Introduction
Over the last decade, the IoT landscape has witnessed significant growth, with an estimated 18 billion devices currently connected, and this number is rapidly expanding with each passing year. Projections suggest that the count could soar to 40 billion in the next decade. This proliferation of connected devices underscores the critical need for robust security measures. Consequently, there has never been a better time to learn about IoT security.
In this series, I’m going to talk about how you can easily get started with IoT and hardware hacking. Before we dive into the first part of the series, let’s review some fundamentals.
Why Combine IoT and Hardware Hacking – Is Hardware Knowledge Essential for IoT Hacking?
IoT hacking shares similarities with other hacking disciplines like web, network, mobile, and even cloud. However, it presents a unique attack surface due to the accessibility of hardware to consumers, security researchers, and adversaries alike. Hardware vulnerabilities in IoT devices can have significant repercussions. For example, a smart lock that could be unlocked from the outside by accessing the keypad pcb.
Even if hardware security isn’t a priority for manufacturers, access to the hardware can facilitate the discovery of vulnerabilities in other attack surfaces such as web portals or interconnectivity to cloud backends. With this in mind, it’s still possible to get into IoT hacking and start finding vulnerabilities without spending a dime on hardware or knowing anything about it.
What Background Experience is Necessary for IoT Hacking?
While IoT hacking shares commonalities with other hacking domains, it also requires baseline knowledge of each of those avenues and their intersections with each other. Personally, I wouldn’t recommend starting with IoT hacking if you’re brand new to ethical hacking or cybersecurity. Instead, I’d recommend starting with a broader intro to ethical hacking. The Practical Ethical Hacking course on TCM Academy provides a solid foundation for beginners. If you’re absolutely new to hacking I’d suggest starting with that before moving into IoT hacking.
Ethical Hacking and Legal Considerations
As with other forms of ethical hacking, it’s imperative to adhere to the golden rule of “don’t hack or test anything you don’t own and/or have permission to hack or test.” Not only is this rule essential for remaining ethical, it can also keep you out of big legal trouble! Violating this rule can have severe legal repercussions, including potential jail time! Additionally, there are also potential legal concerns with testing and reverse engineering firmware. In the United States, software like firmware is protected by the DMCA (and other regulations) and reverse engineering it can violate DMCA protections. While there are exceptions for security testing and research under the DMCA, it’s essential to stay abreast of regulatory changes and regional laws.
However, you shouldn’t take this blog’s word for it. Regulations frequently change and you may be subject to different laws in your region. You should do your own research on the legalities in your specific region and time frame. Alternatively, using firmware designed for learning IoT security (we’ll talk about some examples in this article), or participating in IoT bug bounty programs with reverse engineering firmware in the scope can help you stay on the right side of the law.
Getting Started in IoT Hacking Without Breaking the Bank
Before we can start hacking, we need to pick up a few tools. We’ll discuss the essential tools and gear needed to build a small toolbox affordably. I’m covering this in the first part of the series so that in the further articles you can already have everything required to follow along. I’m going to assume that you’ve already got a computer to use so that won’t be included.
The “FREE.99” Option: Hardware Hacking on a Budget
IoT hacking can be pursued without spending a dollar or even laying a hand on any hardware. While this isn’t my favorite approach and you may miss out on some vulnerabilities and the advantages that having access to the hardware gives, it’s a valid approach for learning, doing security research, or hunting for bugs.
The firmware, which constitutes the bundle of software running on an IoT device, typically includes components enabling the IoT device to boot up and perform its intended functions. Generally, the firmware comprises elements such as the bootloader, the operating system, or custom code running the device’s operations, alongside additional artifacts like files, tools, scripts, or data. In this getting started series, we’ll specifically focus on devices running embedded Linux due to its prevalence in IoT devices and its similarity to desktop versions of Linux familiar to most hackers. In embedded Linux systems, the firmware comprises three main components, the bootloader (which we’ll examine further in this series), the Linux kernel, and the root file system (RFS). The RFS contains all of the files, binaries, libraries, scripts, and even more that enable the IoT device to function. While the other aspects of the firmware may introduce vulnerabilities worth investigating, the majority of hacker interest lies in the RFS.
IoT Hackers want to obtain the firmware to analyze it and scrutinize it for vulnerabilities. Often, firmware can be acquired without direct access to the device, as manufacturers make it available for download for consumer updates or fixes. Alternatively, beginners can utilize custom firmware designed for learning IoT hacking, such as the one designed for this series,or the IoT GOAT firmware by OWASP.
Once we acquire the firmware, analysis involves attempts to unpack, decrypt, decompress, analyze, and reverse engineer it in order to identify vulnerabilities. Most tools used for this purpose are open source and free to download. This process, known as static firmware analysis, constitutes a significant portion of IoT security research and hacking. While conducting static analysis, you may uncover an interesting binary like a web server that you want to run, debug, or even test a potential exploit. Unfortunately, the Linux kernel and all binaries and libraries in an IoT device’s firmware are likely compiled for a CPU architecture different from that of the host system. Typically, IoT devices use either ARM or MIPs architectures. Although access to hardware can be advantageous, there are alternative methods, such as emulation.
QEMU (Quick Emulator) stands out as the most popular tool for emulating IoT hardware. It is open source and entirely free, capable of emulating various architectures encountered in IoT devices. This is a great video resource on getting started with emulating firmware:
My Favorite Part – IoT Hacking Tools
My favorite part of IoT hacking is the intersection with hardware hacking and the cool gear that comes along with it. One of my goals in this series is to share this passion with you and demonstrate the satisfaction derived from hacking and manipulating hardware firsthand, rather than just looking at a shell. A common misconception I’ve encountered is that hardware hacking is prohibitively expensive and requires expensive gear. While it is true that hardware hacking cannot be solely accomplished with a VM and open source software, it’s not necessary to empty your bank account.
My experience in assembling my personal hardware hacking toolbox has revealed that it closely aligns with the 80/20 rule. This rule states that 80% of the results come from 20% of the inputs, or in this context, the tools. Therefore, we can prioritize the essential tools- the ones yielding the most utility and results- before considering additional, specialized, and potentially expensive tools, if needed at all.
Furthermore, I’ve categorized the gear section must-haves and nice-to-haves, options at multiple price points.
Skip to the end of the article for a list of the essentials required to follow along with this series.
Must-Have Gear to Get Started with Hardware Hacking
Digital Multimeter (DMM)
In my toolbox, the digital multimeter reigns as the most frequently used piece of equipment. It serves as a versatile tool akin to a Swiss Army knife for conducting a wide array of electrical measurements. This device safeguards your equipment by checking voltage levels, verifying pin outs, aiding in reverse engineering circuits, and fulfilling numerous other functions. Digital multimeters are available at various price points, offering a wide range of features. However, the primary advantage of investing in a higher-priced model (apart from accuracy and durability) is the inclusion of autoranging capabilities. Nevertheless, if you are just starting out, opting for a budget-friendly meter is perfectly acceptable and will suffice for the majority of tasks.

Option 1
Option 2
Option 3
Logic Analyzer
Logic analyzers enable the visualization and capture of communications occurring among different hardware components and devices. They play a crucial role in hardware hacking by facilitating the discovery of exposed communication headers and lines to discover what protocols and settings are used. I use my logic analyzer on almost every hardware hacking project I do.

Option 1
Option 2
USB to “X protocol” Adapter
After identifying an open communication line and determining the protocol with your logic analyzer, you’ll need a USB adapter to facilitate interaction with it from your computer. By “X protocol,” I’m referring to commonly encountered protocols such as UART, I2C, SPI, JTAG, or SWD. At the very least, you’ll require an adapter cable capable of communicating via UART as this is by far the most frequently used and abused protocol when hardware hacking.
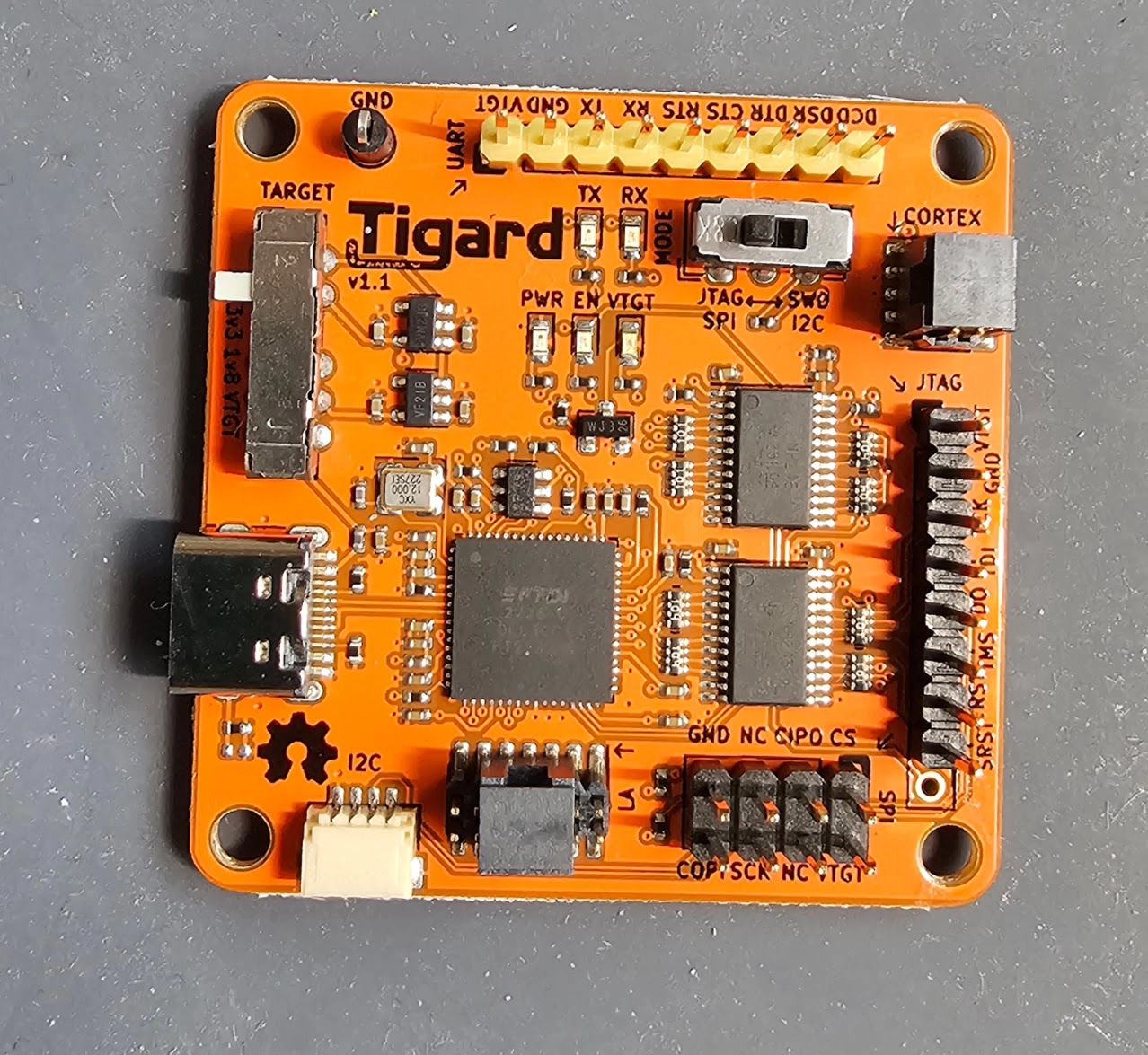
Option 1
Option 2
Option 3
Hand Tools
When working on commercial off-the-shelf consumer IoT devices, you’ll need tools to open them up and access the internal hardware. Based on my experience, most of these devices can be opened up with a jeweler’s Phillips head screwdriver and a spudger (small electrostatic safe pry bar). Both of these tools are available for less than $5 on Amazon. You can even find kits that include spudger tools and sets of small screwdrivers for small electronics repair.

Targets to Test On
Once you’ve acquired some gear, you’ll need something to test and practice your skills on. My personal approach to hardware hacking is to only test or hack on devices I’m prepared to destroy. Accidentally frying or bricking a device is a common occurrence in hardware hacking and can even happen to the most experienced hackers (I have fried many devices in my days). However, there are plenty of affordable options available for testing purposes.
Option 1
Option 2
Nice-to-Have Gear for Hardware Hacking
This section covers some of the gear that I frequently use, but isn’t absolutely required. These tools make my life easier or come in handy from time to time. I won’t provide multiple options here, just a single link, but you can find all of these items from various places and manufacturers.
Third-Hand
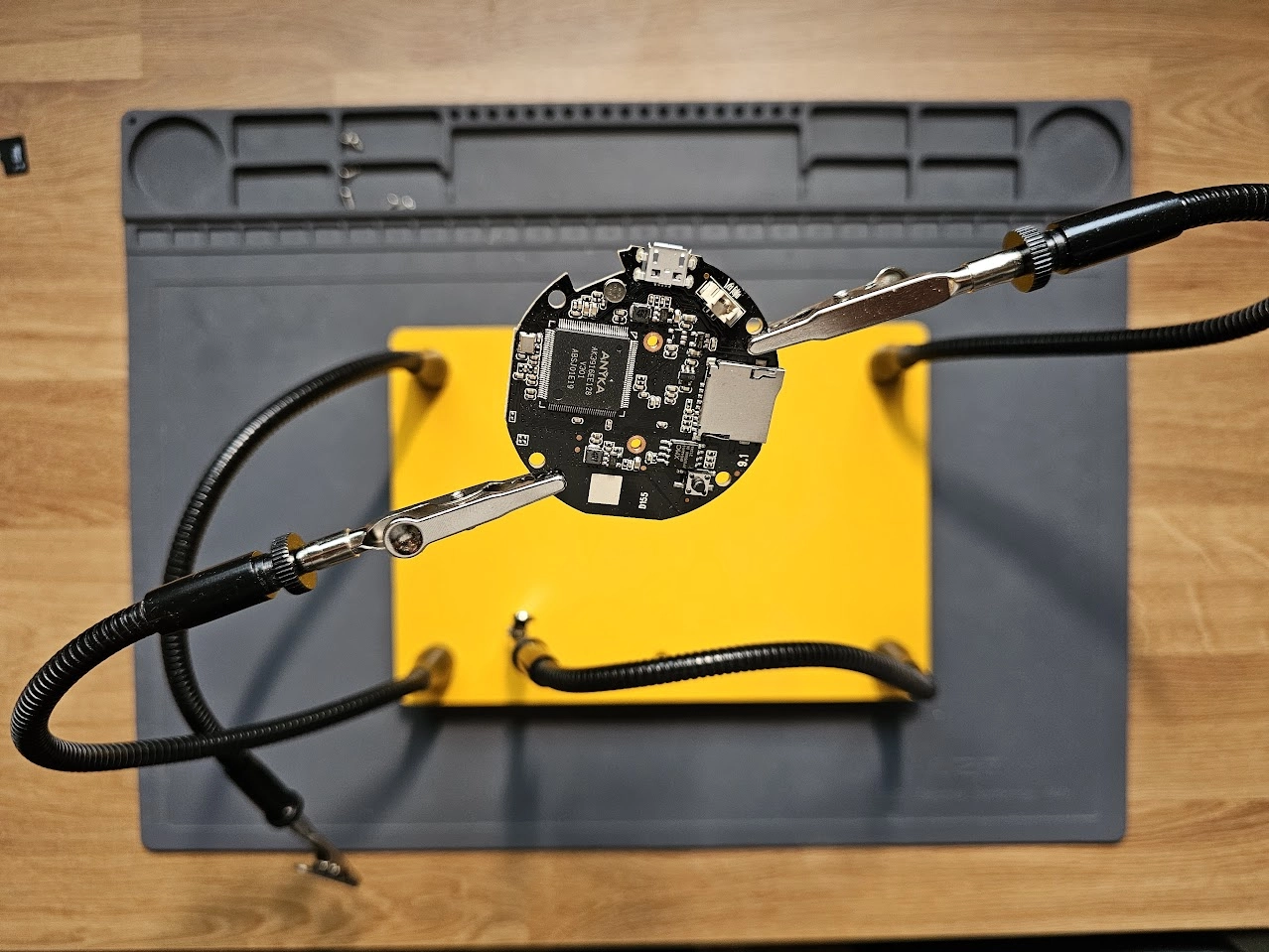
These tools are amazing for holding PCBs or other electronic components during testing or soldering, effectively freeing up your hands (hence the third-hand name). I use mine all the time. Here’s the link to the one I use: https://www.amazon.com/Helping-Soldering-Workshop-Non-slip-Weighted/dp/B07MDKXNPC/
Electrostatic Discharge (ESD) and Soldering Mat
Personally, I’m not too concerned about ESD prevention tools when I’m working on my own IoT devices. Instead, I adhere to a few key rules like avoiding direct contact with components and holding PCBs by their edges. Therefore, this mat isn’t primarily for ESD protection (although it’s a nice extra). I mainly use it to protect my desk and maintain organization. It features a holder for tools, screws, or other small electronic components. Additionally, it is also heat and burn resistant so you can solder on it. Link to the one I use: https://www.amazon.com/Anti-Static-Electronic-Wristband-Grounding-HPFIX/dp/B07X7VL7VR/
Soldering Iron
If you’re going to be working on commercial IoT devices, you’ll likely need to do some soldering to connect your tools to the pads, wires, pins lines etc., that you’ll want to interface with. I’ve always relied on Weller soldering irons and have had great luck with them. Link to the one I use: https://www.amazon.com/Weller-Digital-Soldering-Station-WLC100/dp/B000AS28UC/?th=1
Flash Programmer
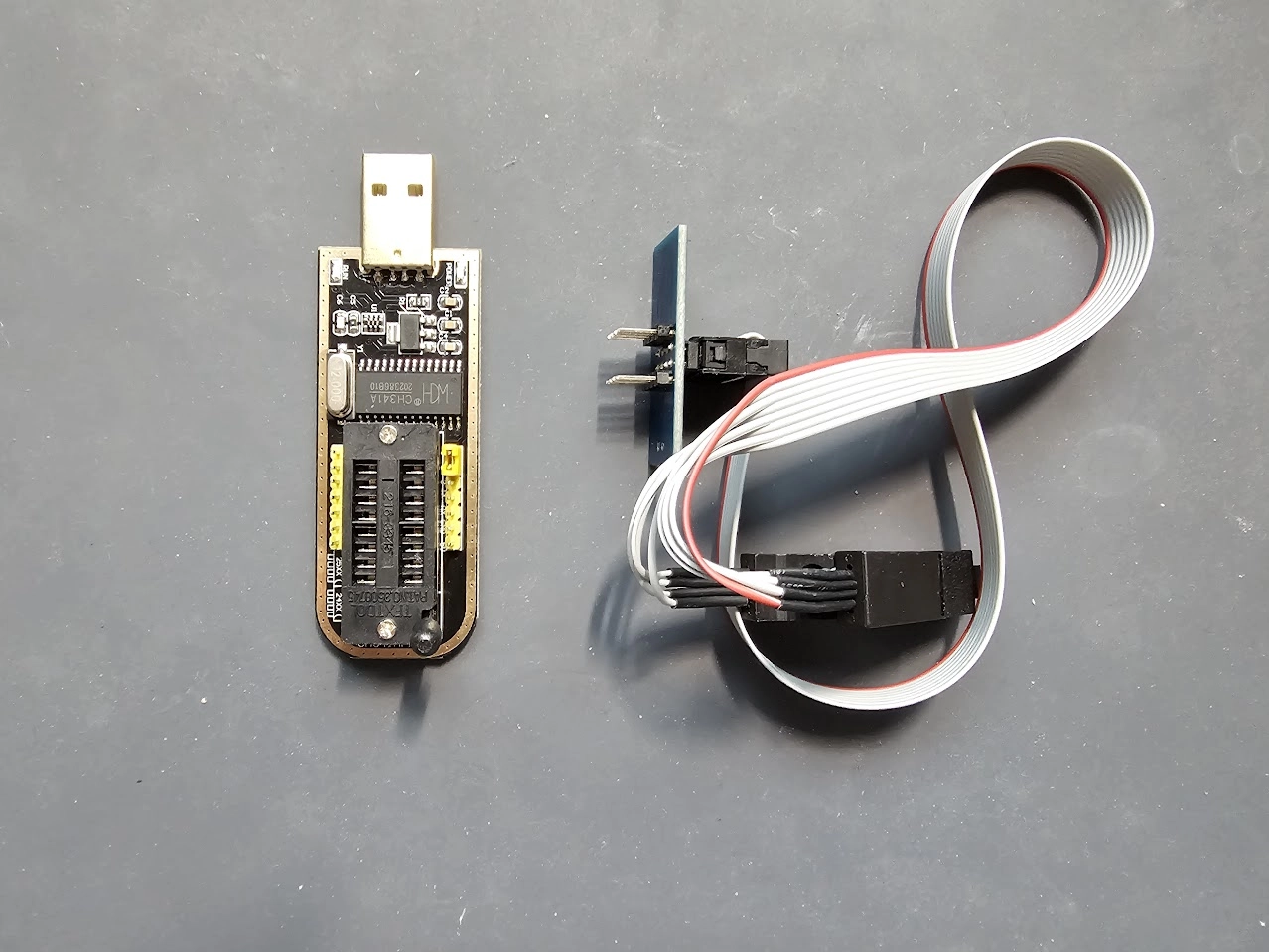
Many commercial IoT devices utilize cheap memory to store their firmware. Extracting this firmware or reprogramming the devices can be accomplished with a Flash programmer. These programmers are extremely helpful for dumping firmware or repairing a bricked device. The one we use in the course features a ch341a chipset and is manufactured by various companies. Here’s one from Amazon: https://www.amazon.com/KeeYees-SOIC8-EEPROM-CH341A-Programmer/dp/B07SHSL9X9
Another popular option for programming and reading a wider range of chip packages are the XGECU T48 or T56.
Test Clips and Extra Jumper Wires
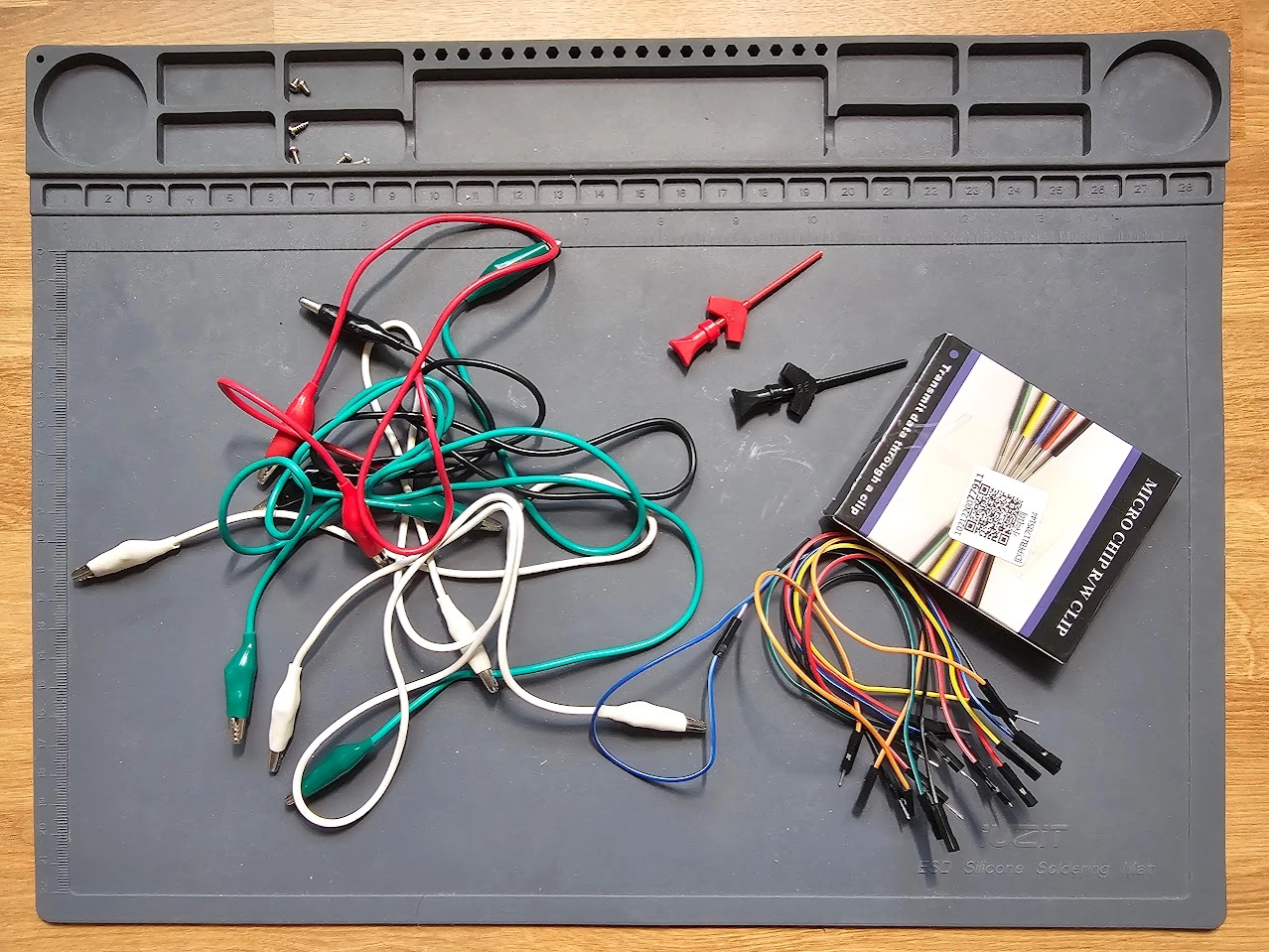
These always come in handy for me and can make your life easier. You can pick them up for cheap on Amazon.
https://www.amazon.com/Tegg-Electrical-Testing-Multimeter-Grabber/dp/B07NY73PQF
https://www.amazon.com/Adapter-oscilloscope-multimeter-Generator-Programmer/dp/B07XNQ8CQW
https://www.amazon.com/Elegoo-EL-CP-004-Multicolored-Breadboard-arduino/dp/B01EV70C78/
The Minimum Requirements to Follow Along with this Series
Raspberry Pi Zero 2w: This is the target we will be learning and testing on. If you don’t already have a micro SD card and something to read/write to it you’ll need to pick those up as well.
Raspi Zero 2W: https://www.amazon.com/Raspberry-Quad-core-Bluetooth-onboard-Antenna/dp/B0CCRP85TR/ **Note if you’re not comfortable soldering I suggest getting one with headers pre-soldered on like this one: https://www.amazon.com/Raspberry-Pre-Soldered-Quad-Core-Cortex-A53-Bluetooth/dp/B09LTDQY2Z/
SD Card Reader: https://www.amazon.com/Reader-Beikell-Connector-Memory-Adapter/dp/B0BGNZGDTC/?th=1
Micro SD Card: https://www.amazon.com/PNY-Elite-microSDHC-Memory-P-SDU32GU185GW-GE/dp/B07R8GVGN9/
USB to UART Serial Adapter: https://www.amazon.com/HiLetgo-CP2102-Converter-Adapter-Downloader/dp/B00LODGRV8/
Logic Analyzer: Two great options from Amazon, either one will work: https://www.amazon.com/HiLetgo-Analyzer-Ferrite-Channel-Arduino/dp/B077LSG5P2/ https://www.amazon.com/Comidox-Analyzer-Device-Channel-Arduino/dp/B07KW445DJ/
If you made it this far, thanks for reading along! In the rest of the series, we will start hacking away at our Raspberry Pi and learn about some common IoT hacking techniques. Part 2 is out now! Check out the All About UART article to learn how to set up your Raspberry Pi with the firmware.

About the Author: Andrew Bellini
My name is Andrew Bellini and I sometimes go as DigitalAndrew on social media. I’m an electrical engineer by trade with a bachelor’s degree in electrical engineering and am a licensed Professional Engineer (P. Eng) in Ontario, Canada. While my background and the majority of my career has been in electrical engineering, I am also an avid and passionate ethical hacker.
I am the instructor of our Beginner’s Guide to IoT and Hardware Hacking course and I also created the Practical IoT Pentest Associate (PIPA) certification.
In addition to my love for all things ethical hacking, cybersecurity, CTFs and tech I also am a dad, play guitar and am passionate about the outdoors and fishing.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.


