What are the ways that you can start to understand the niche field of Mobile Application Penetration Testing? This blog series will explain some of the best tools and mobile apps you can use today to start learning about this exciting field.
Introduction: What is Static Analysis?
It is obvious that the world of mobile penetration testing also follows the trends of the mobile phone markets. Specifically, most companies are developing applications for both iOS and Android devices.
Broadly speaking, mobile application penetration testing can be divided into two primary categories: static analysis and dynamic analysis.
Static Analysis involves analyzing an application file to extract data and/or identify security misconfigurations. Vulnerabilities in this phase can vary widely, but here are a few common ones we have discovered at TCM Security:
- Extracting hard-coded secrets such as client credentials or other secrets.
- Enumerating the URLs and services used by the application (this could be an API endpoint for a function, or a third-party URL such as a firebase or AWS url).
- Discovering security misconfigurations in the application settings.
- Uncovering files generated at application startup or used for default configurations.
In a recent penetration test, we used static analysis to reveal the following treasures:

In this example, simply by examining the application source code we extracted a large number of URLs. This allowed us to chart out the application logic before engaging with the application. For instance, we expect the application to have a Debit Card screen, an onboarding screen, a password reset screen, and the option for biometric enrollment for logging in.
Next, we will explore some of my favorite tools for static analysis, highlighting how they have assisted me in mobile pentests in each of their unique ways.
Static Analysis Tools for Mobile Application Penetration Testing
MOBSF
MobSF, short for “Mobile Security Framework,” serves as a cross-platform security analysis tool analysis tool for both Android and iOS applications. Running within a Docker container, MobSF can analyze either type of application on top of any operating system. Need to analyze an iOS file on your Windows machine? No problem!
MobSF proves invaluable for swiftly identifying misconfigurations in applications from a static analysis perspective. I frequently use this application for quick wins and to perform a makeshift “vulnerability scans” of mobile applications. I highly recommend developers themselves also use MobSF to scan their applications and identify any weaknesses introduced into their applications.
Here are a few examples of vulnerabilities discovered in a recent penetration test using MobSF.
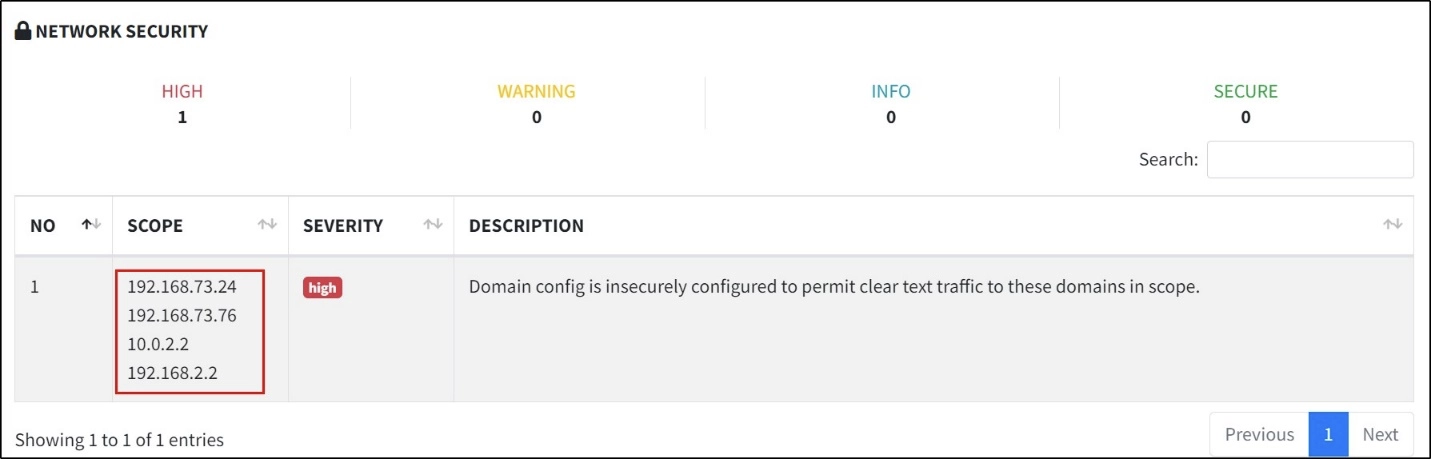
This instance showcases a mobile application misconfigured to transmit traffic to some internal servers via HTTP. As we know, using HTTPS and encrypting traffic is strongly preferred from a security perspective.
MobSF also promptly flags common misconfigurations in your application. Here are some prevalent ones encountered in penetration tests:
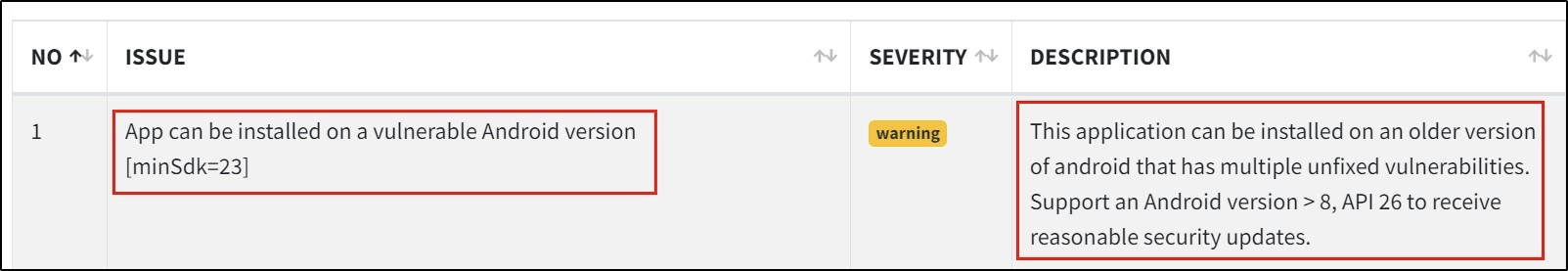
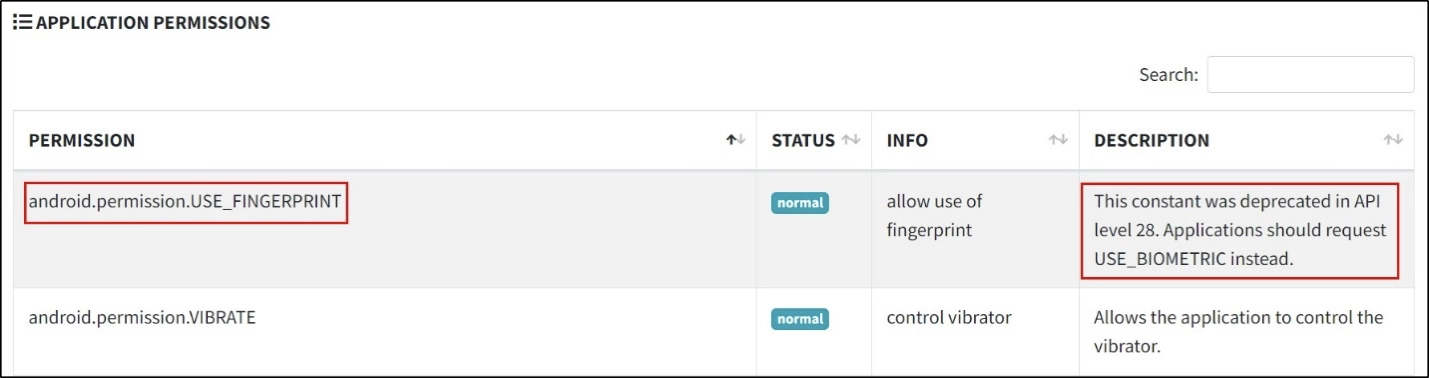
As depicted in the screenshots, MobSF identifies supported mobile devices and alerts developers if they are breaking some best practices (as demonstrated by using the deprecated biometric fingerprint API).
Static Analysis Tools for Android Applications
In addition to MobSF, the following tools are valuable for static analysis in Android applications:
- JADX-GUI
- Apktool
JADX-GUI
JADX-GUI is a tool that I consistently utilize on every mobile application penetration test. This tool allows you to upload an APK file and navigate through its functions and source code. Once imported into JADX-GUI, the interface resembles a folder structure, facilitating easy navigation.
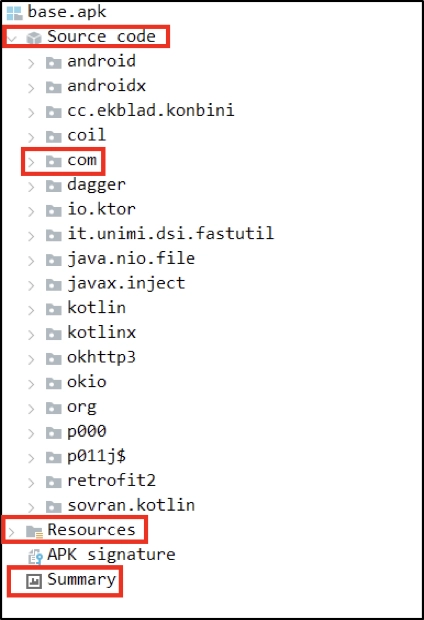
As you can see, the application source code is nicely broken out into a folder-like structure. This is very handy, but one of my favorite features of JADX-GUI is the “search” functionality.
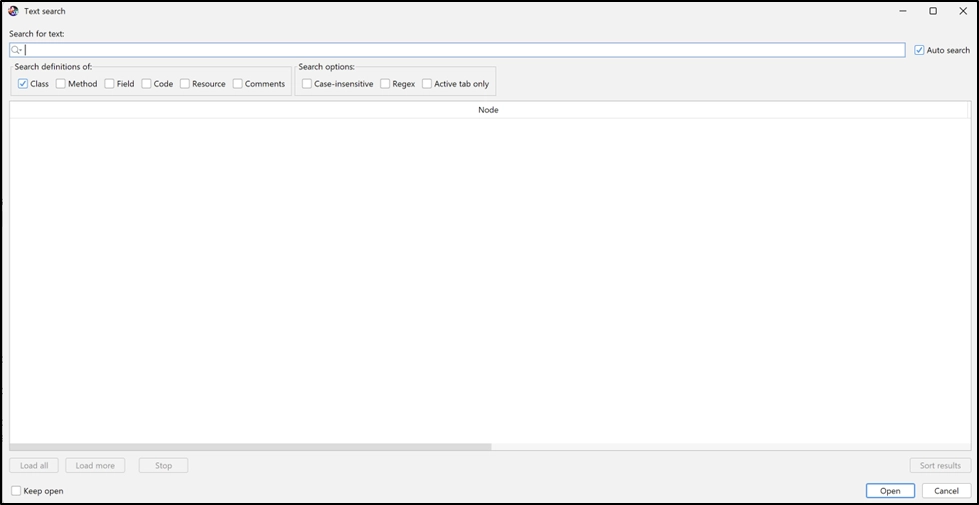
The search functionality within JADX-GUI is particularly beneficial. It enables you to search across classes, methods, fields, raw code, resources, and even developer comments. For instance, searching for the term “key” quickly yields various results.
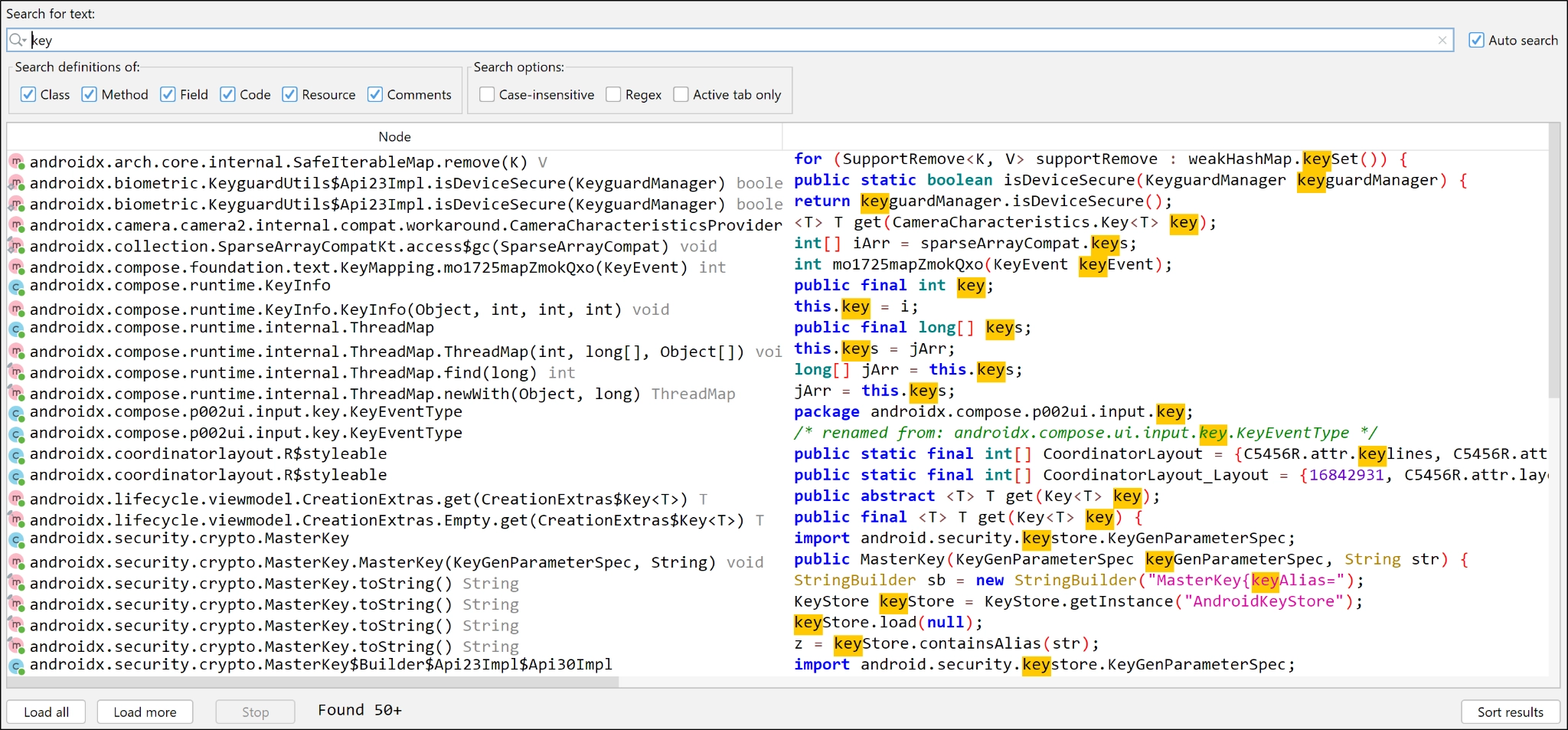
The search feature of JADX-GUI has secured some quick wins for me on multiple pentests. I hope that you also explore this tool and its many additional features.
Apktool
Apktool is designed specifically for reverse engineering APK files. The command-line interface tool automatically decompiles an APK file into its constituent parts. Decompile an application by issuing the command:
apktool d myapp.apk
This will turn the application into a series of folders from which you can further dissect and analyze the application. The main benefit of apktool is that when an application is decoded using this tool you can easily edit the source code. After editing the source code, you can quickly recompile it by using the following command to rebuild the folder structure into an apk file:
apktool b myapp/
Static Analysis Tools for iOS Applications
In addition to MobSF, the following tools are also useful for conducting static analysis in iOS applications:
- Otool
- File Explorer/Mac OS Finder
Otool
Otool is a generic UNIX/Linux command line tool that can assist in decompiling iOS IPA files. Its primary advantage lies in its compatibility with various Linux terminal commands by using the pipe operator. For example, you can use the commands grep, strings, and find in combination with otool output.
File Explorer/Mac OS Finder
Finally, and paradoxically, one of the most useful tools for decompiling iOS IPA files is the Mac OS Finder. All iOS IPA files are essentially zipped folders of resources. In fact, by changing the file extension of an IPA to a ZIP, you can extract the contents and navigate them using the Mac OS Finder application just like any folder on your Desktop. The same is also applicable in Windows environments with the Windows File Explorer.
Here is an example to quickly decompile an IPA application using the File System on Windows.
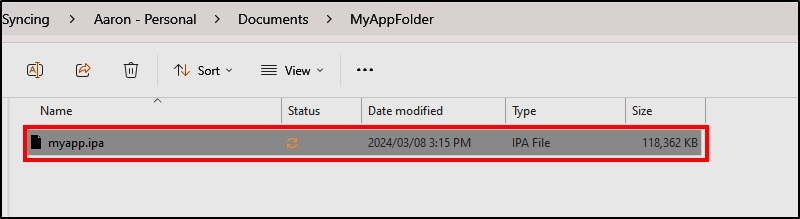
Change the file extension to “zip” and click “Extract All” to extract the contents of the application.
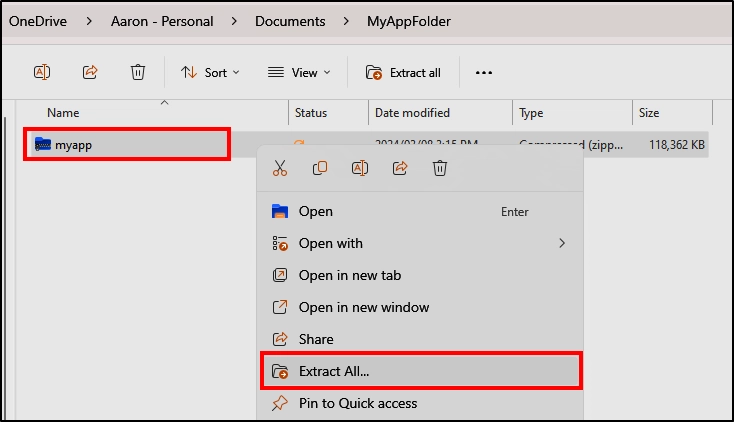
Once extracted you will have multiple folders to hunt through. The “Payload” folder is where most of the juicy details can be found.
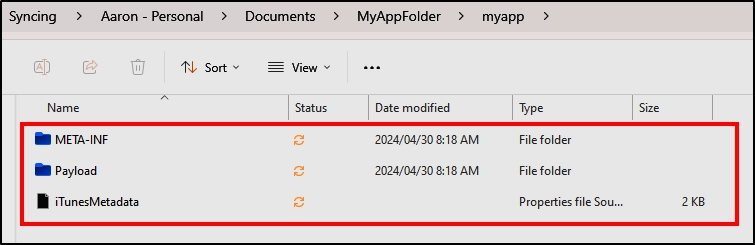
As you can see, even simple file utilities can be useful when analyzing mobile applications!
Conclusion
Do you have a favorite tool for mobile application penetration testing? If you want to learn about these tools and more, check out the Mobile Application Penetration Tester course at TCM Security as well as our Practical Mobile Pentest Associate certification. If you are interested in penetration testing services for your mobile apps, don’t hesitate to contact us by using the form below!
Next up in the series, we look at tools for dynamic analysis in mobile application penetration testing.

About the Author: Aaron Wilson
Aaron is a passionate security professional with experience in the Fortune 50. He is the Red Team Lead at TCM Security, responsible for leading the penetration testing and consulting teams. He is also an avid Capture the Flag Creator and has published multiple rooms on TryHackMe. Aaron is also CEO and Founder of the Wilson Security Group and publishes videos on YouTube on security topics and cybersecurity certification reviews.
Aaron holds certifications such as the eMAPT, CISSP, eCPPTv2, eWAPTv2, CEH, and eJPT certifications among others. He holds a bachelor’s degree in Security and Risk Analysis from Penn State University as well as a Master’s in Information Assurance and Cybersecurity from Western Governor’s University (WGU).
Follow Aaron on Social Media:
LinkedIn – https://www.linkedin.com/in/wilson-security
YouTube – https://www.youtube.com/c/WilsonSecurityGroup
TryHackMe Hacker Methodology – https://tryhackme.com/r/room/hackermethodology
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

