Why Linux Skills are Invaluable for Pentesters
Linux, an open-source operating system, forms the backbone of modern infrastructure. Being comfortable with Linux thus opens up a vast array of systems and servers for you to better be able to understand, evaluate and attack. More specifically, the following factors make Linux indispensable:
- Security Tools: Many security tools are Linux-based. Familiarity with Linux allows you to utilize these tools and potentially customize or automate.
- Flexibility and Control: Linux offers the user unparalleled control over the system. As a pentester, this flexibility allows you to tailor your environment to your needs and develop custom scripts or programs to automate or expedite your testing process.
- Open-source Nature: The open-source nature of Linux means that a vast community of developers is continually contributing to its development and security. This results in an ever-evolving platform that can cope with the ever-evolving world of cybersecurity, including flavours that are specifically tailored to security.
Practical Advice for Learning Linux
Learning Linux can seem like a daunting task due to its seemingly complex command-line interface and vast capabilities. Don’t worry, though; with the right approach, anyone can become proficient. Here’s a roadmap to help you navigate your Linux learning journey:
1. Start with the Basics
Before diving into the advanced aspects of Linux, it’s crucial to grasp the basics. Start by installing a beginner-friendly Linux distribution, such as Ubuntu, Mint or Kali, in a virtual environment like VirtualBox or VMware. Learn to navigate the graphical user interface first, play around with basic settings, browse internet, install some software and understand where your files live. This will help you get comfortable with the overall Linux environment.
2. Learn the Command-Line
As a pentester, you’ll be spending a lot of time with the terminal, Linux’s command-line interface. The terminal might seem intimidating at first, but it’s a powerful tool once you get the hang of it. Start with basic commands like:
- ls
- cd
- mv
- cp
- whoami
- rm
Then gradually move onto advanced commands and utilities like ‘grep’ (search), ‘chmod’ (change file permissions), ‘sudo’ (superuser do), and ‘ssh’ (secure shell). Resources such as ‘man’ (manual) pages in Linux or online guides can be incredibly helpful during this phase.
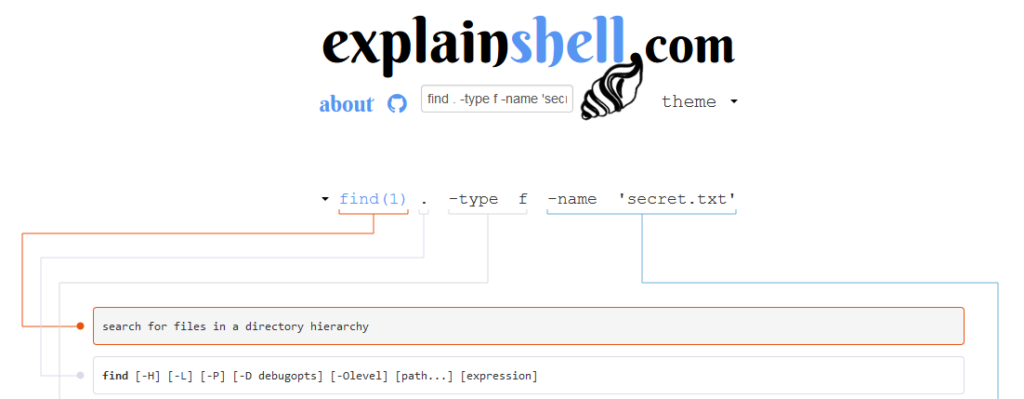
If you see a command and don’t know what it does, try copying it into explainshell.com which will break it down and explain each part.
3. Use Linux Regularly
Consistency is the key to mastering Linux. Whether it’s executing commands, installing packages, or troubleshooting issues, every interaction you have with Linux improves your understanding of the system. One excellent way to practice is to make Linux your daily driver, i.e., use it for everyday tasks. This not only aids in familiarization but also exposes you to various scenarios where you’d have to ‘think in Linux’ to solve problems.
4. Take a Course
There are many courses and materials out there to learn from. If you want a structured approach from start to finish then head over to the TCM Academy and check out the FREE Linux 100: Foundations course.
5. Learn About System and Network Administration
While being comfortable with the Linux terminal is important, understanding system and network administration within a Linux environment is equally crucial. Learn how to manage user permissions, configure network settings, schedule tasks using ‘cron,’ and understand system logs. These skills will help you understand the broader context of the systems you’ll be pentesting.
6. Learn Shell Scripting
Shell scripting is a powerful tool that allows you to automate repetitive tasks and create new tools for your needs. Start with simple scripts and gradually work your way up to more complex ones. This not only boosts your productivity but also deepens your understanding of Linux.
7. Use Linux in Pentesting
Finally, it’s essential to learn how to use Linux in a pentesting environment. Start using pentesting tools that run on Linux and understand how they interact with the system. Also, consider participating in capture-the-flag (CTF) challenges or using platforms like HackTheBox and TryHackMe.
Linux is an invaluable tool in any pentester’s arsenal, providing the flexibility, control, and rich array of security tools needed to succeed in this field. As you embark on your journey to learn Linux, remember that patience and consistent practice are your allies. Over time, you’ll find that the command-line isn’t so scary, and Linux isn’t so mysterious.

About the Author: Alex Olsen
Alex is a Web Application Security specialist with experience working across multiple sectors, from single-developer applications all the way up to enterprise web apps with tens of millions of users. He enjoys building applications almost as much as breaking them and has spent many years supporting the shift-left movement by teaching developers, infrastructure engineers, architects, and anyone who would listen about cybersecurity. He created many of the web hacking courses in TCM Security Academy, as well as the PWPA and PWPP certifications.
Alex holds a Master’s Degree in Computing, as well as the PNPT, CEH, and OSCP certifications.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.