The majority of our internal penetration tests are at least a week long. While we generally have a drop box sent to the client to enable our access to the network, we have to consider efficiency as well. Ensuring persistent access in a network is vital to that efficiency, as well as our ability to move from machine to machine. Today we will show you a few of the ways we ensure persistence when testing internally.
Compromised Credentials
One of the easiest, and most obvious ways that we maintain persistence is through the use of compromised user credentials. These can come from credential breaches, hash cracks, and more. Most recently we have begun using the Rockyou2021 wordlist, which has approximately 8 billion passwords listed. This list, when paired with captured hashes through Responder or ntlmrelayx, has improved our cracking capabilities substantially. Cracked credentials can then be used to then access endpoints as needed. This allows us to leverage those devices or services to dump additional hashes, compromise stored browser credentials, and more.
New User Accounts
We most commonly utilize this technique in circumstances where we have taken over a critical service like the domain controller, or are having difficulty compromising passwords but have exploited a vulnerable service allowing for elevated privileges. This can be used for persistence as well as proof of impact when exploiting vulnerabilities in the wild.
Note that as testers we have a duty to document any time we create new accounts, and to use strong passwords so that we don’t create a user account vulnerability. Additionally, we need to make the effort to clean those accounts up when finished testing, and if unable, notify the client so they can.
Pass the Hash
In circumstances where we are able to obtain uncrackable NTLM hashes through relay attacks or NDTS dumps, we can still use the hash to authenticate. Because Windows allows us to utilize NTLM hashes in the challenge/response process, we can execute a Pass the Hash attack numerous ways. The most common ways we do this is with Evil-WinRM, Impacket tools like PSExec or WMIExec, or XFreeRDP to access remote desktops. Keep in mind that the client’s employees could be using the devices, so try to keep RDP access to as-needed only so as to not disturb business processes.
Click here for information on Microsoft best practices for defending against Pass the Hash attacks.
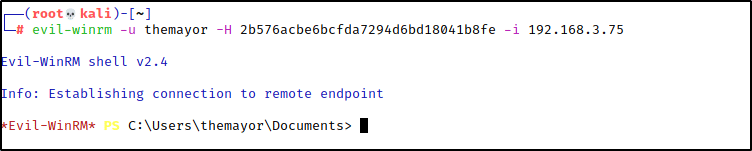
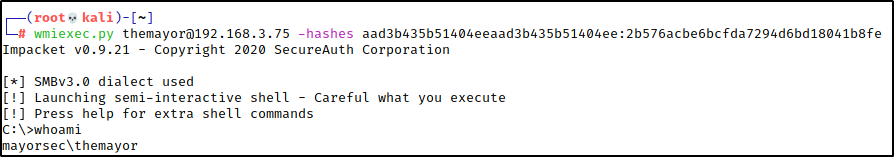
Golden Tickets
We’ve compromised a domain controller but have some more work to do in the domain. One way we can ensure our elevated domain privileges is through a Golden Ticket attack. This attack requires us to dump the krbtgt hash in the domain, and then leverage it to access whichever domain user we need to. We can access the krbtgt hash by dumping the domain NTDS or through a DCSync attack. Using Mimikatz, we can then forge the Golden Ticket and use it to execute commands within the domain as the specified user.
Once you are completed with testing, make sure to clear the klist on the Windows machine you are utilizing so that you don’t leave the ticket in memory.
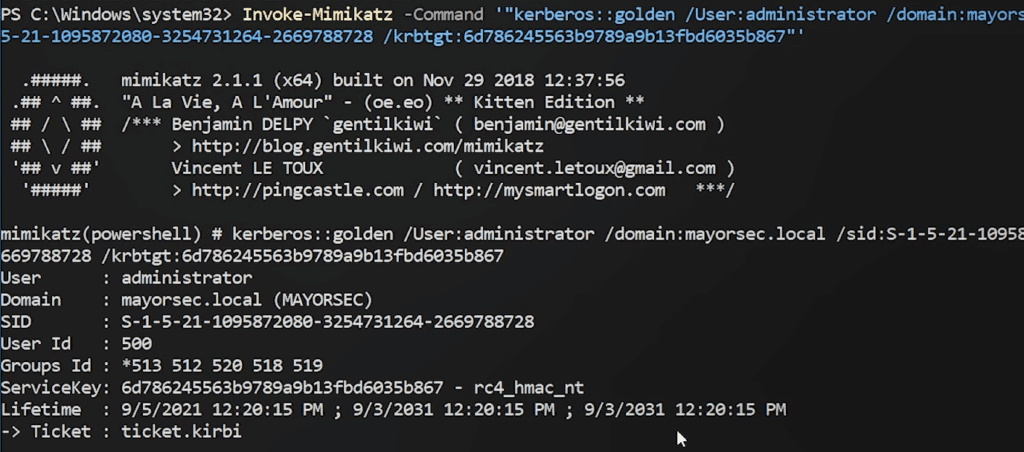
Wrapping Up
These are just a few of the most popular ways we maintain persistence while conducting internal penetration tests. If your organization is concerned about its internal security measures and would like us to test the above techniques and more, please contact us.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com

