Introduction
Fed up being slowed down by simple checks and functionality? Even seemingly simple CSRF tokens can get in the way of a straight-forward brute-force attack! Enter BURP Suite Macros, an indispensable tool that can be used to efficiently handle these scenarios and improve our workflow. Today we’ll gain a practical understanding of how to circumvent issues with single-use CSRF tokens and also delve into mass assignment fuzzing, all the while harnessing the power of BURP Suite Macros.
Lab Setup
The lab demonstrated in this post is freely available at https://github.com/AppSecExplained/ctf-burp-macros. To setup on Kali you simply need to run:
sudo apt install git
sudo apt install docker.io
sudo apt install docker-compose
git clone https://github.com/AppSecExplained/ctf-burp-macros.git
cd ctf-burp-macros
sudo docker-compose upBrowse to http://localhost and you’re good to go.
Handling Single-Use CSRF Tokens
For our first practical lab, we want to use brute-force against this login form however, it makes use of single-use CSRF tokens. In many systems, particularly ones that deal with sensitive operations (like changing passwords or modifying user data), it’s a best practice to make CSRF tokens single-use. That means once a CSRF token has been used, it becomes invalid and a new token is issued for the next request.
However, this isn’t always implemented because of user experience concerns. If you enforce strict single-use CSRF tokens, and a user has multiple tabs or windows open, they might encounter a situation where a CSRF token in one tab is invalidated by a request in another tab. This can lead to “unexpected” errors, where a user doesn’t understand why their legitimate action was rejected.
If we attempt our attack now, we simply get “Invalid token” in each response.
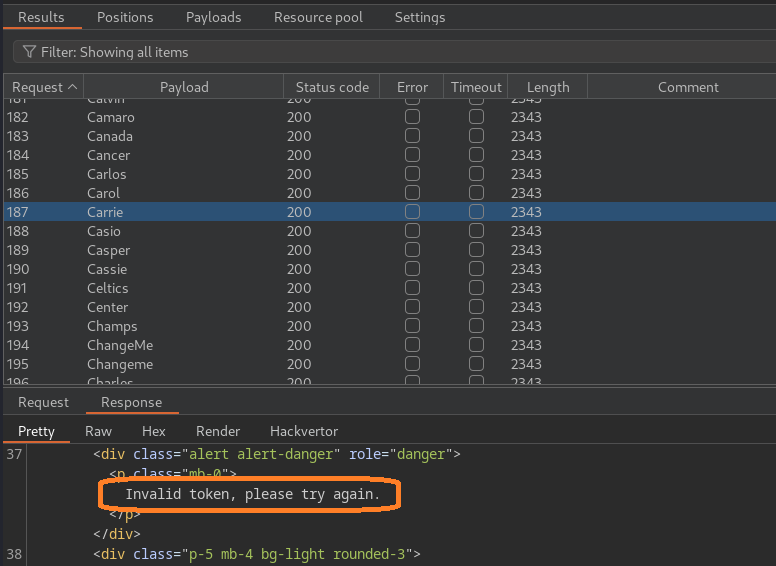
To be able to brute-force this form, we need to submit a new token with each request, so our attack pattern will look like this:
- Send a GET request to /csrf.php
- Extract the token from the page
- Send a POST request to /csrf.php with the extracted token
Steps 1 and 2 are made much easier with macros.
To set this up we navigate to Burp > Settings > Sessions > Macros.
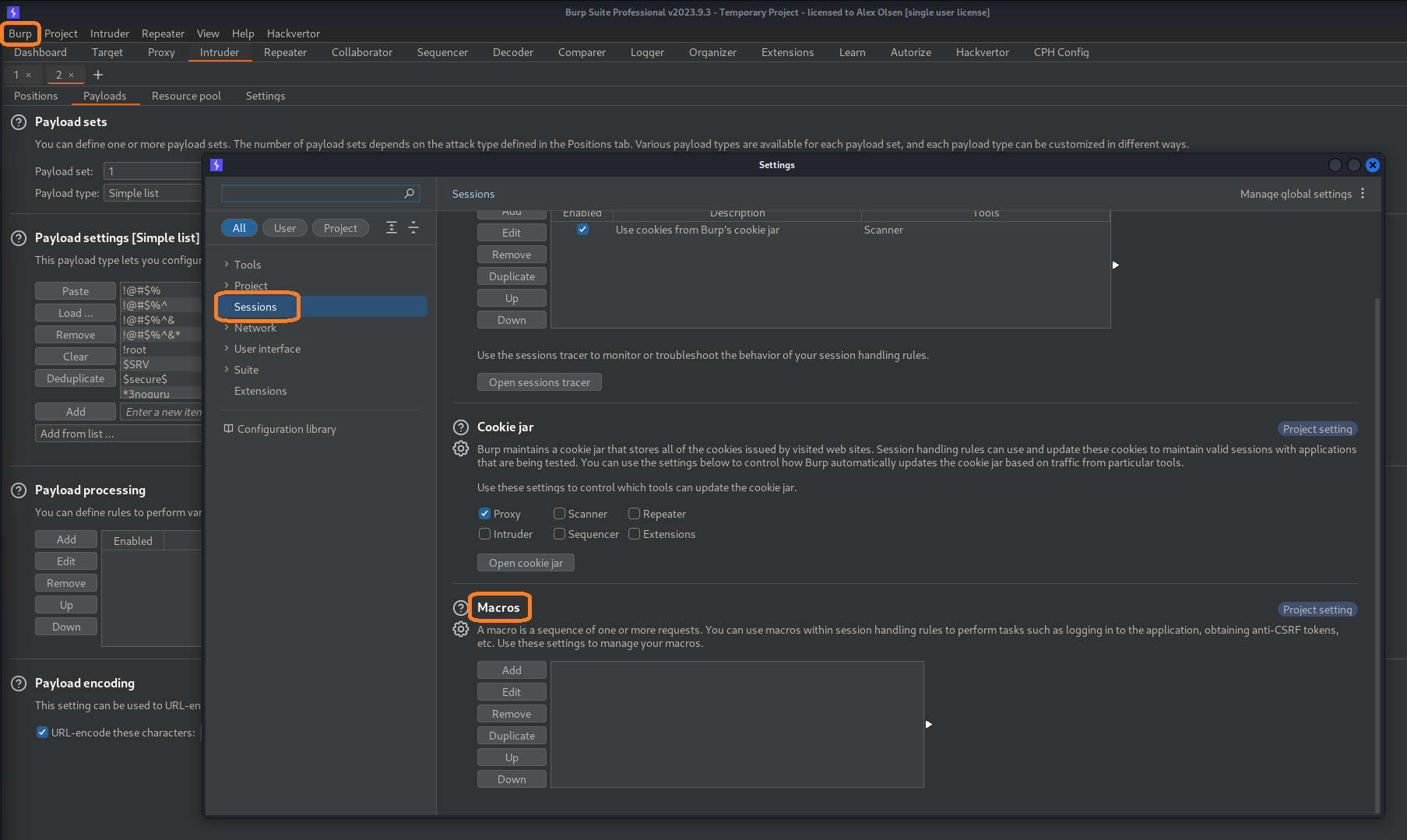
Click “Add” and find our GET /csrf.php request which contains the CSRF token in the response.
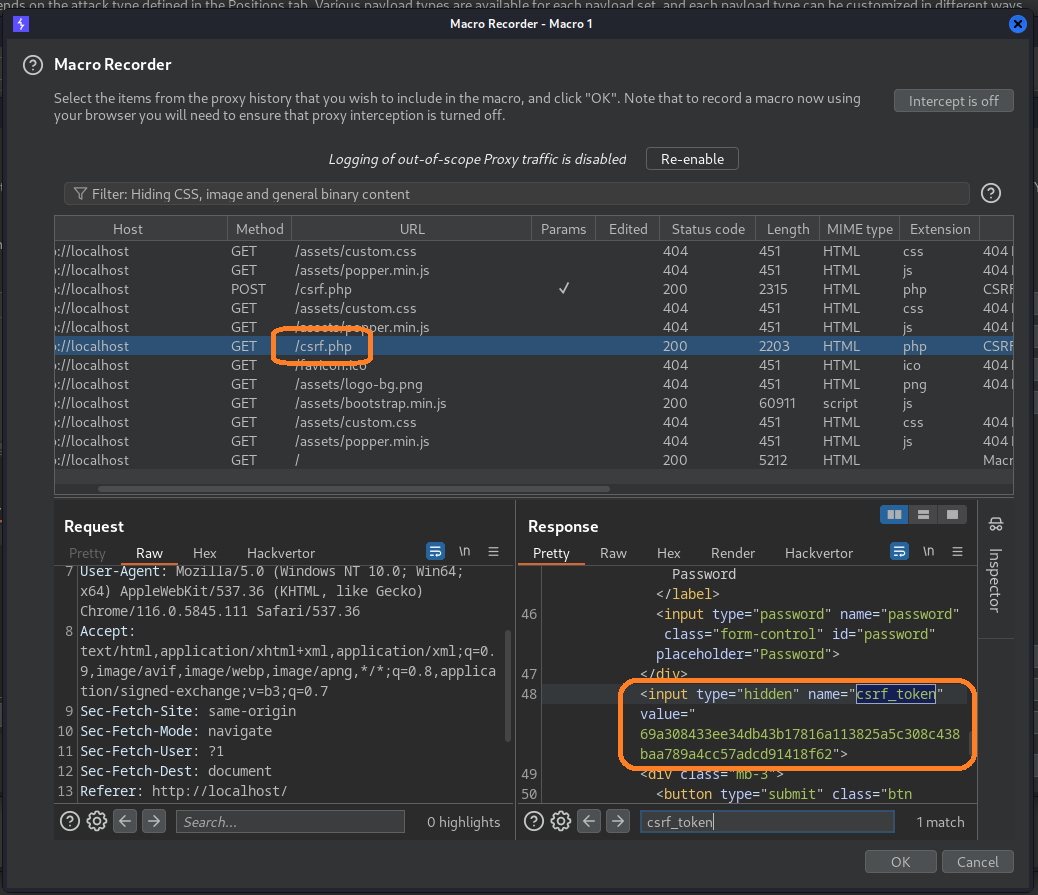
Click “OK”, change “Macro description” to something descriptive, and “OK” again.
Now we need to add a session handling rule, so from the same settings panel, scroll up to “Session handling rules” and Click “Add”.
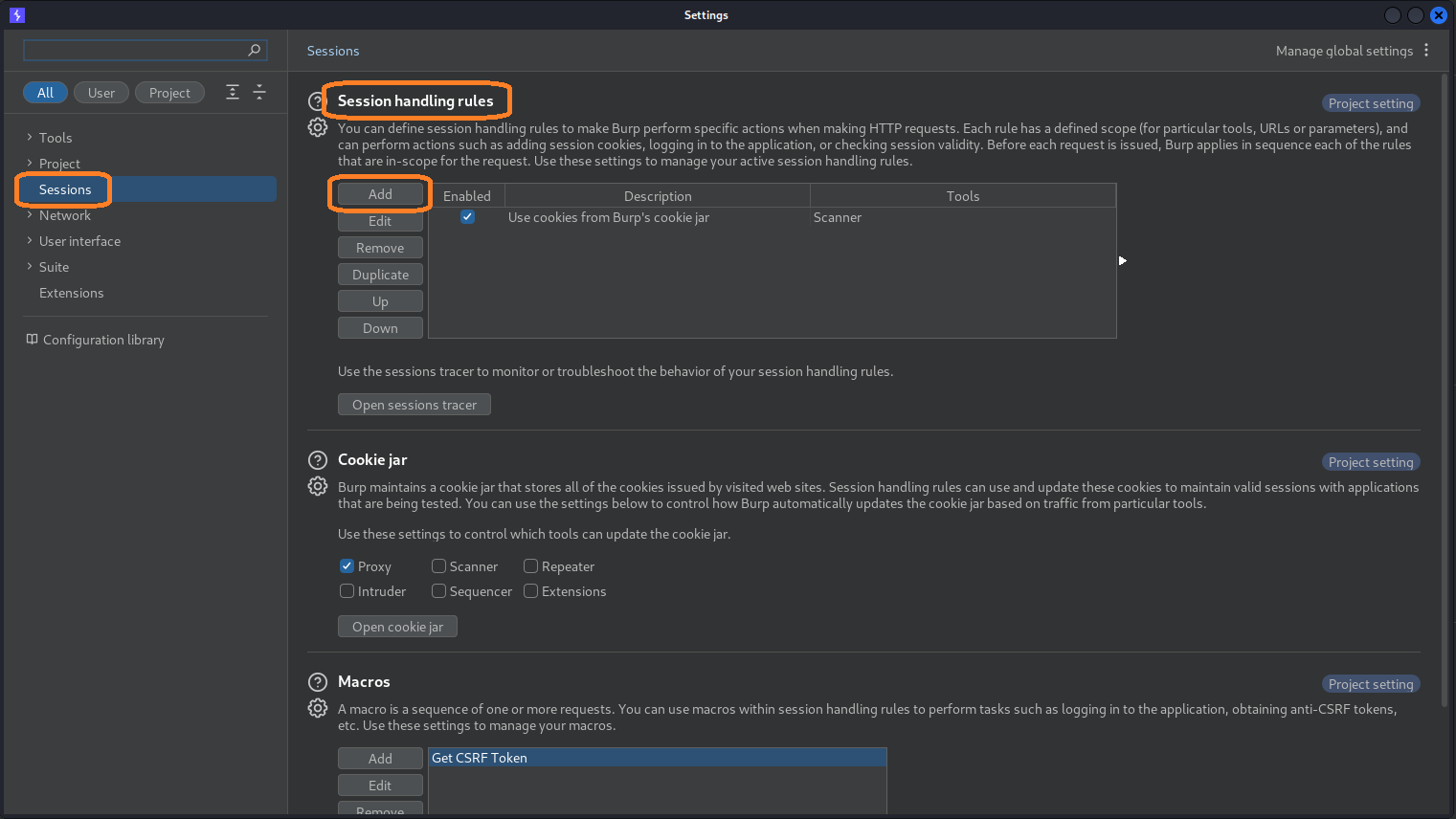
Give the rule a useful description and under the “Rule actions” click “Add” and select “Run a macro”. Select your macro and then click “Ok”.
Select “Scope”, uncheck everything except Repeater and Intruder. Under “URL Scope” let’s go ahead and add “http://localhost/csrf.php” so our macro doesn’t interfere with other requests.
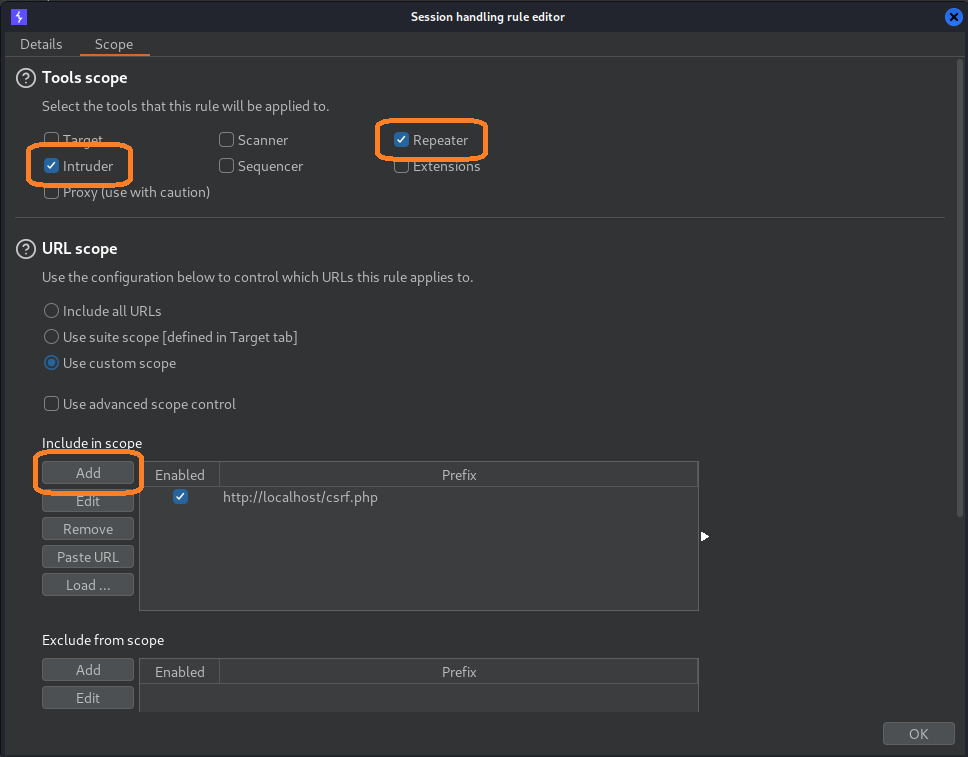
Click “OK” and exit out of the settings panel.
Let’s go ahead and test this in repeater, we should be able to send multiple requests and only receive an invalid credentials error message rather than an invalid token.
Request 1:

Request 2:
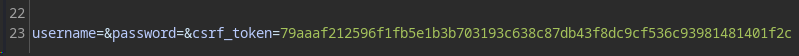
As expected, the token is automatically updated and we receive the invalid credentials error, perfect! Let’s move onto intruder.
We set the username to jeremy, make sure to select the our marked areas and set the attack type as “Cluster bomb”.
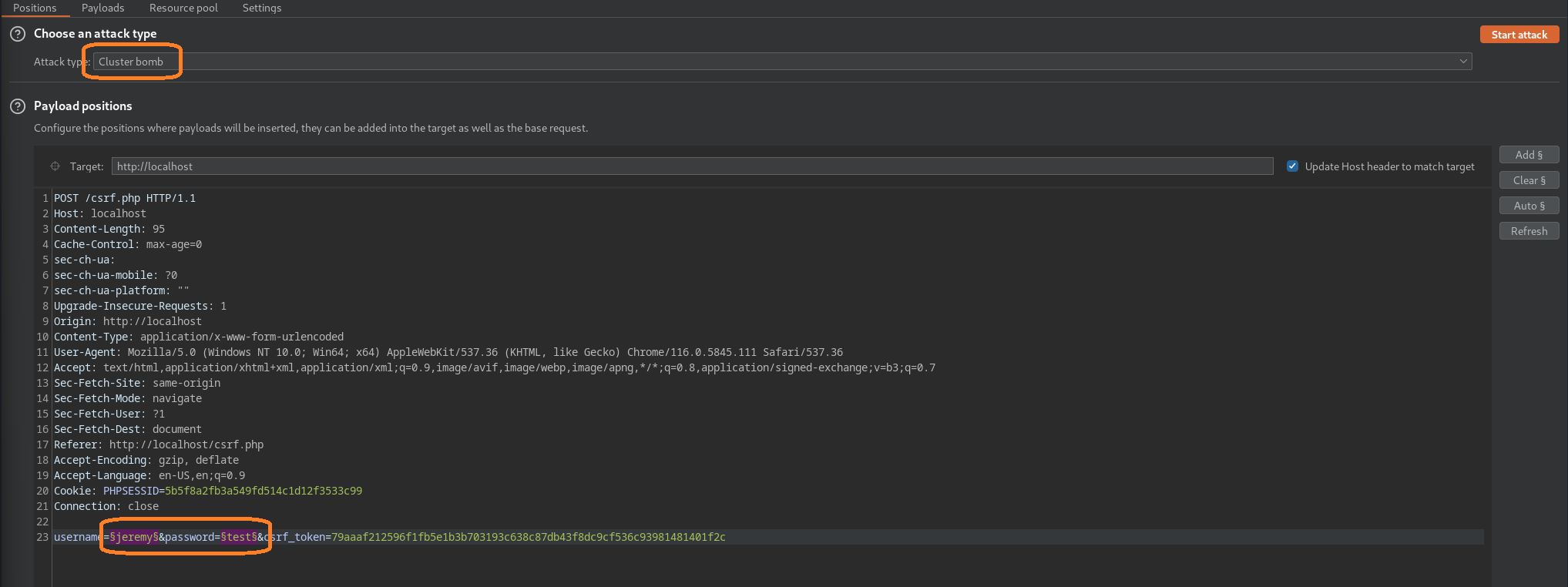
Click the “Payloads” tab, for payload set 1 we can choose “Simple list” and just add “jeremy” as in this situation we are only attacking a single account. For payload set 2 choose a list of common passwords you want to try (I used the built in password list, but something like xato-net-10-million-passwords-1000.txt from seclists should do the trick).
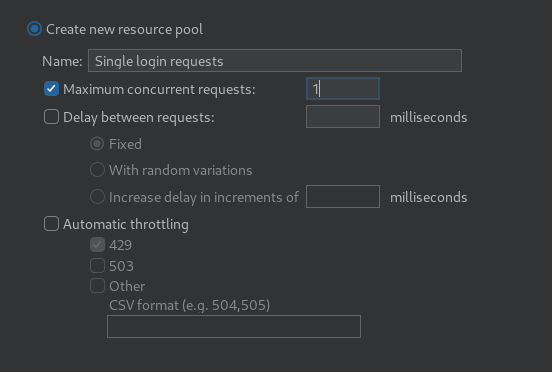
There is one more important thing to consider here, Intruder by default will send concurrent requests and since we only have one valid CSRF token at a time, we need to ensure they are used in order.
Click “Resource pool” and “Create new resource pool”, give it a logical name and set the “Maximum concurrent requests” to “1”.
Now we are ready to start and we click “Start attack”.
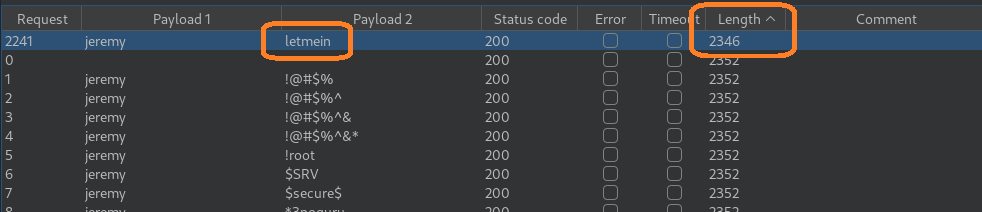
If we order the results by “Length” by clicking on the column title, we can see a result that is different from the rest and this indicates we’ve found the correct password.
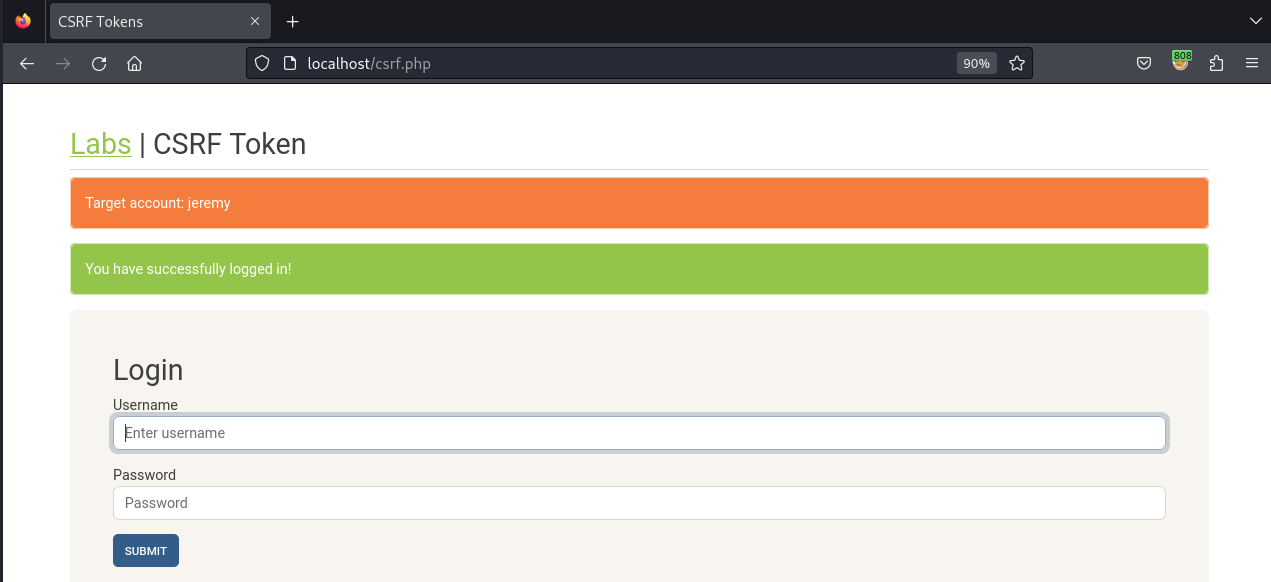
We now head back to the application and verify our findings!
Mass Assignment Fuzzing
In our next lab we will use a Macro to send a request to an endpoint that’s only accessible by admins to verify whether or not we have successfully created an admin account.
Before we begin, if you’re unfamiliar with the mass assignment vulnerability, you can find an introduction here.
After stepping through, creating an account and logging in, we find that there are four parts to this application.
- The registration page
- The login page
- The post-login welcome page
- The admin page
We will go ahead and test this application for mass assignment, supported by BURP Suite Macros, our attack will look like:
- Create a list of potential payloads that might give the account higher level privileges upon creation based on common words
- Use intruder to create accounts with those payloads
- Use intruder and a macro to login to the account and check our access to the admin endpoint.
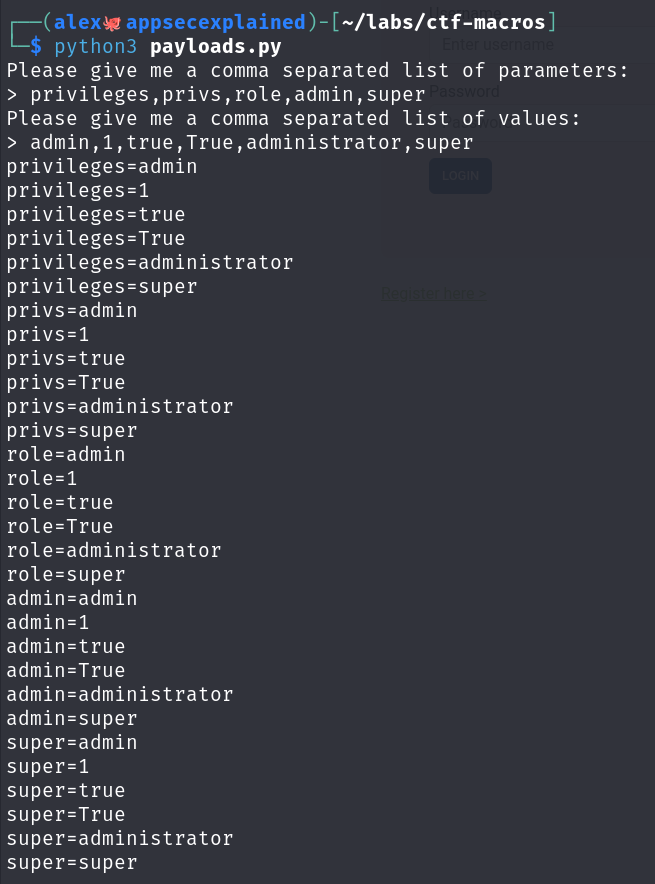
To create our payloads, I wrote a quick python script.
def generate_payloads(param_list, value_list):
result = []
for param in param_list:
for value in value_list:
result.append(f"{param}={value}")
return result
if __name__ == "__main__":
params_input = input("Please give me a comma separated list of parameters:n> ").split(',')
values_input = input("Please give me a comma separated list of values:n> ").split(', ')
payloads = generate_payloads(params_input, values_input)
for payload in payloads:
print(payload)Running this gives us a list of payloads to try.
It’s worth nothing at this point that we could reduce the number of accounts created if we passed more unique parameters with each request. For example ‘username=alex&password=alex&admin=true&role=true&super=true&privs=true’ would also be a valid attack. Each application will handle these attacks differently so I encourage you to experiment.
Let’s create our accounts with Intruder and then setup our macro to check their privileges. We start by sending a POST to /register.php request to Intruder.
We add ‘&payload’ to the end of the body, set the attack type to Pitchfork and mark the username and payload fields.
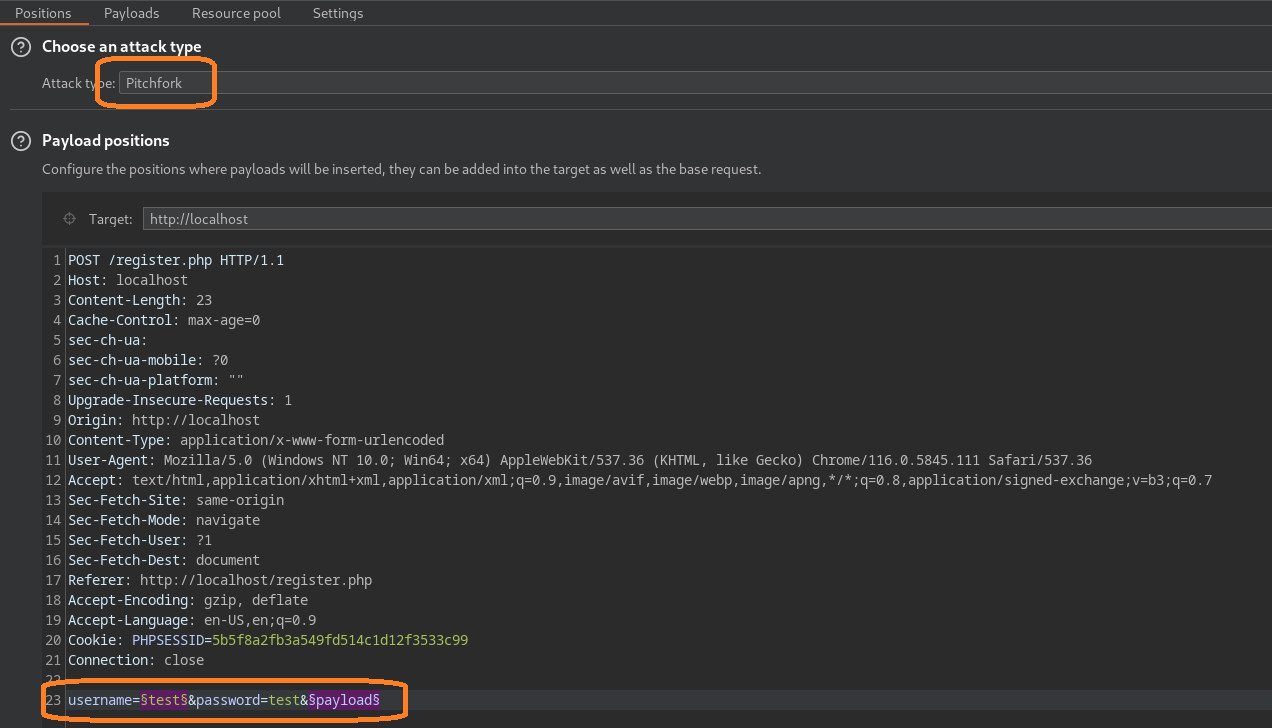
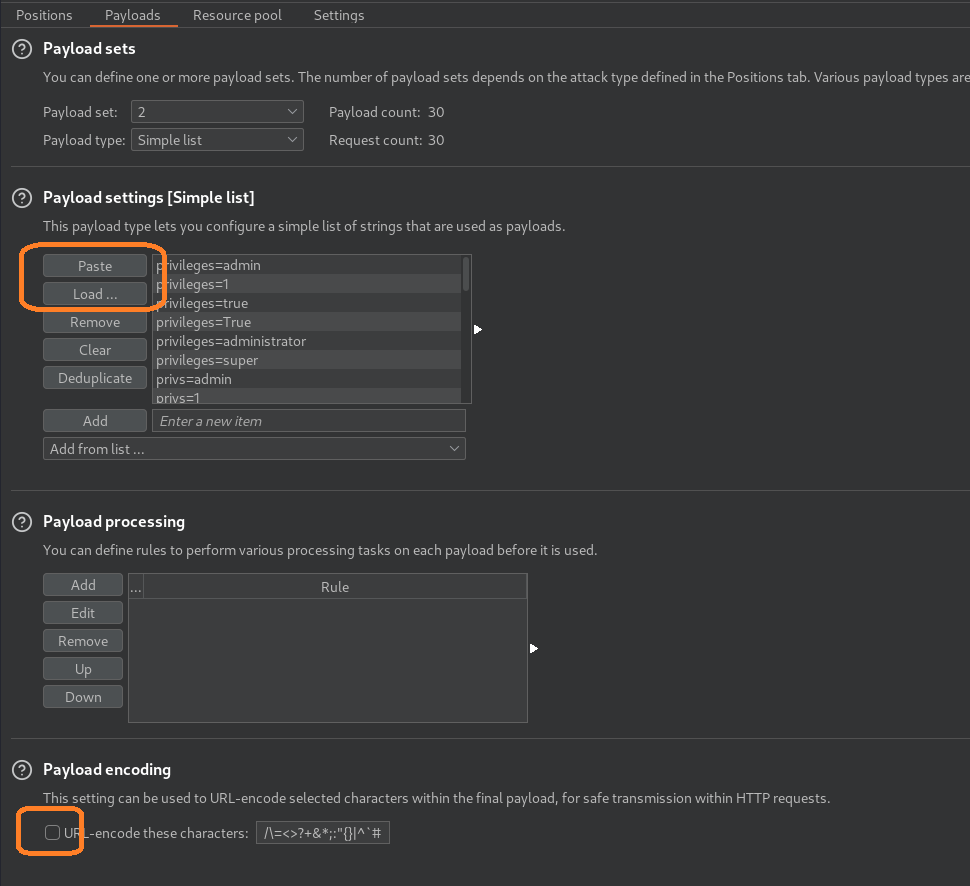
For the first payload, we can just set the payload type to “Numbers”. Now we don’t know how many payloads we have yet so switch to payload set 2, keep the payload type as “Simple list”, and paste or load in the payloads we generated earlier. Make sure to uncheck “Payload encoding” at the bottom otherwise our ‘=’ will be encoded and potentially not interpreted correctly.
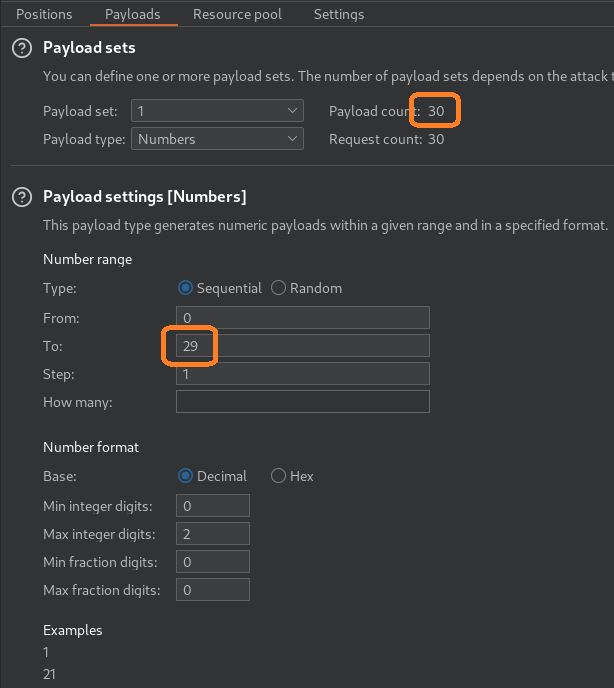
Now the payload count is 30, so we will switch back to payload set 1, and change the “To” in the number range to 29. This will give us 30 payloads (0 – 29) respectively.
Click “Start attack” and we should see that we have created a number of accounts successfully. Stage 1 complete, let’s setup our macro.
Navigate to Burp > Settings > Sessions > Macros.
Click “Add” and find the GET request to /admin.php. Click “OK”, give it a descriptive name, and then “OK” again.
Scroll up to “Session handling rules”, click “Add”, give it a descriptive name, and under “Rule actions” click “Add” and “Run post-request macro”. This will run our GET request macro to /admin.php after authenticating and should give us a successful result if the account we authenticated as is an administrator.
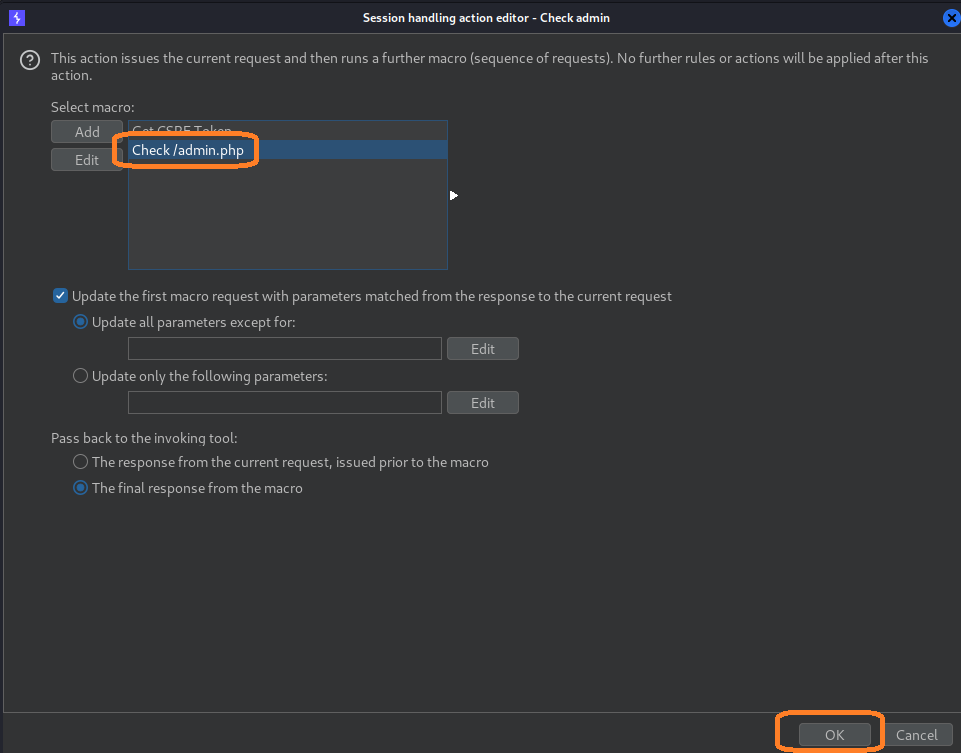
Select the macro, and click “OK”, then click “Scope”. We will once again restrict this to Intruder and Repeater but apply it to all URLs. Just be sure to switch it off again once you’re done.

Click “OK” and exit out of the settings panel. Find or create a POST request to /login.php and send it to Intruder.
Mark the username, keep the attack as “Sniper” and the password as “test” or the value you used to create the accounts with. Navigate to “Payloads” and set the payload type to “Numbers” once again, and use the same values as before.
Navigate to “Resource pool” and once again select the single concurrent requests we setup earlier rather than the default pool. Click “Start attack”.
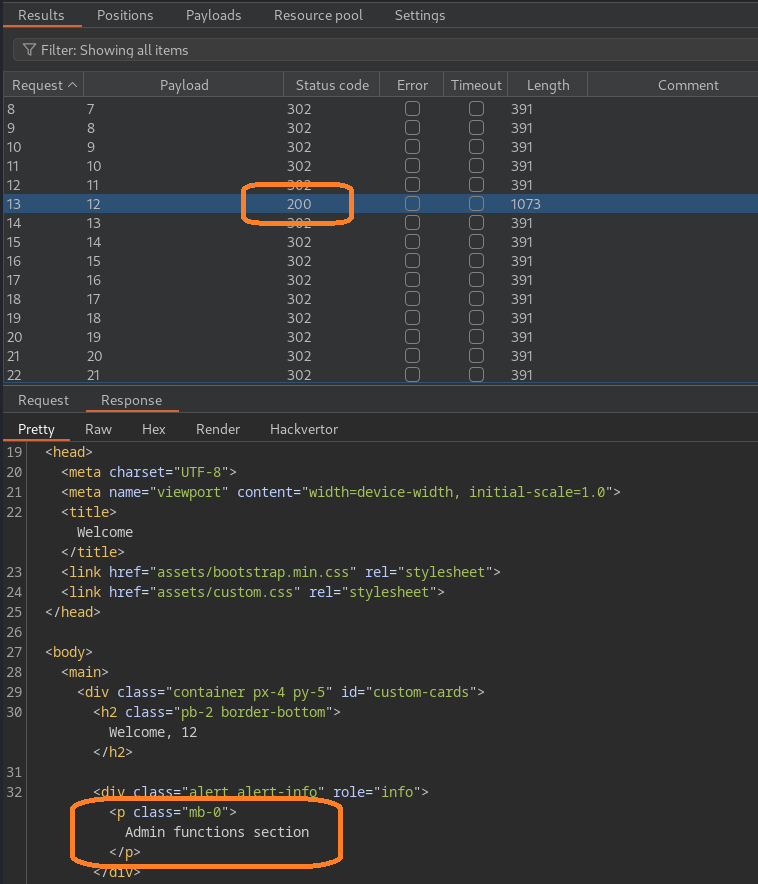
We can see that account 12 was created successfully with admin privileges and if we reference back to our previous attack, we can see that the ‘role=admin’ payload was successful.
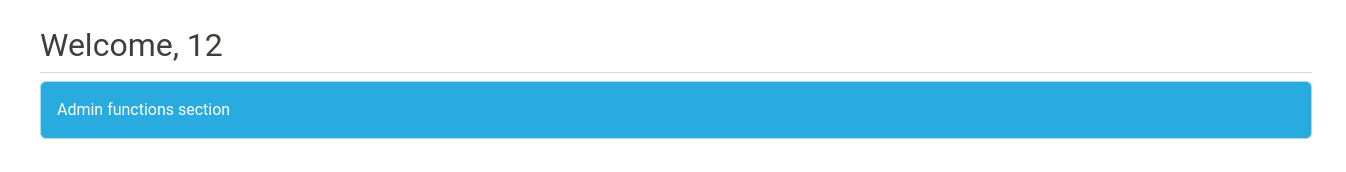
We should once again verify this manually to collect screenshots/evidence and ensure we didn’t make any mistakes before reporting.
Challenge
Finally, we have our challenge to put what we’ve learned today to the test! Good luck!

Conclusion
Through this guide, we’ve demonstrated the incredible potential of BURP Suite Macros in addressing CSRF token challenges and in exploiting mass assignment vulnerabilities. Remember, the key lies in understanding the technologies we’re working with and thinking outside the box. As cybersecurity professionals, continuous learning and adapting is our mantra.

About the Author: Alex Olsen
Alex is a Web Application Security specialist with experience working across multiple sectors, from single-developer applications all the way up to enterprise web apps with tens of millions of users. He enjoys building applications almost as much as breaking them and has spent many years supporting the shift-left movement by teaching developers, infrastructure engineers, architects, and anyone who would listen about cybersecurity. He created many of the web hacking courses in TCM Security Academy, as well as the PJWT and PWPT certifications.
Alex holds a Master’s Degree in Computing, as well as the PNPT, CEH, and OSCP certifications.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

