Overview
Having a flexible and isolated environment doesn’t just save us time, it can also be crucial for testing. Whether you’re deploying a real-world application stack for research, testing exploits, or setting up vulnerable apps for practice, you need a system that’s both adaptable and reliable. Enter Docker.
Docker makes it easier than ever to deploy, scale, and manage applications in various environments. Today we’ll take a look at why Docker is a staple in my day to day tools, demonstrate its utility for pentesting and provide a quick-start guide to setting up labs and testing environments.
What is Docker?
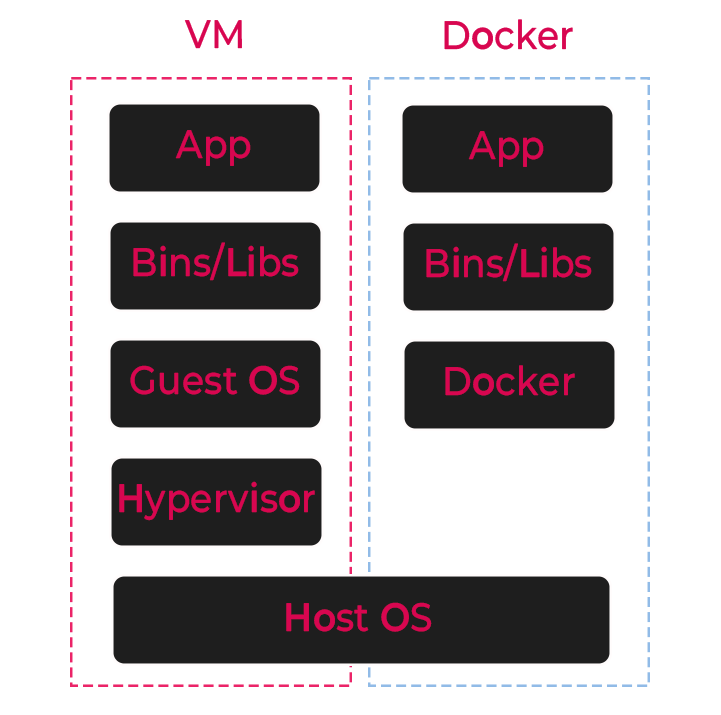
Docker is a platform that uses containerization technology to package an application and its dependencies into a single container. Unlike traditional virtual machines (VMs) that virtualize the entire OS, Docker containers share the same OS kernel and isolate the application processes from each other.
So what are the advantages over traditional VMs?
- Lightweight: Containers take up less space than VMs.
- Fast: Docker containers can start almost instantly due to less overhead.
- Consistent: The application will run the same regardless of where the Docker container is run.
Using Docker for Web App Pentesting
There are many reasons to use Docker, but for Web Application Penetration Testers in particular, it allows us to:
- Quickly deploy applications or targets for testing and research
- Quickly deploy specific applications (with specific versions running on specific servers) to test payloads
- Setup vulnerable labs for study
- Building PoCs or CTFs
For example, to run DVWA:
docker pull vulnerables/web-dvwa
docker run -d -p 80:80 vulnerables/web-dvwaWe can customize this even further so that when we’re testing exploits on specific versions of web applications or a particular tech stack, we can quickly create the environment we need.
- Dockerfiles: These are scripts containing instructions to build a Docker image. As pentesters, we can use Dockerfiles to recreate specific application environments, right down to the exact versions and configurations.
- Docker Compose: For more complex setups involving multiple containers (like an app server and a separate database), Docker Compose lets us define multi-container applications in a single docker-compose.yml file.
Finally, Docker gives us some isolation and safety so that when we are testing potentially volatile payloads we can do it without impacting production systems or users.
Getting Started with Docker
Installation: Docker is available for Linux, macOS, and Windows. Follow the official Docker documentation for installation instructions specific to your OS. If you are running Kali like most Pentesters, you can install easily with `apt`.
sudo apt install docker.io# Download a Docker image
docker pull [image-name]
# Run a container from an image
docker run [options] [image-name]
# List running containers
docker ps
# Stop a running container
docker stop [container-id]Conclusion
Docker provides web application penetration testers with a flexible, efficient, and safe way to set up testing environments. From running vulnerable labs to customizing intricate application stacks, Docker simplifies the process, allowing testers to focus on what we do best: finding vulnerabilities and ensuring web application security.

About the Author: Alex Olsen
Alex is a Web Application Security specialist with experience working across multiple sectors, from single-developer applications all the way up to enterprise web apps with tens of millions of users. He enjoys building applications almost as much as breaking them and has spent many years supporting the shift-left movement by teaching developers, infrastructure engineers, architects, and anyone who would listen about cybersecurity. He created many of the web hacking courses in TCM Security Academy, as well as the PJWT and PWPT certifications.
Alex holds a Master’s Degree in Computing, as well as the PNPT, CEH, and OSCP certifications.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

