Content discovery is often focused on finding files and folders. However, modern applications not longer conform to this hierarchical approach and specifically applications that use APIs. Kiterunner is a tool that can be used to discover routes and endpoints used in modern applications that may be missed with tools that look to bruteforce files and directories.
You can find Kiterunner here: https://github.com/assetnote/kiterunner
Prefer to watch instead of read? See below:
Depth Scanning
Depth-based scanning is aimed at detecting wildcards for virtual application path-based routing. The depth refers to how many directories deep the baseline checks are carried out.
- /api/v1/user
- /api/v2/user
- /api/v2/admin
- /dev/user
Depth 0:
- /
Depth 1:
- /api
- /dev
Depth 2:
- /api/v1
- /api/v2
- /dev/user
Depth 3:
- /api/v1/user
- /api/v2/user
- /api/v2/admin
By default, ‘kr scan’ has a depth of 1 and while increasing depth improves scan accuracy, it also raises the number of requests to the target (baseline checks * depth baseline directories).
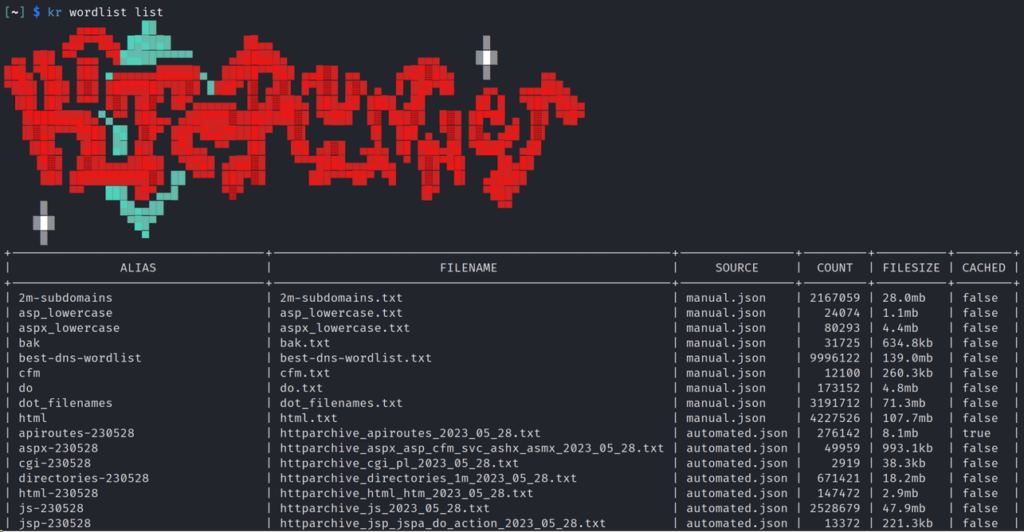
Choosing a Wordlist
The Assetnote wordlists are available with kr wordlist list. When used, they are downloaded and stored in ~/.cache/kiterunner/wordlists.
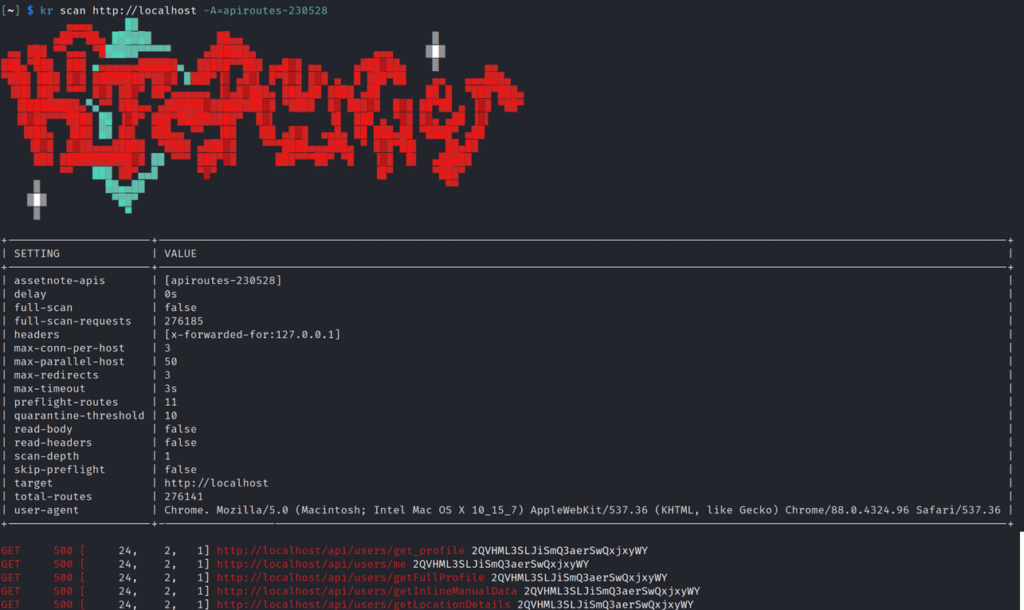
Basic API Scan
kr scan http://localhost -A=apiroutes-230528
Some options you might want to use are:
- –user-agent to set the user agent as blank or unusual ones are often blocked on production web applications
- –ignore-length to filter out results of a specific you don’t want to see
- -A=apiroutes-230528:1000 the :1000 means you’ll be using the first 1000 lines of the wordlist instead of the entire wordlist
- –max-connection-per-host defines how many connections per host is allowed, the default is 3
Speed
Kiterunner is also designed with speed in mind, which is not surprising since it’s written in Go. The recommendations in the repository are:
- -x, –max-connection-per-host – maximum number of open connections we can have on a host. Governed by 1 goroutine each. To avoid DOS’ing a host, we recommend keeping this in a low realm of 5-10. Depending on latency to the target, this will yield on average between 1-5 requests per second per connection (200ms – 1000ms/req) to a host.
- -j, –max-parallel-hosts – maximum number of hosts to scan at any given time. Governed by 1 goroutine supervisor for each
As well as advice to maximize performance:
To maximize performance when scanning an individual target, or a large attack surface we recommend the following tips:
- Spin up an EC2 instance in a similar geographic region/datacenter to the target(s) you are scanning
- Perform some initial benchmarks against your target set with varying -x and -j options. We recommend having a typical starting point of around -x 5 -j 100 and moving -j upwards as your CPU usage/network performance permits
You can read more about this here: https://github.com/assetnote/kiterunner#concurrency-settingsgoing-fast
Wrapping Up
Kiterunner is a robust tool designed for effective content discovery and API endpoint bruteforcing. Its ability to perform rapid content discovery and negotiate routes in modern web applications makes it a key tool to add to your arsenal.

About the Author: Alex Olsen
Alex is a Web Application Security specialist with experience working across multiple sectors, from single-developer applications all the way up to enterprise web apps with tens of millions of users. He enjoys building applications almost as much as breaking them and has spent many years supporting the shift-left movement by teaching developers, infrastructure engineers, architects, and anyone who would listen about cybersecurity.
Alex holds a Master’s Degree in Computing, as well as the PNPT, CEH, and OSCP certifications.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.