and initially struggled to get some momentum. No two people reading this are alike, but...

How to Use Social Media for Cybersecurity Networking
I know as you read this, the word “networking” has likely sent your eyeballs rolling. For better or for worse, networking has become a necessity in today’s job market - and cybersecurity is no different. In the last decade of working in cybersecurity, I have found...

Preventing Burnout in the Cybersecurity Field
We can’t defend against cyber threats if we’re dealing with burnout. In this article, we explore the signs and discuss practical strategies to prevent burnout.
Issue
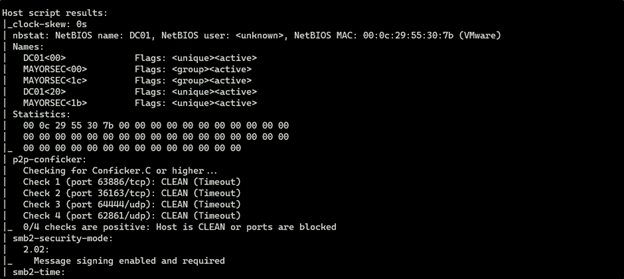
The SMB service on the domain-joined endpoint is available to the Internet. This could permit information disclosure of internal network identities (i.e., fully-qualified domain names of internal domains) and accessibility of an external entry point for brute force attacks.
Recommended Remediation
The following outlines the recommended steps that the systems and network administrators should take in order to secure the environment.
Utilizing a user account with administrative privileges, open Windows Defender Firewall with Advanced Security.
Right-click inbound Rules and select New Rule.
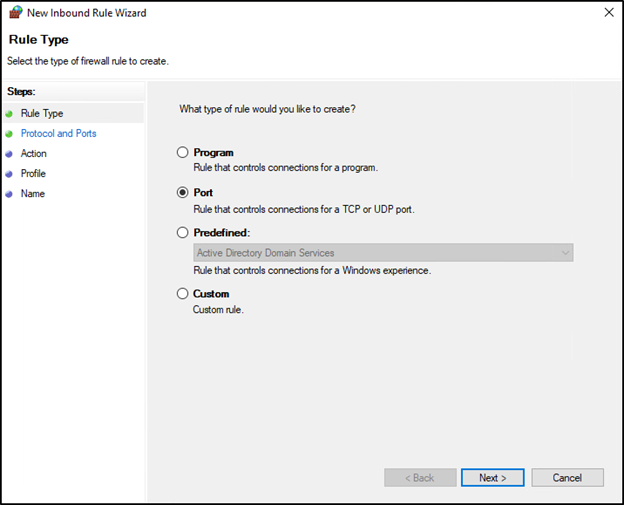
In the Rule Type window, click Port and select next.
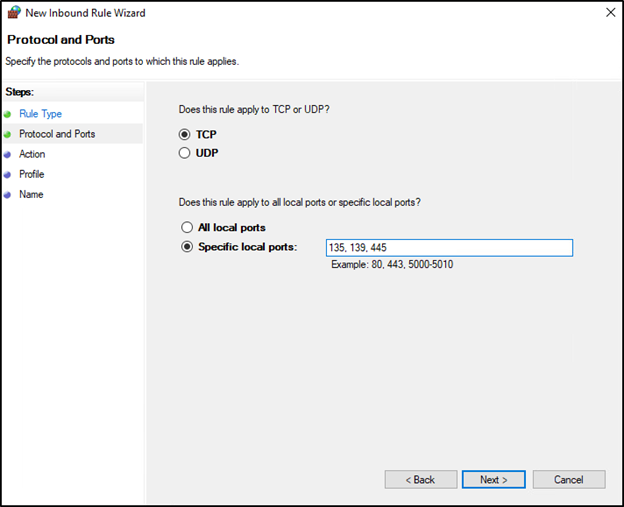
Select the TCP option, and below, the Specific local ports option. Enter ports 135, 139, 445 and click Next.
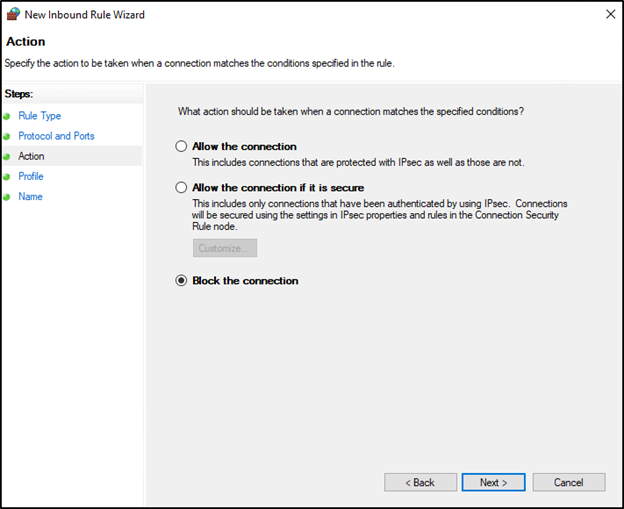
On the next screen, select Block the connection and press Next.
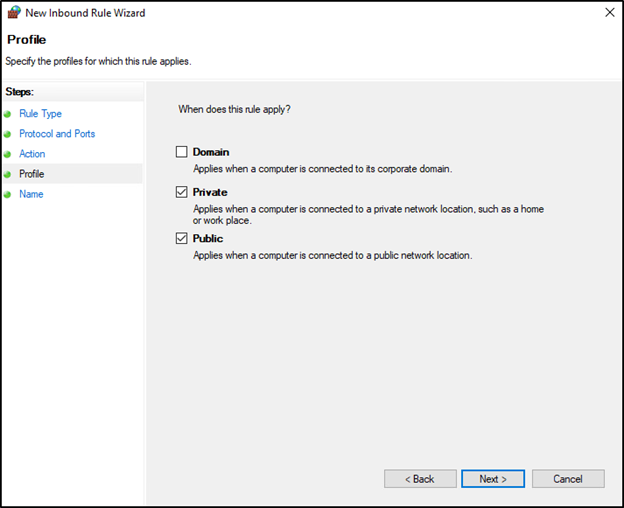
In the next window, deselect Domain and Private, and select Public. If you prefer to only allow domain-connected devices to access the SMB service, deselect only Domain, and select Private and Public. Press Next when complete.
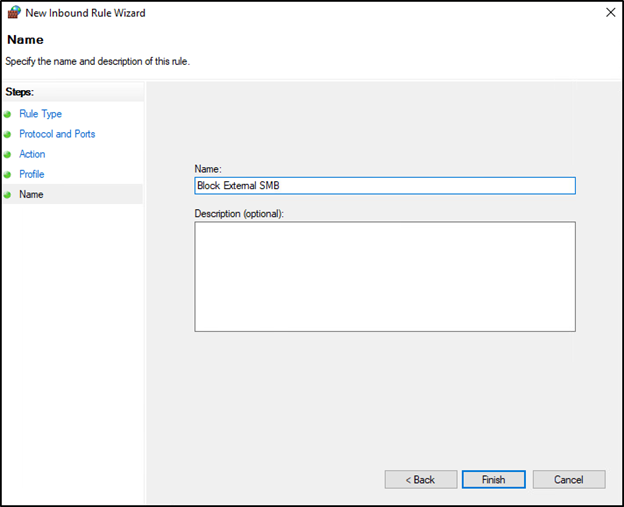
In the next window, specify a name for the new firewall rule, and enter a description if desired. Press Finish when complete.

Sample Pentest Report
See The Results We Can Deliver To You. No Email Required.
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.