Overview
NoSQL databases, a term that stands for “Not Only SQL,” represent a shift from traditional relational databases. Unlike their SQL-based counterparts that rely heavily on tables and fixed schemas, NoSQL databases provide flexible storage mechanisms, catering to big data and real-time applications. They are characterized by their ability to scale out by distributing the database load across multiple hosts. Some popular NoSQL databases include MongoDB, CouchDB, and Cassandra, among others, are increasingly gaining adoption year by year
Basic NoSQL Syntax and Structure
To understand NoSQL injection, we need to grasp the basic structure and syntax of NoSQL databases. Since MongoDB is by far the most popular NoSQL database, we’ll use it for the examples in this post.
Documents and Collections
In MongoDB, data is stored as a document inside a collection. Generally speaking a document is like a record or row, and is a set of key-value pairs in a format somewhat similar to JSON objects. A collection is similar to a table that stores related documents. For example, we might have a collection called users and inside it the following document.
{
username: "jeremy",
email: "jeremy@tcm-sec.com",
role: "user",
hobbies: ["ice skating", "competitive programming"]
}Queries
MongoDB provides a method-based query language to insert and query this data. For example, to retrieve all the information about our user, Jeremy, we can use the following query:
db.users.insertOne({username: "jeremy", email: "jeremy@tcm-sec.com", role: "user", hobbies: ["ice skating", "competitive programming"]})
db.users.find({"username": "jeremy"})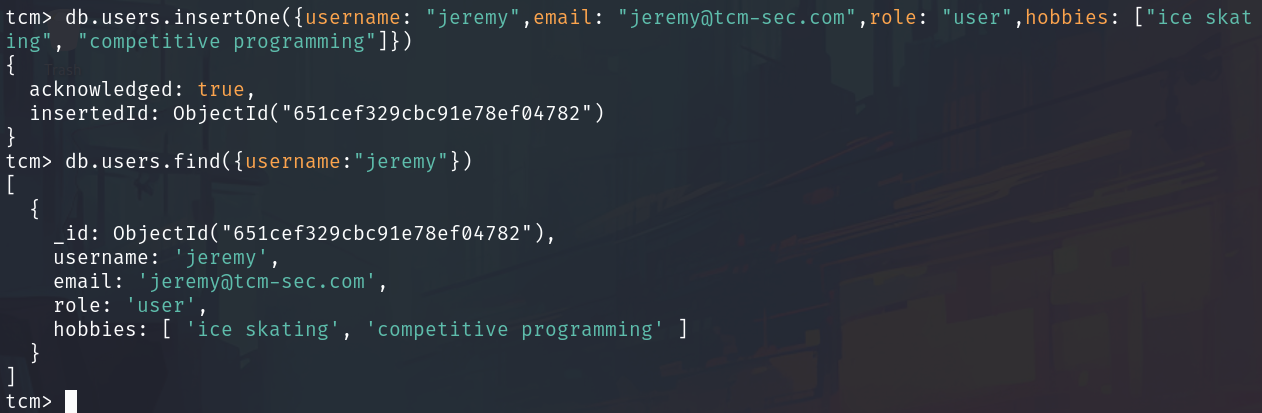
Operators
Operators can also be used when querying data, below are some examples however, this list is not exhaustive.
| $eq | equals |
| $ne | not equals |
| $gt | greater than |
| $gte | greater than or equal to |
| $regex | match regex |
For instance, if we want to fetch a user based on their hobbies, we can use the following query:
db.users.find({hobbies:{$eq:"competitive programming"}})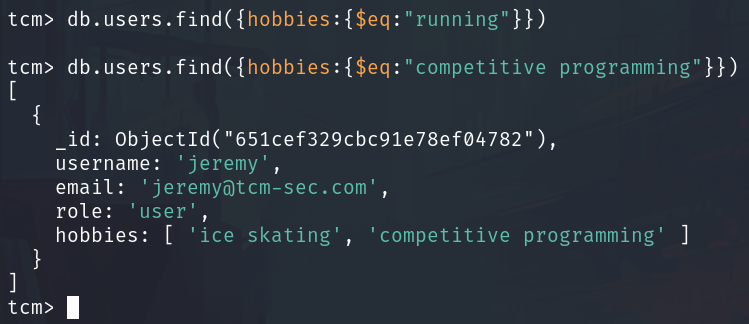
Basic Attack Example
NoSQL injection attacks target application code that improperly sanitizes user input when constructing database queries. Attackers can manipulate the logic of the query with their input.
For example, consider the following code that validates a user based on a username and password:
var user = db.users.find({"username": userInputUsername, "password": userInputPassword});If an attacker provides {"$gt": ""} as both the username and password, the query effectively becomes:
var user = db.users.find({"username": "administrator", "password": {"$gt": ""}});The "$gt" operator in MongoDB means “greater than.” By setting the value to an empty string, the attacker bypasses the authentication because the query will return the first user where the username and password are greater than an empty string.
Defenses
Protecting against NoSQL injection mostly involves being mindful of secure coding practices. However, a defense-in-depth approach is usually recommended and we can employ several security measures such as:
- Parameterized Queries: Just as in SQL databases, parameterized queries can help prevent injection attacks by ensuring that user input is always treated as data and not executable code.
- Input Validation: Always validate and sanitize user inputs. Utilize allow-lists to restrict inputs to known good values.
- Limit Database Permissions: Ensure that the application’s database user has the minimum necessary permissions. If the application only needs to read data, don’t give it write permissions.
- Database-specific Security Features: Most NoSQL databases have built-in security features. Familiarize yourself with these features and use them. For example, MongoDB offers client-side field-level encryption.
- Regular Updates: Always keep your NoSQL database and drivers updated. Many updates address security vulnerabilities.
Conclusion
While NoSQL databases offer flexibility and scalability, they also introduce their own set of security challenges. Understanding the basics of NoSQL syntax, being aware of potential injection payloads, and adopting proper defensive measures are critical to maintaining a secure application environment.

About the Author: Alex Olsen
Alex is a Web Application Security specialist with experience working across multiple sectors, from single-developer applications all the way up to enterprise web apps with tens of millions of users. He enjoys building applications almost as much as breaking them and has spent many years supporting the shift-left movement by teaching developers, infrastructure engineers, architects, and anyone who would listen about cybersecurity. He created many of the web hacking courses in TCM Security Academy, as well as the PJWT and PWPT certifications.
Alex holds a Master’s Degree in Computing, as well as the PNPT, CEH, and OSCP certifications.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

