Overview
TCM Security is proud to share a non-technical look at phishing attacks, the first of a four-part series for Cybersecurity Awareness Month 2023. Each Wednesday during October, we will release a blog post with general best practices for the information worker, followed by a YouTube video on the same topic. Each topic will be combined into a free course at TCM Security Academy called “Practical CyberSecurity Awareness.” Topics covered later this month will be safe browsing, then password management and rounding out the series will be privacy and the dark web.
Today, we start our series on the most pressing issue facing today’s workers: phishing. Did you know that phishing is one of many common social engineering techniques? But what exactly is phishing?
Social Engineering (SE) Tactics
Social engineering (SE) tactics are tools cybercriminals employ to manipulate individuals, effectively ‘hacking humans.’ These tactics span a broad spectrum, from face-to-face attempts to extract private information to those incorporating technical elements. In this post and the subsequent YouTube video, we will delve into four distinct SE tactics:
- Phishing
- Vishing
- Smishing
- Business Email Compromise (BEC)
What is Phishing?
Phishing, one of the most recognizable forms, involves using emails as lures to entice recipients into clicking malicious links or opening harmful attachments. Threat actors employ various strategies to make their emails convincing, often relying on language designed to trigger immediate action, instill a false sense of security, or promise rewards.
How many red flags can you spot in this email? You might be surprised with how many you find!

You may think that no one would ever fall for a simple email like this; however, it happens daily! Even though this email is an obvious trap, what specific aspects make this email suspicious?
Let’s begin with the email’s “Sender line.”

In this case, the sender is John Money, whose email reads as john (at) inheritance (dot) com; you may or may not know John or have had previous correspondences with him in the past. Regardless, you should always check every email’s sender line and consider questions such as:
- Do I know this person?
- Have I received emails from them in the past?
- Why would this person be contacting me?
- Even if I know this person, was I expecting an email with an attachment?
Asking these straightforward questions can help you avoid scams and slow your thinking process so that you think before you click!
Next, we can move on to the body of the email and check it for inconsistencies.
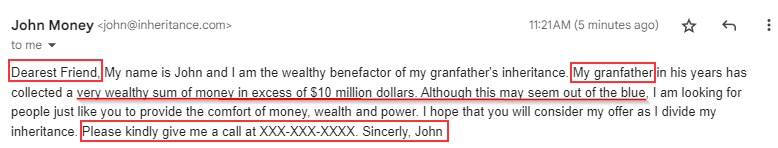
A closer inspection reveals several spelling errors and other red flag indicators. The email opens with the phrase “Dearest Friend,” a clear sign that it’s been sent en masse to various recipients. Instead of addressing you by your name, the threat actor is going for the path of least resistance and calling you “friend.”
If you look closely, the word “grandfather” is misspelled in the first and second sentences, a frequent red flag in phishing emails. Many threat actors now use tools to correct grammar and punctuation, making them more convincing.
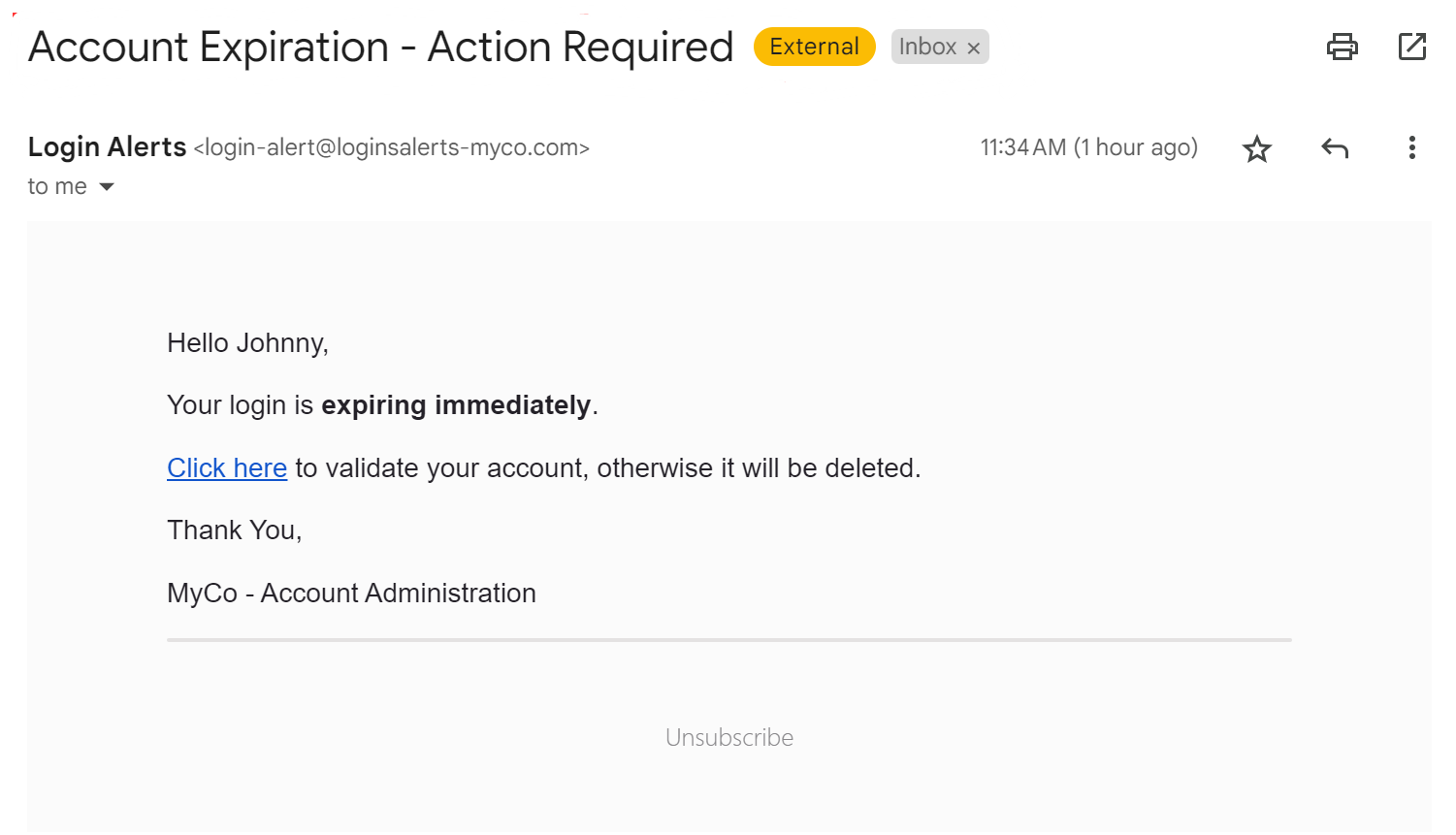
Although this can be a good protection, remember that many systems you utilize regularly send alerts to your end users from outside their organization. Take special care when reading and clicking links in emails from expense report systems, cloud providers, or other platforms your organization utilizes regularly.
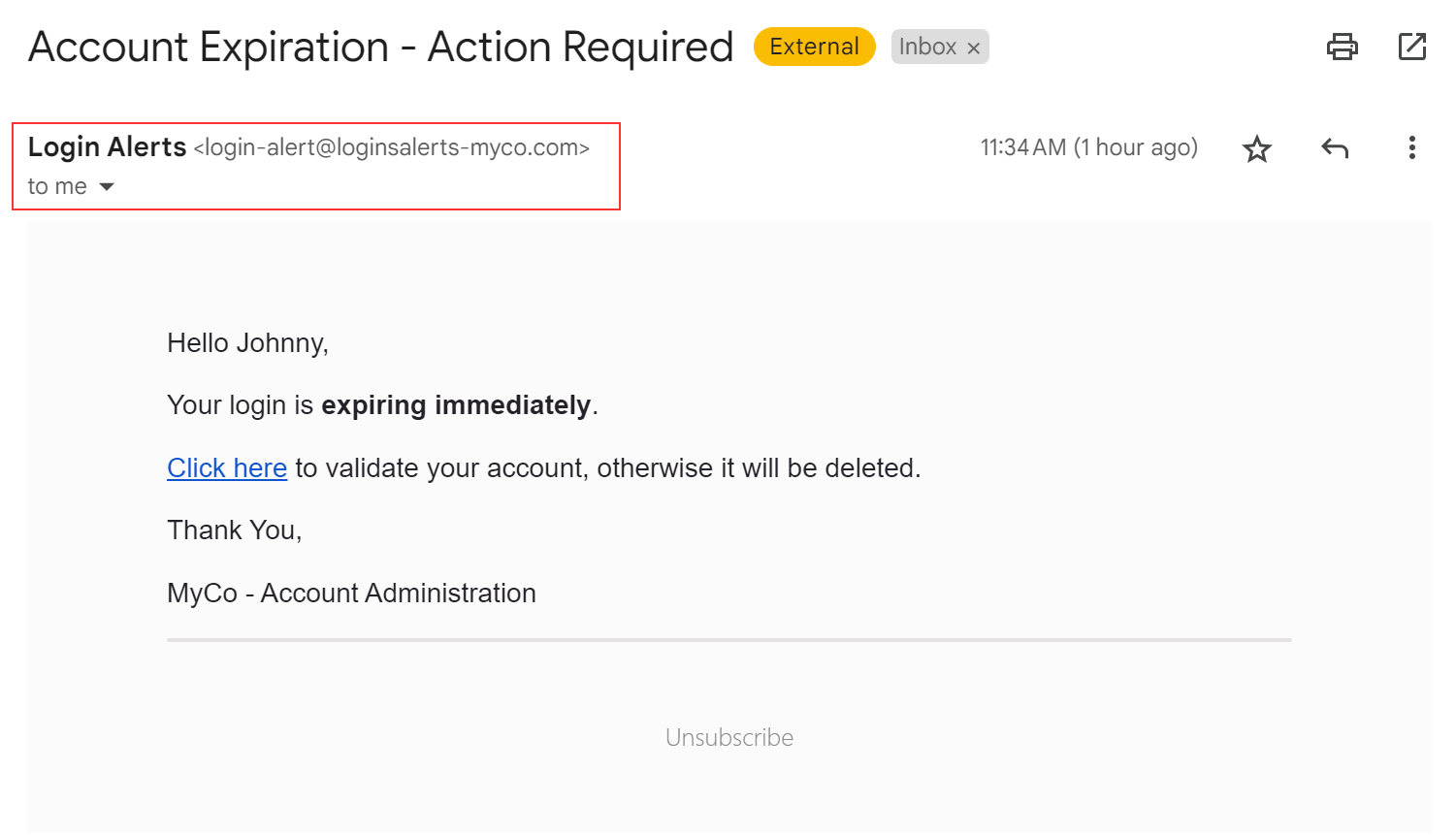
Examining the sender reveals another potential red flag: the email is from a user named ‘Login Alerts,’ a significant cause for concern, especially when it originates from an automated system. In this instance, the domain, loginsalerts-myco.com, contains a misspelling, raising additional suspicions.
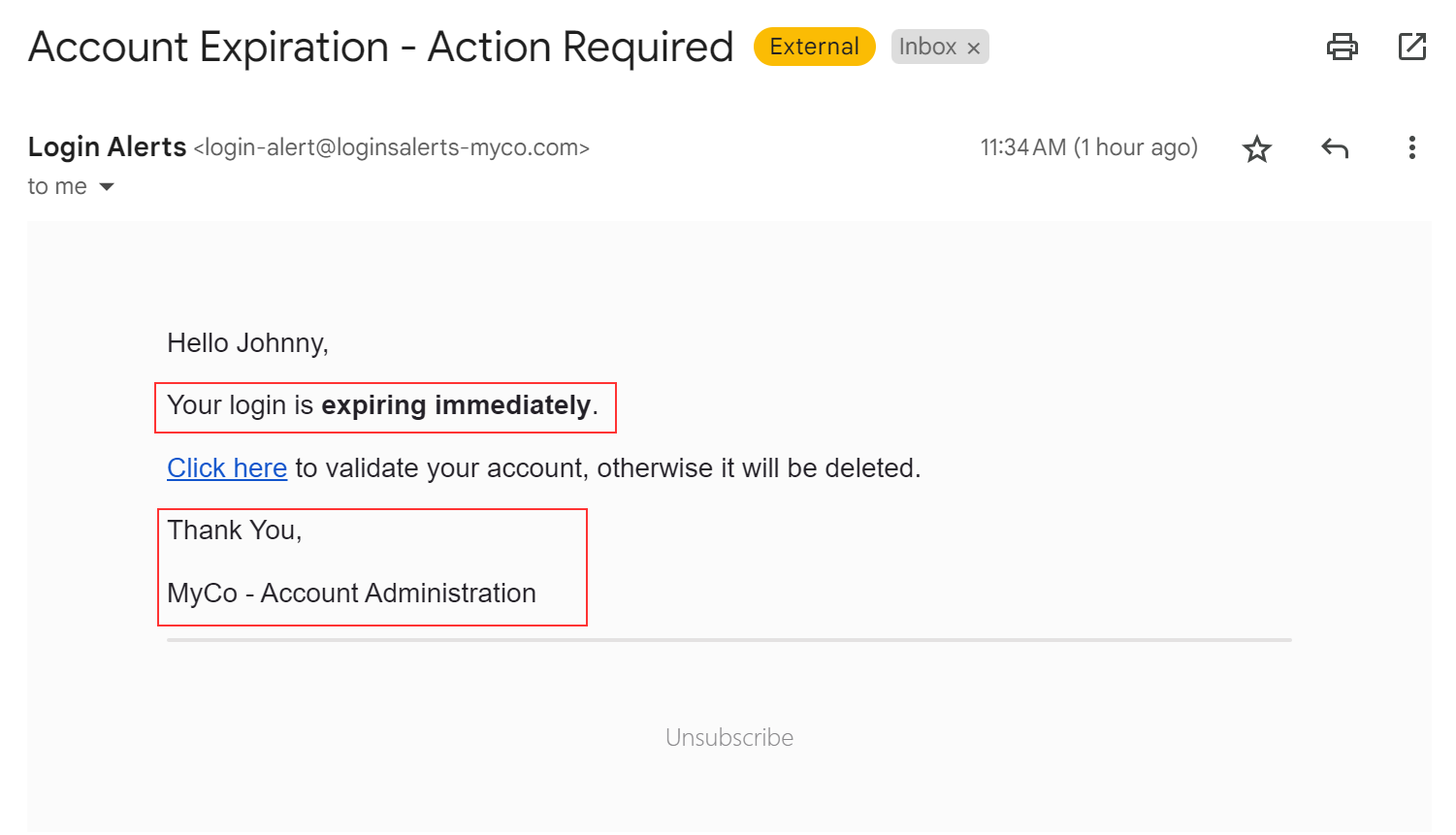
The hook in this email is the urgent claim that your login is expiring immediately, pressuring you to act quickly. This urgency is reinforced by the email’s signature, claiming to be from MyCo – Account Administration.
Always take a moment to evaluate such emails by considering whether they align with your organization’s procedures and ask yourself questions such as:
- Is this a company procedure we use?
- Does this email fall in the timeline of when I need to reset my password?
- Is this what we call the company’s IT department?
To guard against phishing attacks, we recommend these key precautions:
- Never open an email from an unknown sender.
- Avoid opening attachments from untrusted sources, particularly those with .exe extensions.
- Utilize your email provider’s “report spam” or “phish reporter” feature.
- Instead of clicking links within emails, navigate to websites using your web browser or search engine independently.
Next we will discuss vishing.
What is Vishing?
Vishing, or ‘Voice Phishing,’ employs voice and phone communication to social engineer to manipulate victims. Threat actors utilize advanced techniques, including voice changers and AI to mimic familiar voices. They may pose as neighbors, friends, colleagues, CEOs, or other authoritative figures. Additionally, attackers can employ SIM swapping to spoof phone numbers of government agencies, your bank, or other entities, making the attack seem to be coming from a legitimate source.
Despite these intimidating tactics, most vishing attacks share a common trait: the urgency for immediate action. Whether it’s purchasing gift cards, clicking links, or providing information, threat actors demand rapid compliance. To shield yourself against vishing attacks, consider the following strategies:
- Always ask questions before you click, buy, or do something someone asks you to do over the phone. Many scammers will get upset when you ask them to clarify what is happening.
- Avoid answering calls from unrecognized phone numbers.
- Block and report suspicious numbers that are frequently calling you.
- Implement third-party apps like Robokiller, Hiya, or Truecaller to block known spam calls.
- If you reside in the United States, add your phone number to the national do not call registry at https://www.donotcall.gov/.
Next up in social engineering tactics threat actors use is Smishing!
What is Smishing?
Smishing is a social engineering attack that takes place through text messages. These attacks take on various forms, including alerts, delivery notifications, and messages designed to pose as reputable delivery companies, leveraging trust. In some cases, scammers utilize dating websites to build trust and then transition to texting to manipulate users further.
To protect against Smishing attacks, consider these tactics:
- Employ third-party apps like Robokiller, Hiya, or Truecaller to block spam text messages.
- Block and report suspicious individuals who text you.
- Refrain from responding to unsolicited text messages.
The last social engineering tactic is, Business Email Compromise (BEC).
What is Business Email Compromise?
Business Email Compromise (BEC) is where attackers utilize email addresses from within an organization to send phishing campaigns. The threat actor compromises a victim’s account to issue demands to other employees. This has become an increasingly prevalent threat to business across the World.
A story that comes to mind in my career is when a high-level employee was compromised. The compromised employee started to send emails to their secretary asking them to purchase $5,000 of Google Play gift cards. The secretary purchases the gift cards, as the email is from a known and trusted employee, and provides the threat actor with the gift cards. The key lesson here is to always verify urgent requests via communication channels separate from the original email. In this example, a call, text, message, or personal conversation could have averted the situation.
Even when you are receiving emails from people inside of your organization, adhere to these best practices:
- If a request appears urgent or out of character for the individual’s typical behavior, verify it through alternate communication channels.
- Seek clarification on instructions to push back on the attacker.
- Refrain from opening email attachments without first validating is was sent by the individual via out-of-band communication methods.
Conclusion
Awareness is half the battle when it comes to cybersecurity. This series aims to educate and equip all individuals with the knowledge necessary to safeguard themselves regardless of their technical background. This information isn’t just valuable in a business setting; it enhances your personal cybersecurity experience. Together, we can contribute to a safer digital world for all.

About the Author: Aaron Wilson
Aaron is a passionate security professional with experience in the Fortune 50. He is the Red Team Lead at TCM Security, responsible for leading the penetration testing and consulting teams. He is also an avid Capture the Flag Creator and has published multiple rooms on TryHackMe. Aaron is also CEO and Founder of the Wilson Security Group and publishes videos on YouTube on security topics and cybersecurity certification reviews.
Aaron holds certifications such as the eMAPT, CISSP, eCPPTv2, eWAPTv2, CEH, and eJPT certifications among others. He holds a bachelor’s degree in Security and Risk Analysis from Penn State University as well as a Master’s in Information Assurance and Cybersecurity from Western Governor’s University (WGU).
Follow Aaron on Social Media:
LinkedIn – https://www.linkedin.com/in/wilson-security
YouTube – https://www.youtube.com/c/WilsonSecurityGroup
TryHackMe Hacker Methodology – https://tryhackme.com/r/room/hackermethodology
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

