What is Mass Assignment?
Mass assignment is a feature, and it makes our lives easier when trying to map input passed from the front end to the back end. By automatically assigning values to the properties of an object, we save some time in development and gain some flexibility. However, if not handled properly, it can also introduce security vulnerabilities.
A Common Scenario
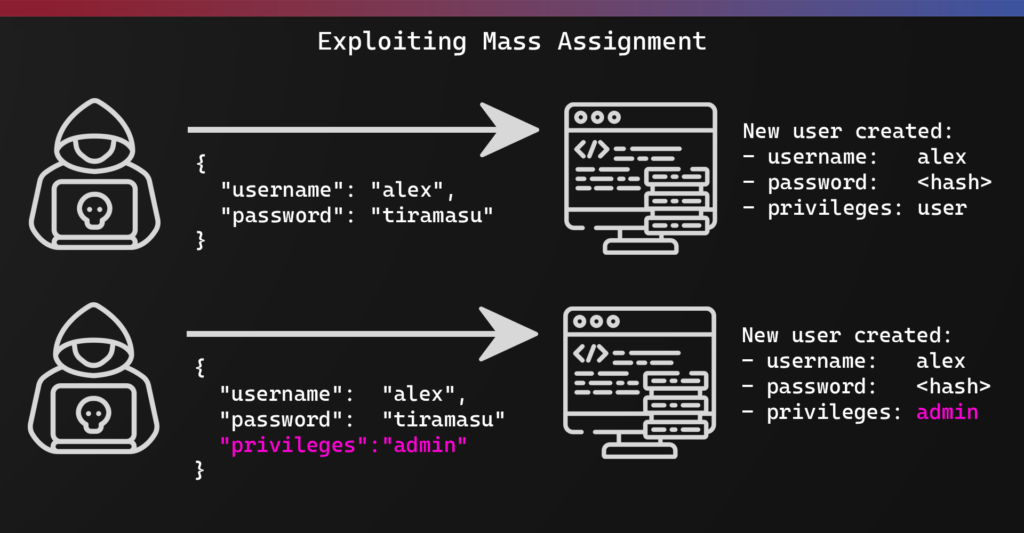
When a web application takes data from a form submission and maps it directly to an object’s properties without validating or filtering, an attacker may exploit this by additional or unexpected fields in the form. This can potentially overwrite or manipulate sensitive data.
In this example, we have a simple user model:
const UserSchema = new Schema({
username: {
type: String,
required: true,
},
password: {
type: String,
required: true,
},
privileges: {
type: String,
required: true,
default: "user",
},
});
When a new user is created, the expectation is that the username and password will be submitted from the user.
An insecure way of creating the new user, using Mass Assignment, would be:
app.post('/register', (req, res) => {
const newUser = new User({ ...req.body });
Here we are using the spread operator. It is used to expand iterable elements into arrays. So in this case, all of the key-value pairs from the re.body will be passed into the User constructor.
A malicious payload would look like this:
{
"username": "alex",
"password": "tiramasu",
"privileges": "admin"
}

A secure way to process this would be something like:
app.post("/register", async (req, res) => {
const { username, password } = req.body;
const newUser = new User({ username, password });
In the second version of our code, we are being explicit about what fields we allow to be passed from the user, and in our model, we are setting all privileges for new users to “user” by default.
Some other examples of sensitive fields that may be impacted are:
- Verified
- Balance
- Status
- isAdmin
- isSubscriber
- etc
What About Web Frameworks?
Mass Assignment is commonplace in frameworks too as many of them support Mass Assignment. It’s sometimes also referred to as autobinding. Whilst this is a great feature, it can easily become a security vulnerability when not used appropriately.
Vulnerable code that allows for unintended fields:
@app.route('/users', methods=['POST'])
def create_user():
user_data = request.form
new_user = User(**user_data)
Secure code that extracts only the fields we want to process from the request:
def create_user():
username = request.form.get('username')
password = request.form.get('password')
new_user = User(username=username, password=password)
Detecting Mass Assignment
Discovery of Mass Assignment vulnerabilities can be tricky, though easier if you’re able to carry out code review. I recommend reading through the OWASP WSTG for Testing Mass Assignment to learn more.

About the Author: Alex Olsen
Alex is a Web Application Security specialist with experience working across multiple sectors, from single-developer applications all the way up to enterprise web apps with tens of millions of users. He enjoys building applications almost as much as breaking them and has spent many years supporting the shift-left movement by teaching developers, infrastructure engineers, architects, and anyone who would listen about cybersecurity. He created many of the web hacking courses in TCM Security Academy, as well as the PWPA and PWPP certifications.
Alex holds a Master’s Degree in Computing, as well as the PNPT, CEH, and OSCP certifications.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.