Introduction
The new Practical Web Pentest Professional (PWPP) certification is now available! In this article, we’ll talk about how to prepare for the exam. You won’t find any spoilers, but you will find some helpful tips for how best to prepare for and approach the exam. For a video version of this post, check out the video below.
How is the Practical Web Pentest Professional Exam Structured?
Similar to other TCM Security exams, you’ll have a number of days to carry out a pentest on a target and then extra time to write a report. To start the test, you’ll login to the platform, use a VPN file to connect to the environment, and then begin your pentest. Remember to treat the exam like a real-world pentest. You will need to work through the target methodically and the report should include low, medium, and high findings. For the PWPP, there’s no debrief.
What Do I Need to Know to Pass the PWPP?
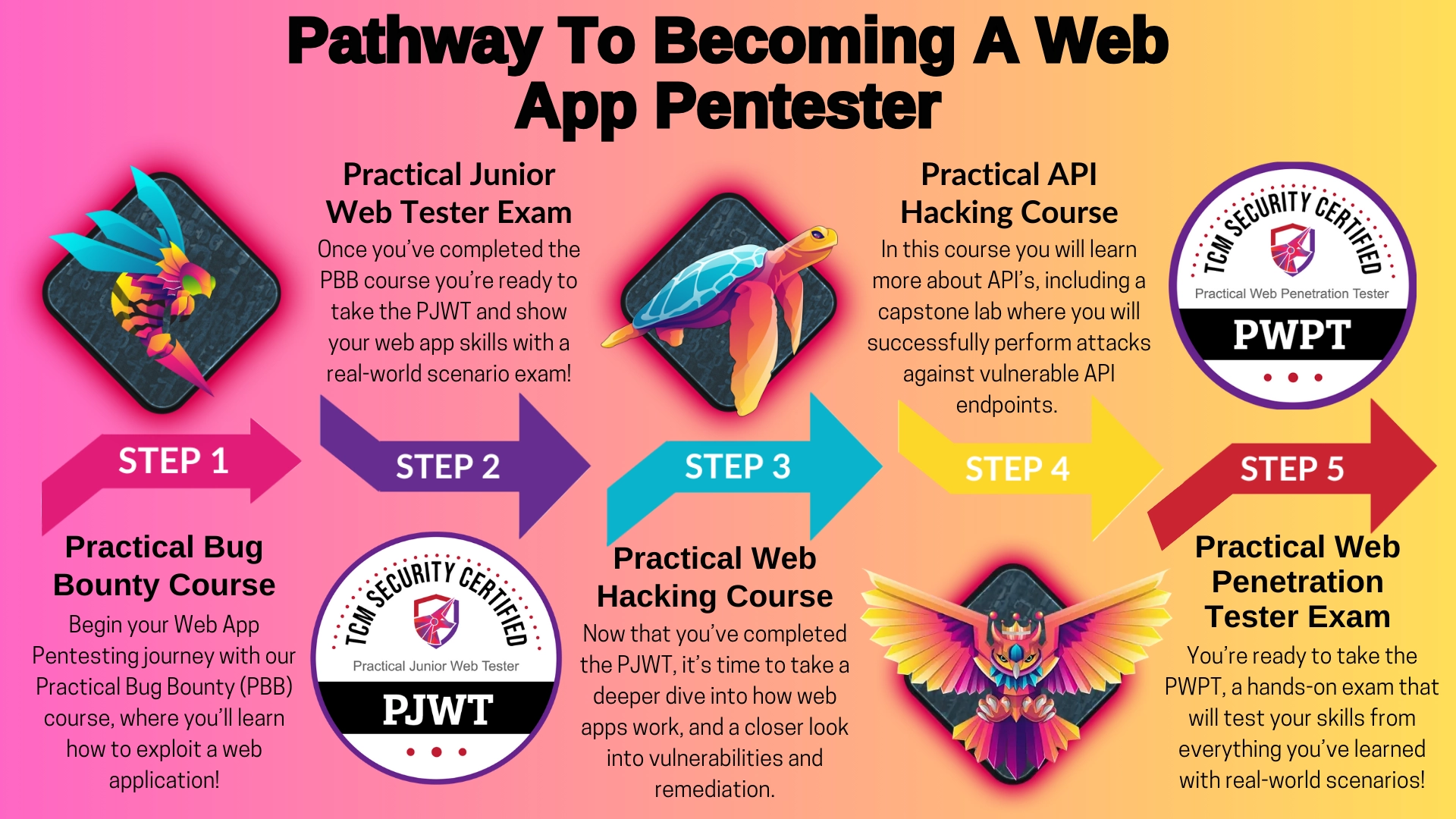
All the essential knowledge to pass the certification is covered in the two TCM Academy courses: Practical API Hacking and Practical Web Hacking. If you go through these courses, complete the exercises, take notes, and absorb the material then you will be well-prepared to take the exam. There are no “gotchas” included; instead, the exam mirrors real-world issues that I’ve encountered during pentests. These issues are often missed by scanners and finding them requires knowledge of the vulnerability, a solid testing methodology, and, naturally, troubleshooting skills.
Throughout the courses, emphasis is placed on comprehending the application’s behavior and its response to our inputs. When testing a section of the application, it’s crucial to contemplate the functionality’s purpose and consider relevant vulnerabilities and potential edge cases.
I want to emphasize that acquiring knowledge of modern web applications and technologies is essential. The Practical Web Pentest Professional certification doesn’t center around an outdated PHP application susceptible to null byte injection. Therefore, understanding concepts such as routing, templating engines, and APIs will greatly benefit you. While these topics are covered in the course material, if you haven’t previously constructed a small modern web app, consider spending some time building one. Whether it’s creating something in Flask or developing a small API-driven app using Node.js and Express, building your own application will facilitate a deeper understanding of how modern web applications function.
Path to Passing the PWPP
Preparation
Next, let’s talk about the path to passing the PWPP and how you can optimize your chances of success. If you’re just stepping into web app pentesting, bug bounty programs, or application security, we suggest beginning with the Practical Bug Bounty course. This course will equip you with the skills needed for the Practical Web Pentest Associate certification. The exam follows a similar format, but is not a prerequisite for the PWPP.
To prepare for the exam, getting comfortable with HTTP and understanding the different headers, content-types, and common authentication and authorization mechanisms like JSON Web Tokens and session tokens is really important. Fortunately, the included course materials offer an excellent opportunity to acquire this insight. Be sure to closely examine requests and responses, and don’t hesitate to research anything that isn’t immediately clear. It’s also important to understand common security controls like input filtering, and how to test that these controls are effective.
Create a Plan of Attack
Once you have finished studying, develop a game plan for your exam. While having detailed notes is beneficial, spending excessive time re-reading them and then creating tests, as well as double-checking for any oversights, wastes a lot of time.
Personally, I have checklists for different technologies and vulnerabilities. So when I encounter a search box, for instance, I immediately think about potential risks: my input likely interacts with the database, so I need to test for injection vulnerabilities; if my input is reflected back on the page, I should test for XSS; and if the application employs a templating engine, I need to consider template injection as well. I have checklists and predefined payloads for each of these attack vectors, enabling me to kickstart my testing process. Moreover, with the additional context I gather while testing the application, I can adapt and refine my checklist, adding or removing checks as necessary. At the very least, these checklists help me identify which wordlists might be suitable for fuzzing, providing a solid starting point for my examination.
Once you’ve mastered the fundamentals, shift your focus to considering the impact of attacks. And what I mean by this is really thinking about how your payload is impacting the application, its users, and the administrators. This approach has two major benefits. Firstly, it allows you to accurately gauge whether a vulnerability poses a major threat or is merely a minor inconvenience. Secondly, it enables you to recognize opportunities for chaining vulnerabilities together to accomplish a larger objective.
So whenever you find something, even if it’s just quirky behavior, think to yourself….so what? What does this really mean? What does this enable me to do?
Next, you want to get into the habit of verifying your findings and documenting proof of concepts. Your proof of concept doesn’t necessarily need to be something like a standalone script; instead, focus on creating simple instructions that other engineers can easily follow. This practice ensures that your findings are reproducible and well-documented. Moreover, these notes can prove invaluable in the future when you encounter similar issues.
Prepare Your Environment
Finally, ensure your environment is prepped and ready to go. This entails configuring Burp Suite to your preferences, with your preferred extensions already installed. Also, ensure your wordlists and payload lists are prepared or at least bookmarked and easily accessible in a convenient format.
Optional Extra Practice
If you feel like you need some extra practice before taking the exam or you simply want to sharpen your skills in your spare time, I recommend trying the practitioner level mystery labs on PortSwigger. Additionally, revisiting the challenges from the course material is also an excellent way to practice. There may be small details or alternative payloads to uncover, which can further enhance your understanding and proficiency.
Working on small web CTF challenges can also be beneficial. Often, these challenges require focusing on attacking specific functionalities, which can help sharpen your ability to discern which attacks to deploy and when to utilize them effectively. This hands-on experience can significantly enhance your skills and intuition in real-world scenarios.
PWPP Exam Tips
To wrap up, here are some more generic exam tips that are still incredibly important. Firstly, prioritize taking regular breaks. Even during my daily work, I’ve noticed that each time I take a break, whether it’s to make a cup of tea or step away from my desk for a minute, I almost always return with a fresh perspective and either solve the problem I was stuck on or make meaningful progress.
it’s beneficial to create a to-do list of tests for edge-cases as they occur to you, and then return to them systematically. This approach helps prevent distractions and ensures thorough testing. For instance, in the search bar example mentioned earlier, where potential vulnerabilities include injection into the database, XSS, and template injection, if you start testing for XSS and then suddenly consider template injection before completing the XSS testing, you might overlook discovering a vulnerability. Or, at the very least, you’ll waste time revisiting or re-testing later. Therefore, take notes and jot down ideas as you progress through your testing.
My final tip is to take your time. The exam has been structured to allow sufficient time for completion, and you’re likely to exhaust your ideas before running out of time. Therefore, utilize this time to take comprehensive notes, ensure thorough testing, and if you find yourself finishing testing everything and feeling like you’ve missed something, there will still be time to go back and reassess. Nothing in the exam is designed to trick you, its purpose is to demonstrate your ability to identify and exploit real-world issues.
Conclusion
That’s all you need to know to prepare for the PWPP. If you don’t ace it the first time, don’t worry. A free retake is included with every certification voucher. Go back to the materials and review what was previously covered, and try to identify where you might have come up short. If you need help, join our Discord! There’s a fantastic community of people who will be happy to figure out where you may need more practice.

About the Author: Alex Olsen
Alex is a Web Application Security specialist with experience working across multiple sectors, from single-developer applications all the way up to enterprise web apps with tens of millions of users. He enjoys building applications almost as much as breaking them and has spent many years supporting the shift-left movement by teaching developers, infrastructure engineers, architects, and anyone who would listen about cybersecurity. He created many of the web hacking courses in TCM Security Academy, as well as the PWPA and PWPP certifications.
Alex holds a Master’s Degree in Computing, as well as the PNPT, CEH, and OSCP certifications.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.


